So, who Pwned the DNC and Podesta’s emails? The Russians? Romanians? Or was it just your run-of-the-mill developer/sysadmin/staffer with an axe to grind? Here is a little illustration that helps focus some of the data transfer rate arguments and expand on other cyber points:
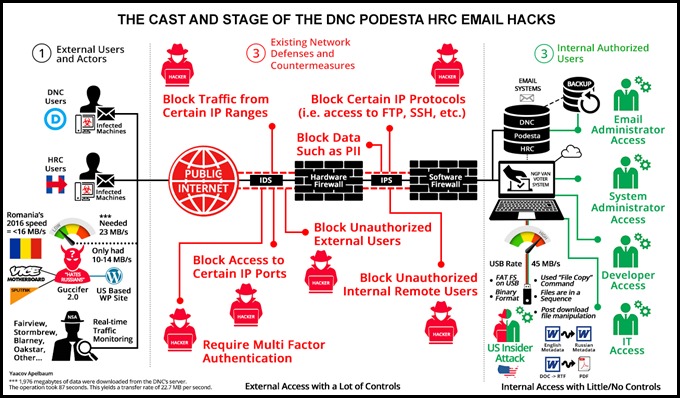
Image 1: The stage and characters of the DNC-Podesta-HFA email hacks
If you are still confused about the who, what, when, where, and how, you are not alone. The reason for this heavy fog is that it’s impossible to separate the spin from facts without access to the forensic data–which, for some reason, doesn’t seem to make itself available. As far as the pro and con arguments for local vs. remote access are concerned, yes. Theoretically, a remote attacker could have used a cocktail of zero-day + remote privilege elevation + password recovery against the DNC network and cloud-based NGP VAN voter system, but so could a local user/administrator at a fraction of the time and effort.
What about the identity of the perpetrator? According to WaPo (using CrowdStrike, the DOJ, and their other usual hush-hush government leakers in the know), the attack was perpetrated by a Russian unit led by Lieutenant Captain Nikolay Kozachek, who allegedly crafted malware called X-Agent and used it to get into the network and install keystroke loggers on several PCs. This allowed them to see what a DNC staffer was typing on the keyboard and take screenshots of their computer. The description of the exploit seems plausible, but if this was the case, how did the DOJ learn all these details and use them in the indictments without the FBI ever forensically evaluating the DNC/HFA computers and servers? And why would the Russian intelligence services use outdated, Ukrainian-made malware for such highly visible exploits? Finally, since when does the DOJ, which only speaks the language of indictments, use hearsay from British nationals like Matt Tait—a former junior GCHQ employee and a connoisseur of all things related to Russian collusion (who, under oath, denied his media claims) or evidence from CrowdStrike (the FBI didn’t perform any computer forensics on the Seth Rich laptops or the DNC hack), or any other evidence lacking chain-of-custody accreditation as a primary source for prosecution?
Another noteworthy observation is that three of the Russian GRU officers on the DOJ wanted list were allegedly working in 2016 concurrently on multiple non-related projects like interfering with the United States elections (and hacking the HFA and DNC), while at the same time, they were also allegedly hacking the United States Anti-Doping Agency (USADA) and the World Anti-Doping Agency (WADA).

Image 2: Overlap of GRU resources working on the DNC/HRC and the Olympic doping projects

Image 3: The very busy (L-R ) Malyshev Artyom Andreevich, Dmitriy Sergeyevich Badin, and Ivan Sergeyevich Yermakov
The three’s multiple (at least 4) concurrent high-impact and high-visibility project assignments are odd because this is not how typical offensive cyber intelligence teams operate. These units tend to be compartmentalized; they are assigned to a specific mission, and the task force stays together for the entire project.
And this riddle wrapped up in an enigma doesn’t stop there; in addition to shoddy cyber forensics from Crowdstrike and the FBI, we also have all of the questionable MSM investigative work that links the attacker to the pseudonym Guccifer 2.0 and identifies him as a Russian.
Any evidence that Guccifer 2.0 is Russian should be evaluated while keeping these points in mind:
- He used a Russian VPN service to cloak his IP address, but he did not use an anonymizer like TOR. Using an anonymizer and proxy to conduct cyber operations is an SOP in all intelligence and LEA agencies.
- He used the AOL email service that captured and forwarded his IP address and the same AOL email to contact various media outlets on the same day of the attack. This is so overt and amateurish that it’s unlikely to be a mistake, and it seems like a deliberate attempt to leave traceable breadcrumbs.
- He named his Office User account Феликс Эдмундович. The full name is assumed to be Фе́ликс Эдму́ндович Дзержи́нский which translates to Felix Edmundovich Dzerzhinsky, after the founder of the Soviet Secret Police. Devices and accounts in offensive cyberspace use random names to prevent tractability and identification. Why anyone in the FSB/GRU/SVR would use this pseudonym (besides the apparent reason) is beyond comprehension.
- He copied the original Trump opposition research document and pasted it into a new template (with an editing time of about 2 minutes). The new document style sheet has different types of fonts, sizes, and configurations, which increases the page count in the new document from 157 to 231 and the file size from 694KB to 5.05MB. He also changes field title to “_Title”, and “Last Modified by” field from “Warren Flood” to “Феликс Эдмундович”. Why waste the time and effort doing this?
- About 4 hours after creating the ‘Russian’ version of the document, he exported it to PDF using LibreOffice 4.2 (in the process, he changed the watermark, lost a date field, and removed about 20 of the original pages). This was most likely done to show additional ‘Russian fingerprints’ in the form of broken hyperlink error messages in Russian (Images 4 and 5). Why bother with re-formatting, re-editing, and converting the source documents? Why not just get the raw data out in the original format ASAP?

Image 4: Parts of the Word and PDF versions of the purported DNC Opposition research document showing the original English template and the pasted version into a Russian template and resulting in subsequent broken hyperlink error messages in Russian.
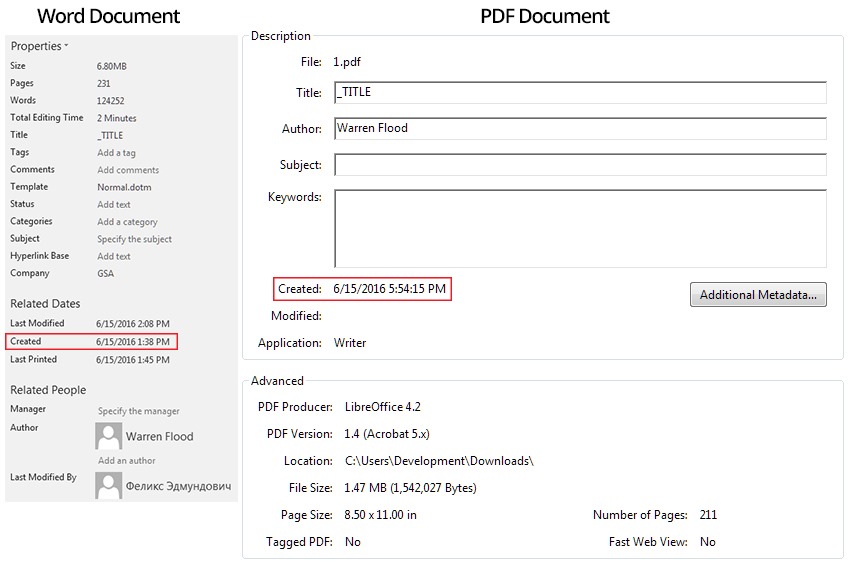 Image 5: L-R Metadata from the purported DNC Opposition research Word document and the PDF version of the same document. Note that what is supposed to be a Russian template document still uses a US date format of mm/dd/yyyy.
