The following composite shows the results of a image authentication and evaluation tests performed on images from the Hunter Biden laptop collection. The Biden campaign and various MSM apologists claims that they are fakes. The results of the image analysis beg to differ:
- The two images match Hunter Biden on face recognition within a 98% certainty (using a validated image as the reference)
- The object in Hunter Biden’s mouth matched a glass crack pipe within a 93% certainty
- Both images came back as negative on a wide range of tampering and Deepfake manipulations
Conclusion, these are authentic images within a match probability >90%.
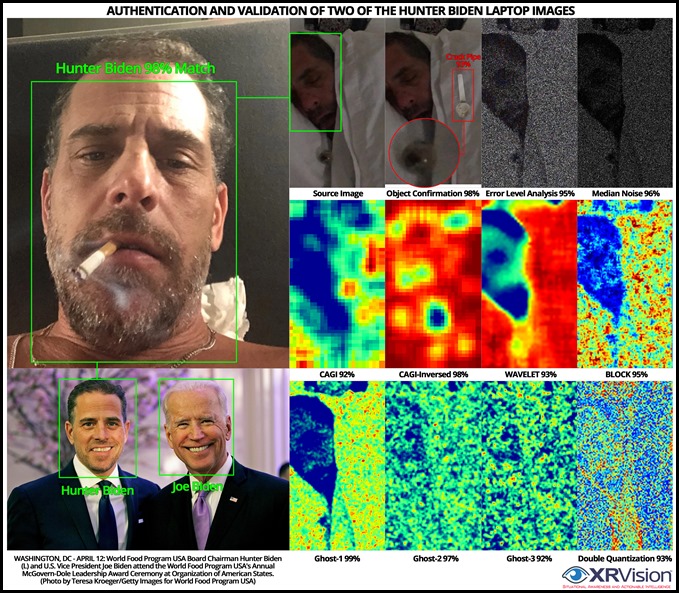
Image 1: Authentication and validation of two images from the ‘Hunter Biden laptop’ collection
If you are not getting the relevance of Vadym Pozharskyi, the top Burisma adviser, emailing Hunter asking for “advice on how you could use your influence,” the following composite may be of some help. Seen below is Vadym Pozharskyi in situ at an Atlantic Council event with former senior state department officials in the Obama administration, including Evelyn Farkas, Ambassador John Herbst, and Ambassador Roman Popadiuk. All hard at work unselfishly promoting the interests of Burisma.
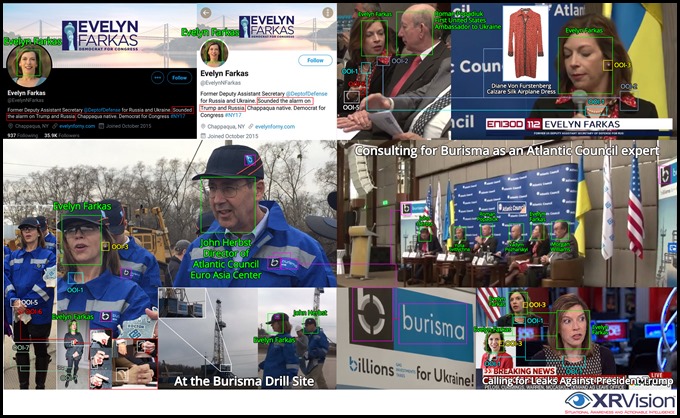
Image 2: How to sell influence like a pro
References
Former IC Officers’ Public Statement about the Hunter Biden Laptop
A sampling of the Tests Performed on Imagery
AI-based face recognition and deepfake detection. I’ve also performed a battery of forensic image analysis tests that included functions such as:
Double Quantization – These types of inconsistencies occur when a foreign object is inserted in a JPEG image. When the new image is saved, the untampered part of the image will have been compressed twice, while the inserted region only once. In this case, the tampered area should appear red while the rest of the image blue. If other colors are present (green, yellow) then no conclusion can be made.
Error Level Analysis – These types of inconsistencies are produced by recompressing the image as a JPEG of quality 75 and subtracting the new image from the old. The resulting image of differences is then enhanced and displayed. Areas of interest are those with higher values than other similar parts of the image. Only similar regions should be compared, i.e., edges should be compared to edges, textures to textures, and uniform regions to uniform regions. Color discrepancies (commonly blue regions) are also generally suspicious.