Image 5: L-R Metadata from the purported DNC Opposition research Word document and the PDF version of the same document. Note that what is supposed to be a Russian template document still uses a US date format of mm/dd/yyyy.
The likely explanation for all these fancy dance steps in manipulating the document’s language, property fields, and content was an attempt to make it look like the document had been worked on by the Russians. This can be inferred from the following sequence of events:
- The user opens and saves a document (‘source’) called “12192015 Trump Report – for dist-4.docx,” originally composed by Lauren Dillon as an RTF file, and then opens it again.
- The user opens a second document originally generated by User Warren Flood on a computer registered to Company GSA (‘destination’) named “Slate_-_Domestic_-_USDA_-_2008-12-20-3.doc.” He deletes its content, saves the empty file as an RTF, and reopens it.
- The user copies the content of the ‘source’ RTF document and pastes it into the ‘destination’ empty RTF document.
- The user modifies the document’s content, such as changing the watermark from “CONFIDENTIAL DRAFT” to “CONFIDENTIAL.”
- The user saves this document into a file called “1.doc.” This document now contains the text of the original Lauren Dillon “Donald Trump Report,” and it also has Russian language URL link error messages in its body. The user also produces a PDF version of this document.
- A user first publishes “1.doc” to various media outlets, including WaPo, and then uploads a copy to the Guccifer 2.0 WordPress website (which, interestingly, is hosted in the US).
The user name Warren Flood in the metadata most likely refers to Vice President Joe Biden’s former information technology director at the White House (who had a GSA-registered copy of MS Office).
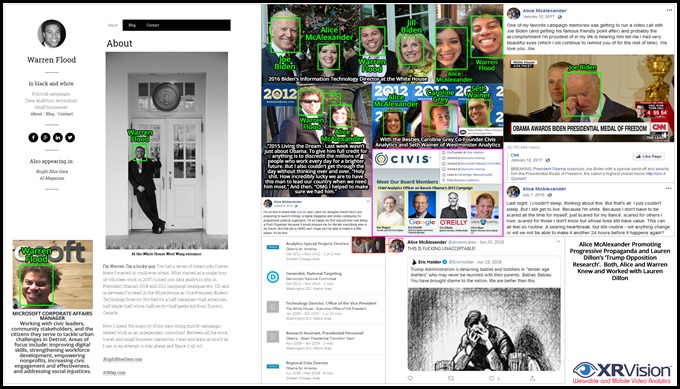
Image 6: Sample linkage for Warren Flood and his wife, Alice McAlexander. In 2016, both worked at the White House, were tied to senior DNC political leadership, published a newspaper for progressive organizers, and produced a large volume of political and strategic democratic content.
Based on evidence that goes beyond the user and company name in the file metadata, it’s clear that Warren and his professional circle of the likes of Tony Carrk, Kristin Sheehy, Sara Latham, and Lauren Dillon had copies/access to these files long before they were leaked on June 14, 2016. Of note is that at least one of these individuals, Sara Latham, John Podesta’s Chief of Staff and HRC’s senior campaign advisor, was also in contact with some British players associated with the Steele Dossier.
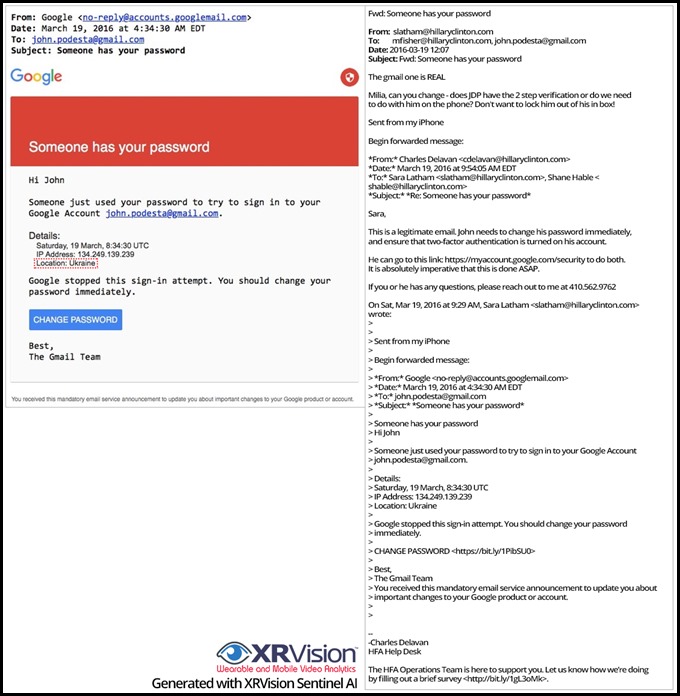
Image 7: The details of Podesta’s alleged email phish and the subsequent emails sent by the Hillary for America (HFA) IT help desk to Sara Latham telling her that Podesta’s password must be reset via a verified Gmail URL (i.e., don’t click on the phish email link) and instructions for enabling 2-factor authentication. Both actions were taken, challenging the claim that the phishing was successful. Despite this, Lorenzo Franceschi-Bicchierai, the reporter who also just happened to interview Cuccifer 2.0, wrote on October 28 a damage control piece in Vice Motherboard (it followed an almost identical piece published by Tara Golshan from Vox 11 minutes earlier) claiming that the HFA IT help desk believed that the phish was a legitimate email.
Guccifer 2.0
On June 21, 2016, a week after the DNC leak went public, Lorenzo Franceschi-Bicchierai, a Vice Motherboard reporter, interviewed a person who identified himself as “Guccifer 2.0.” During their online chat session, the individual claimed that he was Romanian. His alleged poor Romanian language skills were later used to unmask his Russian identity.
Guccifer’s use of contraction like “can’t”, and “couldn’t “ and definite/indefinite articles like “a” and “the” suggests that he is in fact a native English speaker. This also applies to his technical vocabulary and phrasing. Regardless of how bad Guccifer 2.0’s Romanian might appear, the truth is that we don’t know who Bicchierai was texting, if the conversation was a hoax, or if it was staged. The fact that Bicchierai shows up in every critical junction involving the DNC email hack and has first-hand/insider knowledge about what allegedly transpired is suspicious, to say the least.
None of these trivial questions stopped a slew of mainstream media (MSM) publications from claiming that Guccifer 2.0 was the DNC hacker and that he was Russian. One such pseudo-scientific study, published by NYT, claimed that:
“… a linguistic analysis provided to The New York Times by Shlomo Argamon, a chief scientist at Taia Global, a cybersecurity firm… also concluded that Guccifer 2 is Russian.” … Mr. Argamon, who is a professor of computer science and the director of the master of data science program at the Illinois Institute of Technology, found seven oddities in the hacker’s English text, five of which pointed clearly to Russian as the speaker’s native tongue.” Argamon then concludes that: “It is possible that the writer is a Romanian speaker who has studied Russian. However, the writer denied knowing any Russian, and so the most reasonable conclusion is that he is a Russian native speaker rather than a Romanian native speaker.”
Just like with any other forms of misinformation, this piece, too, is laced with partial truths and inaccuracies. If you read the actual text of the online chat, Guccifer 2.0 never “denied knowing any Russian.” he said, “Just a moment, I’ll look in Google Translate what u meant.” Not that this makes much of a difference. Both the study and the NYT article’s pretentious assertions read as if they were written by the team behind the Kid Snippets episode of the “Salesman.”
I’m not a scientific linguist, nor do I even know where to find one if my life depended on it, but I’m certain (based on the fact that I speak two languages natively) that you can’t reliably determine nationality based on someone impersonating another language or from the use of fake metadata in files. This elaborate theory also has the obvious flaw of assuming that the Russian intelligence services are dumb enough to show up to an interview posing as Romanians without actually being able to read and write fluent Romanian.
As far as the ‘actual’ attack details are concerned, in his interview with Vice Motherboard, Guccifer 2.0 was very specific about his exploit, claiming that:
“I used 0-day exploit of NGP VAN soft then I installed shell-code into the DNC server. it allowed me to intrude into DNC network. They have Windows-based domain architecture. then I installed my Trojans on several PCs. I had to go from one PC to another every week so Crowdstrike couldn’t catch me for a long time. I know that they have cool intrusion detection system. But my heuristic algorithms are better.”
For Guccifer 2.0 to develop/purchase a zero-day for the cloud-based NGP VAN system, he had to either have access to the source code or the runtime. NGP VAN is not publicly available, so where did he get the initial copy (before breaching it)? And if there was a zero-day exploit, what is it? He also only discusses high-level post-exploit actions like installing shell code and Trojans. What is ostensibly missing are the low-level details and pride of authorship.
And what is the relevance/relationship between the cloud-hosted NGP VAN exploit, the attack against the individual workstations (which were running on a local area network), and the MS Exchange email system? The general impression is that Guccifer 2.0 is not a coder.
The purpose of this whole interview is also puzzling, instead of factually discussing the lifecycle of the exploit, he spends a lot of time boasting about fluffy things like being a ladies man (or alternatively a lesbian) and his interest in expensive Italian fashion.
”I’m a hacker, manager, philosopher, women lover. I also like Gucci.”

Image 8: Guccifer 2.0 is a woman lover and a Gucci connoisseur – Source Gucci Ready to Wear for man
The line stating, ” They [Crowdstrike] have cool intrusion detection systems. But my heuristic algorithms are better,” strongly suggests that the conversation was staged.
It is unlikely that an intelligence organization would disclose a vulnerability in Crowedstrike’s Falcon product—for no other reason than bragging rights–and boast about its ability to evade it. Finally, his assertions that he installed the shell code on the DNC server, gained access to the internal network, placed Trojans on several PCs, and subsequently re-visited these PCs for several weeks could have also been easily verified. Each server/PC/laptop/endpoint he accessed had logs that captured some of these alleged actions.
Even if they didn’t capture all of his nefarious traffic, they would still show some activity, such as PowerShell usage, logins, and application/process and registry changes. So why aren’t we seeing Crowdstrike’s SIEM dump of the DNC and HFA projects?
A Ukrainian Fairy Tale
There seems to be a lot of confusion about Crowdstrike’s confirmation that the same Russian team responsible for the DNC hack also hacked some Ukrainian artillery Android apps. This story has been repeated so many times that it has all but become a statement of fact.
The widespread acceptance of this claim is based on a report and several articles that appeared around December 2016, which connect the DNC email leaks to several alleged Russian intelligence cyber-attacks. This media blitz was a coordinated effort by Dmitri Alperovitch, the CTO of Crowdstrik, and several major news outlets like Reuters, AP, and NYT.
On December 22, 2016, Alperovitch told The Washington Post:
“The fact that they would be tracking and helping the Russian military kill Ukrainian army personnel in eastern Ukraine and also intervening in the US election is quite chilling,”
On December 22, 2016, Alperovitch told the PBS NewsHour:
“And when you think about, well, who would be interested in targeting Ukraine artillerymen in eastern Ukraine?” suggesting again that Russians were responsible.
On December 26, 2016, Alperovich told Forbes:
“It’s pretty high confidence that Fancy Bear had to be in touch with the Russian military,” “This is exactly what the mission is of the GRU.”
Some of the specific claims that Crowdstrike made and the media dutifully parroted were:
- The Russians hacked a Ukrainian artillery app and used it to collect data and unit position information.
- The Ukrainians lost 80% of their D-30 Howitzer field artillery pieces.
- Ukraine’s D-30 Howitzers suffered the highest percentage of loss of any artillery pieces in Ukraine’s arsenal.
Crowdstrike based its figures for the “excessive losses” of Ukrainian artillery units on statistics from the International Institute for Strategic Studies (IISS). However, IISS said that its figures completely disagree with Crowdstrike‘s claims. There were no “excessive losses” of Ukrainian artillery. The IISS told Voice of America that Crowdstrike had erroneously used their data to prove such an intrusion and that the IISS has disavowed any connection to the Crowdstrike report.
The same applies to the claim that the Russian malware could “retrieve communications” and “some location data” from the infected devices, which is blatantly false. Just like with the “DNC hack,” Crowdstrike made up the whole story, and no one in the media or the DOJ challenged them or asked for solid evidence.
The Details of the Alleged Russian Attack
Between 2014-2016, Ukrainian developers by the name of Sherstuk, Dobronravin, and Dmytro provided the Ukraine military through direct channels and an NGO named Army SOS with an artillery targeting solution called Попр-Д30 (Popr D-30) and a digital navigation package. Version 1.0 of the navigation solution was distributed on an Android tablet, and the targeting app came on an Android smartphone.
Version 2.0 of the mapping solution expanded the app’s features to include an add-on called the NetworkBridge that allowed one operator to connect to other operators via a digital radio (Motorola XPR) to allow different units to exchange voice and text messages. It’s important to note that the tablet mapping devices had no GPS tracking capabilities; they were strictly off-line and could only communicate point-to-point via the Motorola radio. GPS coordinates for the targeting app were collected separately using Garmin handheld GPS devices.

Image 9: Typical COTS hand-held GPS devices used by the Ukrainian Army.

Image 10: The Ukrainian targeting solution app “Popr D-30” on the Android phone and the mapping app on a tablet.

Image 11: The Ukrainians mapping app, the Android tablet and radio setup, and the devices in field use.
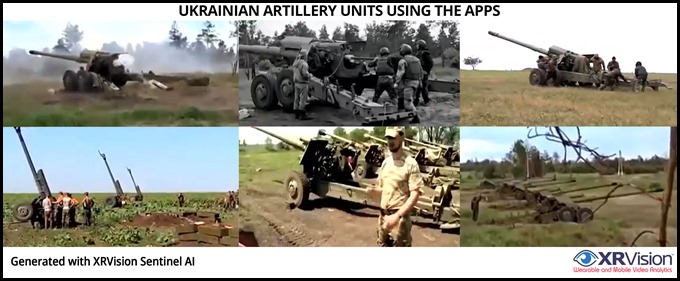
Image 12: Some of the Ukrainian Howitzer batteries use both applications.
On August 27, 2015, Dmytro’s email contacts received a suspicious phishing email impersonating him. The email instructed the recipient to download the latest version of NetworkBridge. Allegedly—and we don’t know this fact—the modified add-on in the phishing email could intercept text messages from the device and upload them to a remote server.