Median Noise Residuals – These type of inconsistencies are based on isolating the almost-invisible image noise through median filtering. When interpreting the results, areas of interest are those that return higher (i.e. brighter) values than other similar parts of the image. Only similar regions are compared, i.e. edges are compared to edges, textures to textures, and uniform regions to uniform regions.
Compression anomalies 1 – JPEG compression operates in an 8-by-8 grid, which is near-invisible but detectable. Adding or moving an object on an image may locally disrupt this grid. The GRIDS algorithm seeks such discrepancies and highlights them locally. The algorithm produces local red/orange “blobs” where it detects grid discrepancies. Generally, the GRIDS algorithm is less distracted by textures in the image and focuses on grid disturbances.
Compression anomalies 2 – JPEG compression operates in an 8-by-8 grid, which is near-invisible but detectable. Adding or moving an object on an image may locally disrupt this grid. The GRIDS-Inverse algorithm is complementary to GRIDS in seeking such discrepancies. The algorithm produces local blue “blobs” where it detects grid discrepancies. Generally, the GRIDS algorithm is less distracted by textures in the image and focuses on grid disturbances. However, it should mostly be interpreted in combination with other algorithm outputs that highlight the same regions.
Compression anomalies 3 – JPEG compression operates in an 8-by-8 grid, which is near-invisible but detectable. Adding or moving an object on an image may locally disrupt this grid. The BLOCK algorithm detects the image grid and looks for local discrepancies. Any coherent region with a different color to its surroundings may correspond to tampering, although reds and yellows against a blue background are the most typical indication of tampering.
Compression anomalies 4 – The JPEG Ghosts algorithm is based on recompressing the image in multiple different qualities and subtracting each of them from the original. The resulting difference images are post-processed to highlight regions that stand out and are likely to originate from a different JPEG image. Then, the images most likely to contain interesting findings are selected (i.e., those that feature localized inconsistencies). Consistent yellow regions against a blue background may correspond to traces of tampering, especially if they do not correspond to edges but to entire regions.
Noise anomalies – Each image carries invisible, high-frequency noise that is the result of the capturing process as well as the compression. The Discrete Wavelet Noise algorithm filters the image and calculates the local noise distribution at each part of the image. Regions that differ from the rest of the image are highlighted in strong red, and are likely to originate from other images.
Copyright 2020 Yaacov Apelbaum, All Rights Reserved.


So where did these photos come from other than Biden laptop that is in who’s possession? That really was not explained.
This hasn’t been made clear by the media/signers of the declaration of fraud (see links below). Some of the general suggestions floating around are that the documents and images are fakes, but no challenger has provided any specifics such as image X is a deep fake or document Y shows evidence of manipulation.
– Justine Coleman from The Hill is A Manipulative Media Hack
– No Russians Need Apply
Still where did the photos even if not fakes come from anyway? Were they from the shop computer and then released by the post. Has the laptop been confirmed to be Hunters and did all these doc photos come from Hunter computer? Should I assume this group in search came from some other source? https://www.google.com/search?q=Hunter+biden+computer+receipt&rlz=1CAKSOU_enUS909&sxsrf=ALeKk015_bIB8RjtwZQaz5u_iy5r1uTbSQ:1611359270433&source=lnms&tbm=isch&sa=X&ved=2ahUKEwiinK2H3bDuAhVMFjQIHdJbCYsQ_AUoAXoECAYQAw&biw=1366&bih=641 I read the linked stuff. Others argue that none of this came from so-called Hunter shop computer. I believe your forensics per photo but does not look like computer went through FBI forensics. Grand Jury had a number for computer but no conclusion.
My source of the images is the “Hunter Laptop”. The images that you linked to most likely came from the Giuliani copy, which he distributed to the NY Post and Bannon. The Bannon copy eventually made it to G-TV.
The are multiple issues with the identification and commentary about some of the images, for example, some of the statements made by G-TV about the content are inaccurate.
Hunter originally brought in 3 laptops for service. He came back and picked-up two of the laptops. He abandoned the third unit, which became the source of the content in question.
I’m not sure what the FBI did with the laptop, or what the Grand Jury saw or was told about the evidence. On my part, I can certify that what I published is authentic.