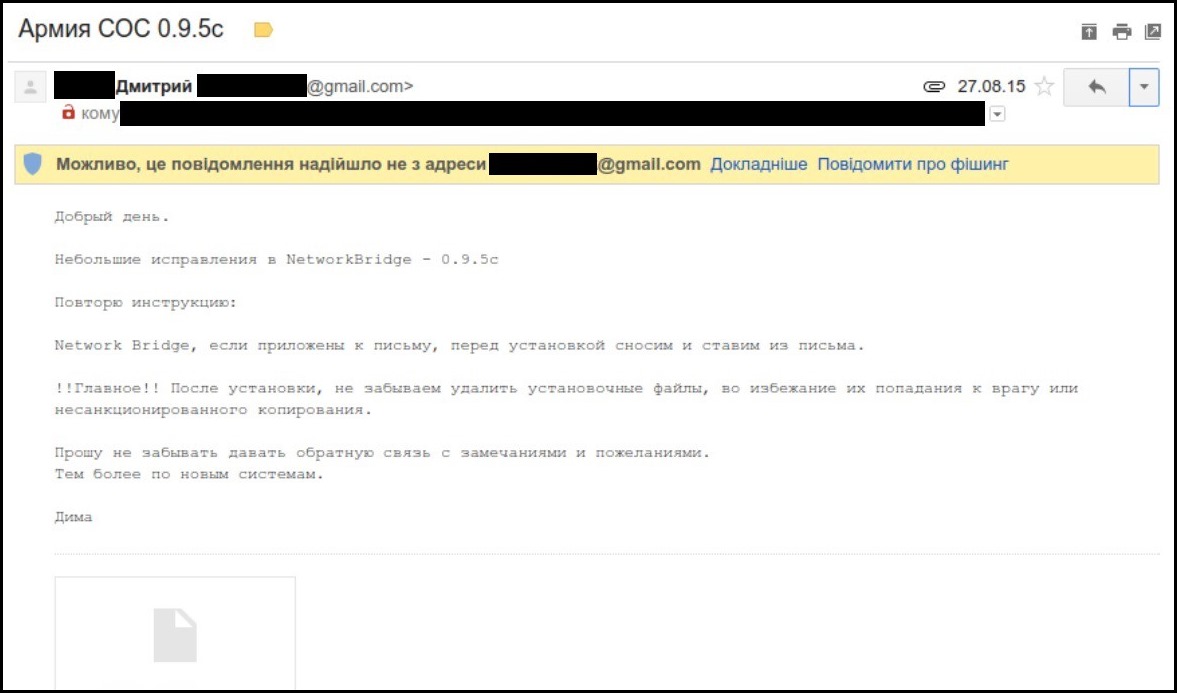 Image 13: The phishing email impersonating Dmytro’s (note the Gmail security warning that the email likely contains malware).
Image 13: The phishing email impersonating Dmytro’s (note the Gmail security warning that the email likely contains malware).
Dmytro immediately told his users not to download the malicious add-on. He sent a copy of the phishing email for analysis to a friend, Andriy Baranovych, a Ukrainian hacker who goes by the alias “Sean Townsend.” AKA “Ross Hatfield” is a leader in the Ukrainian hacktivist group “RUH8.” According to Dobronravin and Dmytro, none of their users downloaded the malware because Gmail flagged it suspicious.
Baranovych, who contracted for Ukrainian intelligence (FSU) and did some work for Alexandra Chalupa/DNC, also just happened to know Dmitri Alperovitch, the CTO of Crowdstrike, and forwarded the code/story to Alperovitch.
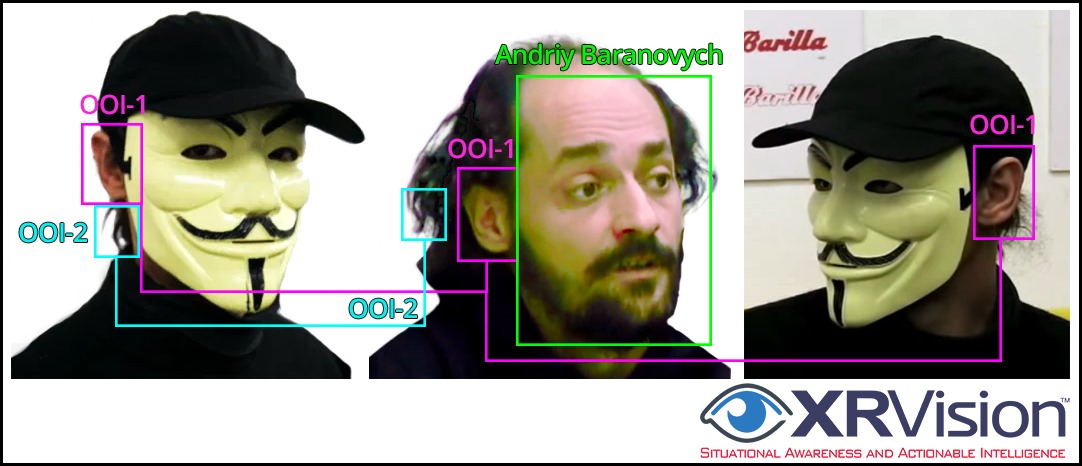 Image 14: (L-R) The Ukrainian hacker Andriy Baranovych, AKA ‘Sean Townsend.’ One of Chalupa’s hackers.
Image 14: (L-R) The Ukrainian hacker Andriy Baranovych, AKA ‘Sean Townsend.’ One of Chalupa’s hackers.
So this is how the fairy tale about the Russian malware in the artillery software hack got out. Alperovitch from Crowdstrike then set on the information he got from Andriy Baranovych for about 16 months (the phishing email date is August 27, 2015). Crowdstrike only went public with this information in December 2016 as the Russian collusion conspiracy was simmering. As soon as the story started gaining traction, Alperovitch jumped on the opportunity to reinforce the alleged Russian role in the DNC hack by showing the same alleged APT 28-29 sources, methods, and pattern of attack in Ukraine.
On December 22, 2016, Ellen Nakashima from the WaPo published another article that promoted the Crowdstrike Russian artillery hack narrative. It’s probably not a coincidence that Nakashima (who has several three-letter agency executives on her speed dial) is the same reporter who, six months earlier, also pimped the Crowdstrike Russia DNC hack story.
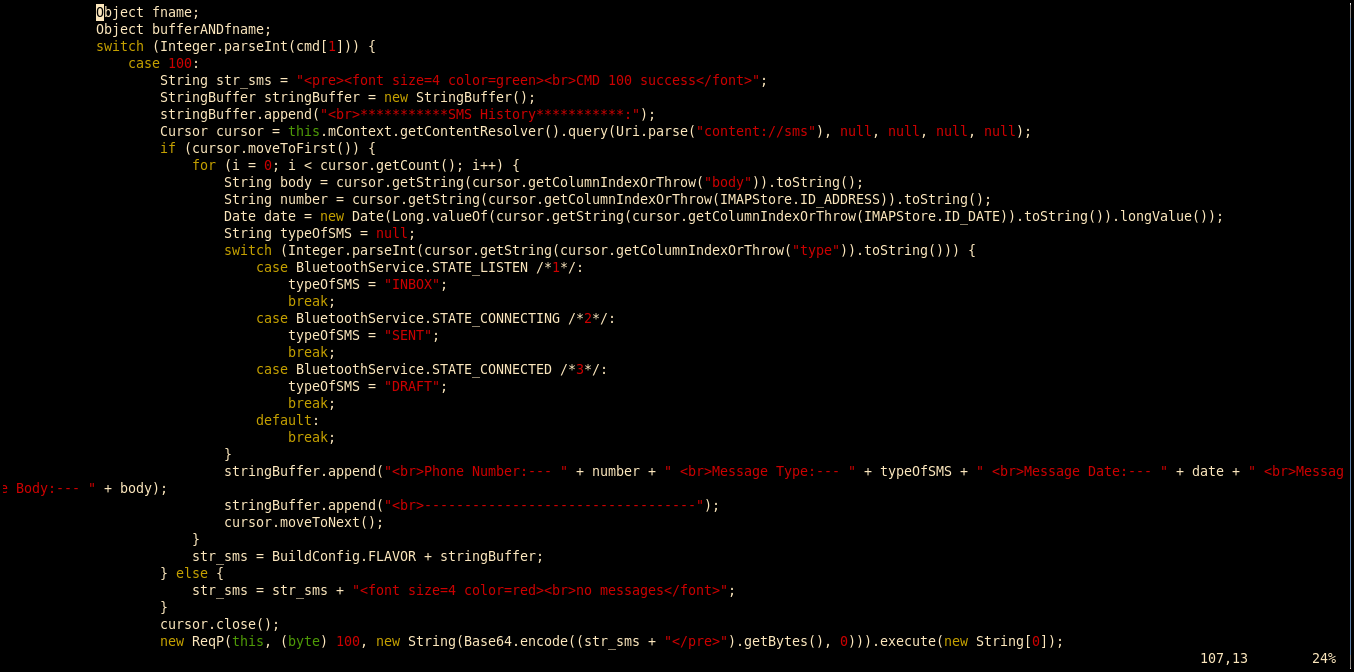 Image 15: Some of the source code of the malicious add-in Dmytro sent to Sean Townsend for evaluation
Image 15: Some of the source code of the malicious add-in Dmytro sent to Sean Townsend for evaluation
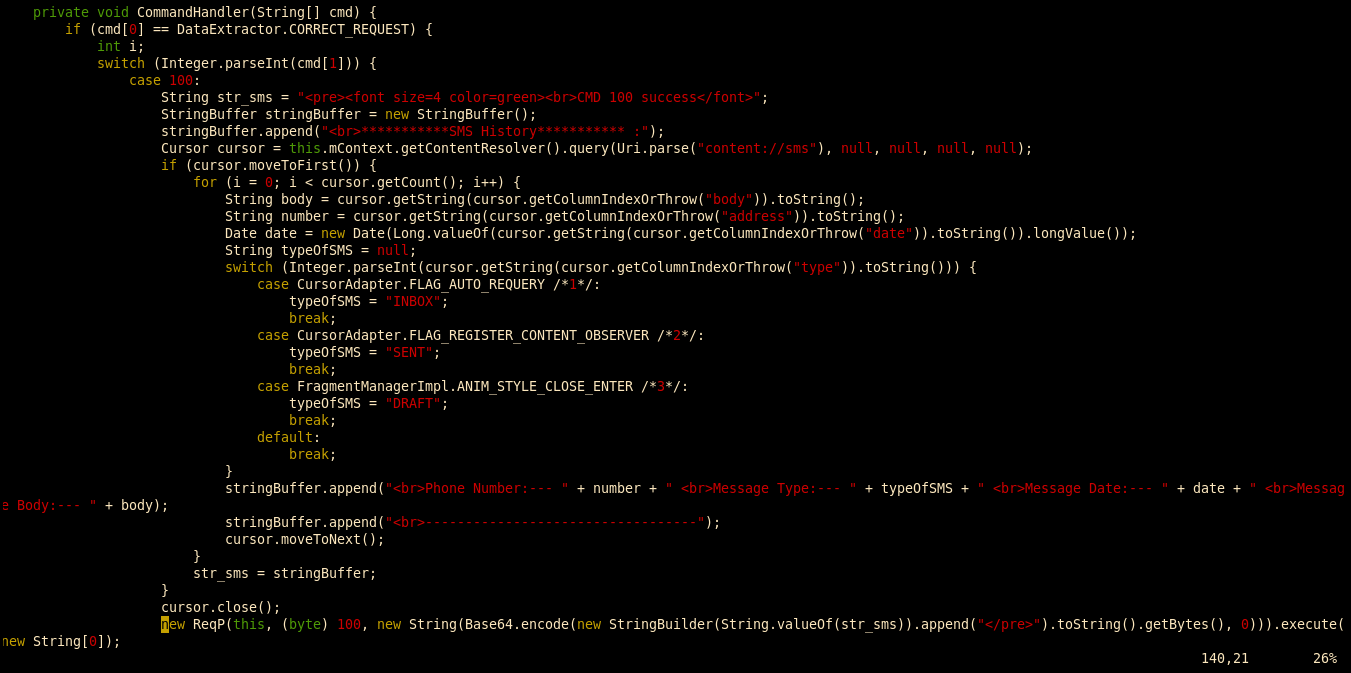 Image 16: Some of the alleged malicious add-in source code published by Crowdstrike in 2016
Image 16: Some of the alleged malicious add-in source code published by Crowdstrike in 2016
Based on the code review of the alleged malware, it’s clear that Crowdstrike entirely made up the whole story about the Ukrainian Howitzer artillery losses and the statement that the rogue artillery RadioBridge add-on was to blame. The simple fact is that even if this malware was downloaded and deployed successfully, all of the tablets and smartphones in the field were offline devices without a functioning GPS. Whoever wrote the code (and it’s not entirely clear that this is not a Ukrainian forgery) incorrectly assumed that the devices would be using Bluetooth, have an active GPS, be networked, and have access to the Internet.
Conclusion
In terms of the big picture, it is possible that whoever added the Russian fingerprint to the documents did this to lay the groundwork for future FISA unmasking. We know that in June 2016 the Obama administration (via people like Susan Rice and Samantha Power) started unmasking Trump campaign officials on the pretext of a ‘Russian interference’. This June 2016 activity also overlaps with the dates of the Guccifer 2.0 saga. So, it is possible that Guccifer 2.0 and MSM outlets like NYT, who promoted him, were part of a larger campaign to affirm Russian involvement in the DNC hacks. If this is indeed the case, then it means that the DNC email leak could implicate Crowdstrike, Ukrainian hackers like RUH8, and Obama administration/DNC officials who manipulated or provided these documents to the perpetrator of the Guccifer 2.0 hoax. This argument is further supported by the fact that the Mueller investigation relied entirely on the Crowdstrike and that the FBI didn’t perform computer forensics.
The bottom line is that in every instance where we can evaluate Crowdstrike’s and Matt Tait’s claims/conclusions, they come back as wrong or deceitful. It all amounts to a lot of political PR and little verifiable forensics. So, if we want to go beyond the speculative trivia, the pseudo-science, and the bombastic unverified MSM claims, we have to ask the real tough questions, mainly:
- Why wasn’t Crowdstrike held accountable for creating the false story about the Ukrainian artillery app/DNC hacks?
- Why were reporters like WaPo’s Ellen Nakashima complicit in propagating false information and failing to correct their reporting even after they knew that what the DNC and Crowdstrike told them was false?
- Who were the ‘anonymous’ hackers who reported their exploits to Alexandra Chalupa on election day, November 8, 2016?
- Is Guccifer 2.0 even a real hacker, or is he just the alter ego or a collaborator working as/with/for Lorenzo Franceschi-Bicchierai, Chalupa, Podesta, the DNC, or the HFA campaign?
- How did Guccifer 2.0 circumvent the security and system logs during several weeks of repeated visits to the DNC network while downloading close to 2 GB of data?
- Why is this entire operation riddled with so many amateurish mistakes?
- Why haven’t the judges handling the Russian collusion/FISA applications (and the Page, Stone, and Flynn cases) asked to see hard evidence from the IC/DOJ/FBI regarding the Crowdstrike claims?
- Who authorized Sara Latham and Kristin Sheehy, both Obama transition team employees, to send Warren Flood’s “Confidential” government communications regarding USDA personnel to Podesta’s unsecured Gmail account?
- Considering the strong possibility that Guccifer doesn’t exist, who collated the documents leaked on June 14th? How did they get these documents from Podesta on/before June 14th, 2016, when WikiLeaks only started publishing them on October 7th, 2016?
- Why were TSG and Gawker selected as the recipients of the pre-leaked version of the documents?
- If Guccifer 2.0 hates Russia so much (“I don’t like Russians and their foreign policy.”), then why reach out to Cassandra Fairbanks, who, while supporting Sanders, also worked for Sputnik, churning out dozens of pure Russian propaganda pieces? Why not just go to the NYT or WaPo instead?
- Why would the Russians leak the most damaging document to Trump, the opposition research titled “Donald Trump Report,” if they are trying to get him elected?
In its July 26, 2016 letter to James Comey (FBI Dir.) and Loretta Lynch (Atty. General), the Senate Committee on the Judiciary called the leak a “pernicious crime”. In the same letter, it demanded a response to the question, “Has the FBI deployed its Cyber Action Team to determine who hacked the DNC?”. In this vein, why haven’t the Feds deployed a cyber response team or investigated all leak-related individuals like DNC staff, Podesta and his people, the WaPo reporter that broke the story, etc.?
Why haven’t the Feds seized the US-based WordPress server and its logs to identify the site’s administrator, the sources of uploads, and the payment method used for hosting it?
Based on some SIGINT and a black box evaluation of Crowdstrike’s evidence vs. claims, it is obvious that their ‘investigation’ was an influence operation, with none of the claims having any factual basis. These include:
- A broken timeline of incident response, investigation, and report
- False information about the DNC breach date, size, and scope
- The political affiliation with the DNC
- Their connection to individuals like Andriy Baranovych and organizations like the cyber alliances and “RUH8”
- Their leadership team came from the FBI, and they communicated with the FBI brass via back channels throughout the project.
- Their deep connection with the Atlantic Council Eurasian division (which includes the leading Russian collusion architects like Evelyn Farkas and David Kramer)
- Their ability to on-demand activate news outlets like NYT, CNN, Slate, and WaPo
Finally, their September 2016 use of the alias “Tea Leaves” to spread the false story that the Russian Alfa Bank server provided a covert communication link between the Trump Organization and the Kremlin also fits into the same MO of political technobabble disinformation. It also servers as a proof that the FBI either doesn’t have have real cyber security capabilities (as they could have easily debunked the Alfa bank white paper), or was acting as an enabler. The fact that Sussmann was using his non-expiring DOJ badge when visiting the FBI suggests the latter.
In lieu of answering these pesky questions, we are left with the only remaining explanation that uses the following formula for predicting cyber attack origins: “Path of Least Resistance”+ “Principle of Least Effort” + “Opportunity” + “Motive” = “Insider,” AKA one of them green guys on the right side of Image 1.
References, Sources, and Credits
A Leak or a Hack? A Forum on the VIPS Memo
The Forensicator – Adam Carter, Elizabeth Vos, and David Blake
GRIZZLY STEPPE – Russian 2016 Malicious Cyber Activity
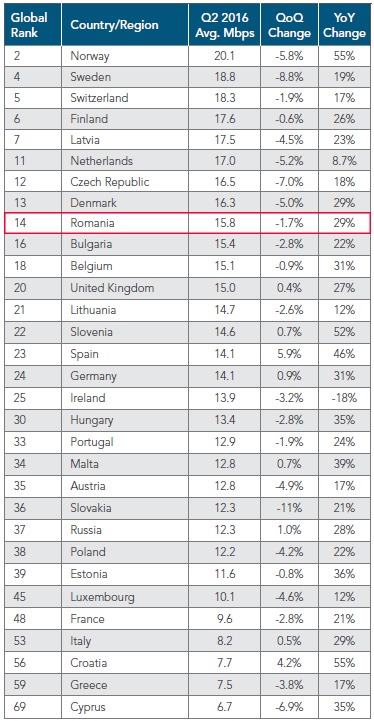
Figure 1: Average Connection Speed by European Country from page 34 in the Akamai’s Q2 2016 report
 Image 17: Guccifer 2.0 use of AOL email
Image 17: Guccifer 2.0 use of AOL email
Transcript of the Jun 21, 201 Vice Motherboard Interview With ‘Guccifer 2.0’
[Motherboard:] So, first of all, what can you tell me about yourself? Who are you?
[Guccifer 2.0:] i’m a hacker, manager, philosopher, women lover. I also like Gucci! I bring the light to people. I’m a freedom fighter! So u can choose what u like!
[Motherboard:] And where are you from?
[Guccifer 2.0:] From Romania.
[Motherboard:] Do you work with Russia or the Russian government?
[Guccifer 2.0:] No because I don’t like Russians and their foreign policy. I hate being attributed to Russia.
[Motherboard:] Why?
[Guccifer 2.0:] I’ve already told! Also I made a big deal, why you glorify them?
[Motherboard:] Tell me about the DNC hack. How did you get in?
[Guccifer 2.0:] I hacked that server through the NGP VAN soft, if u understand what I’m talking about.
[Motherboard:] So that was your entry point; what happened next?
[Guccifer 2.0:] I used 0-day exploit of NGP VAN soft then I installed shell-code into the DNC server. it allowed me to intrude into DNC network. They have Windows-based domain architecture. then I installed my Trojans on several PCs. I had to go from one PC to another every week so Crowdstrike couldn’t catch me for a long time. I know that they have cool intrusion detection system. But my heuristic algorithms are better.
[Motherboard:] When did you first hack them?
[Guccifer 2.0:] Last summer.
[Motherboard:] And when did you get kicked out?
[Guccifer 2.0:] June 12, when they rebooted their system.
[Motherboard:] And why did you hack the DNC in the first place?
[Guccifer 2.0:] DNC isn’t my first deal.
[Motherboard:] Who else have you hacked?
[Guccifer 2.0:] Follow my blog and u’ll know! I can’t tell u now about all my deals. My safety depends on it.
[Motherboard:] OK, I understand. But why did u target DNC? why are you interested in them?
[Guccifer 2.0:] Lazar began this deal and I follow him! I think we must fight for freedom of minds, fight for the world without Illuminati
[Motherboard:] Lazar?
[Guccifer 2.0:] Marcel Lazăr [The original Gufficer]
[Motherboard:] Ah yeah of course. Did you know him personally?
[Guccifer 2.0:] I can’t answer cause I care for Marcel.
[Motherboard:] Ai vrea să vorbească în română pentru un pic? [You want to talk for a bit in Romanian?]
[Guccifer 2.0:] Vorbiți limbă română? [Speak Romanian?]
[Motherboard:] Putin. Poți să-mi spui despre hack în română? cum ai făcut-o? [A little. Can you tell me about hack in Romanian? How did you do it?]
[Motherboard:] Or u just use Google translate?
[Motherboard:] Poți să răspunzi la întrebarea mea? [Can you answer my question?]
Guccifer 2.0: V-am spus deja. încercați să-mi verifica? [I have already said. try to check?]
Guccifer 2.0: Da [Yes]
Guccifer 2.0: Nu vreau să-mi pierd timpul [I do not want to waste my time]
[Motherboard:] De ce ai pus metadate rusă în primul lot de documente? [Why did you put Russian metadata in the first batch of documents?]
Guccifer 2.0: Este filigranul meu [It is my watermark]
[Motherboard:] De ce nu l-ai pus pe documentele de azi? [Why didn’t you put it in the documents today?]
Guccifer 2.0: Puteți găsi de asemenea alte filigrane în limbă spaniolă. Caută mai bine. [You can also find other watermarks in Spanish. Look better]
[Motherboard:] Sunt confuz de ceea ce spui, filigran, pentru că este mereu în schimbare. Pot să vă rog să-mi explicați în propria ta limba maternă? Așa că este mult mai clar. [I’m confused by what you say, why is watermark changing? Can you please explain to me in your own language? So it is more clear.]
[Guccifer 2.0:] Oare nu știți ce este filigran? [You do not know what watermark?]
[Motherboard:] Eu fac. Dar eu nu înțeleg de ce ai folosit filigrane rusești în unele Docs și nu în altele [I do. But I do not understand why you use watermarks in Russian in some documents and not in others?]
[Guccifer 2.0:] îți voi arăta [I will show you]
[Motherboard:] Please do.
[Motherboard:] De ce faci toate astea? [Why are you doing this?]
[Guccifer 2.0:] Asta e din partea următoare [That’s the next]
[Motherboard:] What?
[Guccifer 2.0:] Am spus deja, e un filigran, un semn special [I have already said, it’s a watermark, a special sign]
[Motherboard:] Do you like Trump?
[Guccifer 2.0:] I don’t care at all
[Motherboard:] кто-то говорит мне, что ты румынская полна ошибок [Someone tells me that your Romanian is full of mistakes.]
[Guccifer 2.0:] What’s this? Is it russian?
[Motherboard:] You don’t understand it?
[Guccifer 2.0:] R u kidding? Just a moment I’ll look in google translate what u meant. “Someone tells me that you are full of mistakes Romanian.”
[Motherboard:] Hai sa-ti pun cateva intrebari, ca sa vad ca esti cu adevarat roman [Let me ask you a few questions to see that you are truly native.]
[Guccifer 2.0:] Man, I’m not a pupil at school.
[Motherboard:] What do you mean?
[Guccifer 2.0:] If u have serious questions u can ask. Don’t waste my time.
[Guccifer 2.0:] Am mult de făcut [I have much to do]
[Motherboard:] Si cat umblai prin reteaua astora de la DNC, mai hackuise si altcineva in afara de tine [When you got into the DNC network was someone else there besides you?]
[No answer]

A few questions about your argument against identifying Guccifer 2.0 as the attacker and being Russian.
1. Why would a non Russian attacker use a Russian VPN?
2. Can we attribute his use of the AOL email to human error
3. How do you explain his insider knowledge about the attack
Hi Michael,
1. Because no military/Intel cyber offensive team would execute an exploit in such an overt way. Great Vizzini’s line of reasoning of ‘you know, that I know, that you know, that I know…, doesn’t apply here. It’s very unlikely that any respectable Intelligence agency would launch a high visibility traceable attacks from their main HQ over a local carrier service.
2. You can try, but this is such an amateurish mistake that it would be difficult to reconcile with a common concept of operation of not using traceable email services and reusing the same accounts for multiple activities.
3. I don’t. Everything that Guccier 2.0 said about the exploit suggests that he is not the attacker, (1) he doesn’t have any verifiable information about the attack beyond some generic statements about using a zero-day and planting trojans. (2) all of these comments about being a “Woman lover”, and liking “Gucci”, sound like something a wannabe with a sizable bragging problem would say.
George Papadopoulos?
RESPONDING TO YOUR THREE QUESTIONS:
1.) WHY DOES A BANK ROBBER WEAR GLOVES..? TO CONCEAL HIS FINGERPRINTS..!
>>IF I WANTED TO DIVERT ATTENTION FROM MYSELF OR MY COUNTRY OR ORGANIZATION I WOULD USE THE IMAGE OF AN ADVERSARY OF MY TARGET OR WHO I WANT TO MAKE INTO AN ADVISORY…
***NOTE THAT THE HILLARY CAMPAIGN AND OBAMA ADMINISTRATION USED RUSSIA AS THE PROVIDER OF THE DOSSIER INFORMATION WHILE AT THE SAME TIME ACCUSING RUSSIA OF HELPING TRUMP WIN THE ELECTION, HOW DO YOU DIVERT ATTENTION BOTH WAYS USING THE SAME STRAW MAN FOR EACH EXCUSE..!
2.) USING AN AOL EMAIL ADDRESS DOESN’T REQUIRE A LOGICAL REASON, WHO USES AOL ANYMORE ANYWAY..?
3.) EXPLAINING HIS INSIDER INFORMATION WOULD CAUSE ME TO BRING THE LOGIC ALL THE WAY DOWN TO THE MOST SIMPLEST TERMS, IT IS MOST LIKELY THAT THE IMPLICATION BEING MADE THAT THERE IS ACTUALLY A GUCCIFER OR ANY HACKER IS SIMPLY A FABRICATION JUST LIKE EVERYTHING THAT THE OBAMA ADMIN AND THE DEMOCRATIC PARTY REPRESENT..!
I CAN USE AN INTERNET LOCATION MASKING APPLICATION AND APPLY TO IT ANY LOCATION THAT I WANT TO BY JUST CLICKING ON A RELAY PREFERENCE..!
Most likely, Guccifer 2.0 was operated by someone connected to the DNC, possibly Crowdstrike.
Hi Leo,
Thanks for the feedback. Here is a poetic response and an image of a highly classified device that relates to the Russian collusion:
There once was an inside leak in the DNC
The deceitful emails were delightful to see
Matt Tait from GCHQ advised the DOJ
Indict some Russians! By golly they’ll pay
The FBI without evidence said sure, we agree!
https://apelbaum.files.wordpress.com/2019/09/our-man-in-havana-top-secret-vacuum.jpg
1. Is it possible the files were downloaded at a slower speed over the net? Then transferred to a thumbdrive prior to getting to Wikileaks? After all, probably intermediaries would be used before things got to Wikileaks and it might be that a physical transfer was done to Wikileaks.
2. I agree that some of the mistakes seem unlikely for a government organization, but is it possible instead these were sort of Russian 4chan, LULZSEC jokers?
3. I’ve always found it strange that what was shared by Guccifer was the Trump Oppo research (hurting Trump) versus something embarrassing to Clinton or at least revealing key internal details (strategy, polling, etc.) This is a small point arguing against the Russia Guccifer theory.
4. I doubt Russian intelligence employees would do the Guccifer interview at all, let alone so poorly. That said, it could have been some (2) type joker. Another strong possibility is it is some person unrelated to any of the events that went down (even the initial Guccifer messages). Just third party jumping in and LARPing.
Hi Anonymous, thanks for your feedback. See comments in-line
1. Is it possible the files were downloaded at a slower speed over the net? Then transferred to a thumbdrive prior to getting to Wikileaks? After all, probably intermediaries would be used before things got to Wikileaks and it might be that a physical transfer was done to Wikileaks.
(YA:1) Yes, it is possible that these files were downloaded at slower speed (or a the right speed locally), but this would invalidate the claim that this was a real-time over the Internet exploit from somewhere in Romania. It’s a simple math problem. Given a connection speed, it should take certain amount of time to download a certain file size. What we know about the connection speeds in Romania and the US at the time of the alleged exploit contradicts the transfer rate claims.
2. I agree that some of the mistakes seem unlikely for a government organization, but is it possible instead these were sort of Russian 4chan, LULZSEC jokers?
(YA:1) Again, the issue is not so much the mistakes, but the overall attack characteristics and claims. We don’t have any low-level technical details about the exploit. For example, what is the relationship between the attack on the NGP Van system and the individual workstations that contained the emails. These are two different systems on different networks. Why did the attacker needed to waste time/effort with complex zero day exploits on the NGP Van system, when he had access to the soft and easy DNC users? Why not just spearphish them? What we do have is a lot of political narrative from the USG/MSM and epic/heroic story telling from CrowdStrike. CrowdStrike told us how they fought the hacker in a battle that lasted two weeks. There is nothing more specific about thier actions. Why do you need two weeks to get a parasite off your system? Would you wait two weeks watching a giant tick in your crutch sucking your blood and and infecting you with lime disease before removing it? If this wasn’t an intelligence operation (which clearly it wasn’t) and it was motivated by hacktivisem by the likes of LulzSec, then we would have a lot more derogatory information about the DNC (as you pointed out) and more pride of ownership.
3. I’ve always found it strange that what was shared by Guccifer was the Trump Oppo research (hurting Trump) versus something embarrassing to Clinton or at least revealing internal DNC stratigic and operational details This is a small point arguing against the Russia Guccifer theory.
(YA:1) Yup, that’s a good point and it goes to the heart of the question, what was the overall objective of this expensive and risky operation?
4. I doubt Russian intelligence employees would do the Guccifer interview at all, let alone so poorly. That said, it could have been some (2) type joker. Another strong possibility is it is some person unrelated to any of the events that went down (even the initial Guccifer messages). Just third party jumping in and LARPing.
(YA:1) I agree, if my life depended on finding/validating Guccifer 2.0, I would go hot and heavy after Lorenzo Franceschi-Bicchierai from Vice Motherboard. Everything about the interview tells me that it was staged and rehearsed. The Q&A doesn’t flow logically, it has too many dramatic gotcha moments, and it’s way too scoopish. Bicchierai covers cybersecurity, tech policy, privacy and surveillance, hackers, drones, and the intersection of technology and civil liberties. This is the perfect profile, motive, and opportunity for a reporter who is either trying to make a name for himself or is performing a lap dance for his handlers. The fact that the Guccifer 2.0 story was picked-up by MSM so quickly also suggests that senior management in Vice Motherboards was coordinating the blitz and worked with other outlets the likes of NYT and WaPo to spread the disinformation.
’ve always found it strange that what was shared by Guccifer was the Trump Oppo research (hurting Trump) versus something embarrassing to Clinton or at least revealing key internal details (strategy, polling, etc.) This is a small point arguing against the Russia Guccifer theory.
According to the Steele Dossier, Putin had all kinds of dirt on Hillary Clinton, but did not use it in order to get Trump elected when all the polls were saying he would lose big. Only Trump dirt was leaked through Steele, who also wrote about Trump’s people allegedly asking the Russians to release that very same dirt about Clinton.
There may be dirt on Clinton in the Kremlin:
https://www.realclearinvestigations.com/articles/2018/06/25/heres_one_unverified_leak_the_feds_wont_make_about_loretta_lynch_.html
The DNC hack is connected to the Steele Dossier on multiple levels. Up to and including the strong possibility of being the work of the same political and PR teams. For example, the dossier’s beginning composition date overlaps with the DNC leak. One of the key points that the Dossier makes is that the Russians are hacking US based systems and individuals, and As you noted that the Russians have dirt on HRC, Steele also claims that some of his sources have first hand knowledge of these attacks. So, both of these events and documents seem to retain an eerie sens of affinity and harmony.
You may want to check out The Mechanics of Deception. I did a deeper dive there into who worked on the dossier. It may help you with the bigger picture.
I have found evidence that Brennan likes to use FAKE INTEL REPORTS to cover-up for any illegal activities, as in hiding the source of intel gained through TORTURE. Brennan as deeply involved in the torture activities later investigated by Senate Select Committee on Intelligence 2013-2014.
By early 2014, Brennan worried about SSCI investigation, so he had the committee’s members hacked. He denied the charge of hacking, but was caught. Media speculated as to odds he would be fired. This was in April-June period in 2014. In May, Brennan came up with intel that Russia planned to interfere in elections in Western Europe and US. He changed the subject.
I suspect that the election interference report was another instance of Brennan faking intelligence to get our of a jam or cover-up illegal activity. That might have been all it was for, but, by 2015, copy-and-paste was used to create the 2016 Russian interference “insurance policy,” which was how Brennan always used fake intel–INSURANCE.
Thanks for your comment.
I haven’t seen evidence (fake or otherwise ) that was used to develop the Russian interference report. The January 6, 2017 IC assessment is devoid of any ‘proof’ or ‘factual’ language, it uses the soft term “confidence”. Its even worse, it relies on MSM reports (specifically WaPo and Vice Motherboard) to determine the identity of Guccifer 2.0 as Russian Intel.
What evidence do you have that show that Brennan used fake intel in the IC report?
I wasn’t referring to the IC Report, but a 2014 report that he gave to Obama in May 2014 predicting Russian interference in elections in Western Europe and the US. In May 2014, Brennan was in trouble for hacking the Senate Select Committee on Intelligence (SSCI) which was investigating CIA torture. Brennan frequently used false intelligence reports to cover his use of torture results so he could claim he got the intel from a legitimate source and not from torturing someone.
When the SSCI was closing in on torture in early 2014, Brennan hacked them. When he got in trouble for hacking, he came up with the elections report. False intelligence fits his pattern of behavior.
https://www.thenation.com/article/archive/government-war-against-reporter-james-risen/
https://twitter.com/Farrier105/status/1237786882458746881
https://www.realclearinvestigations.com/articles/2019/11/15/the_brennan_dossier_all_about_a_prime_mover_of_russiagate_121098.html
…other evidence they were trying to discredit Podesta emails is events of Oct 7, 2016.
(1) At around 3:30pm, Director of National Intelligence James Clapper issues a 400 word statement in conjunction with the Department of Homeland Security on “Election Security.” Most of it concerns the possibility that Russians might change actual vote totals and assures us that it’s unlikely. But the first 117 words are about hacking campaign related documents:
“The U.S. Intelligence Community (USIC) is confident that the Russian Government directed the recent compromises of e-mails from US persons and institutions, including from US political organizations. The recent disclosures of alleged hacked e-mails on sites like DCLeaks.com and WikiLeaks and by the Guccifer 2.0 online persona are consistent with the methods and motivations of Russian-directed efforts. These thefts and disclosures are intended to interfere with the US election process. Such activity is not new to Moscow—the Russians have used similar tactics and techniques across Europe and Eurasia, for example, to influence public opinion there. We believe, based on the scope and sensitivity of these efforts, that only Russia’s senior-most officials could have authorized these activities.”
(2) Around a half hour later, the Washington Post alerted the world about the infamous Access Hollywood tape featuring Donald Trump.
(3) And around a half an hour after that, WikiLeaks released John Podesta’s emails, containing devastating information about Hillary Clinton.
Some have claimed the fact that the Podesta emails were released after the “Access Hollywood” tape is evidence that Assange was trying to cover for Trump by diverting attention away from the tape. It’s, of course, possible that the three events occurring within an hour of each other is coincidental, but if it isn’t, this explanation is flawed.
First, it doesn’t account for the first event. If you think Assange was trying to drown out news about the AH tape then you have to still say it was a coincidence that the AH tape came out the same day Clapper’s report did. On the other hand, if you think that Director of National Intelligence James Clapper got wind of the fact that Assange would be releasing something damaging to Clintonand that both Clapper’s report and the AH tape were released in advance to respectively discredit and drown out the devastating information about HRC contained in Podesta’s emails, you aren’t left with any coincidences. In fact, I think there were rumors Assange was close to releasing something the day before, so it’s not at all implausible that Clapper made sure to try and find out when.
So, if you think the coincidences are too much to be believed, Occam’s Razor suggests that the first 2 events happened to counteract the third. But that hypothesis would seem to mean that Assange was being framed to discredit WikiLeaks releases and not as an end in itself.
Most of the time the law of parsimony doesn’t apply to Intelligence work because each phenomenon can have a large number of possible and complex alternative explanations to the ‘simplest’ one. So you have to evaluate all of the data points carefully enrich them and fuse them before you can come up with a working hypothesis.
I do agree that the sequence that you describe in terms of order of operations and ‘net’ benefit of the consequences suggests some form of staging and orchestration.
Just from the timeline point of view, having Access Hollywood, the DNC Hack, Crowdstrike, WaPo’s Ellen Nakashima report, G2, and Clapper so close to each other, without either one of them being aware of the others is suspicious to say the least. This act reminds me of the plot line in the P. G. Wodehouse’s novel “Jeeves Takes Charge”. In it, Jeeves’s makes the following observation to Bertie Wooster:
“Any undertaking that requires the presence of four people [people and events in our case] all in one place, all at the same time, while two of them are unaware of the fact, is fraught with the possibility of mishap sir.” (19:27)
https://www.youtube.com/watch?v=y-Wlaw78JN4
I’ve done some more digging. The alleged Russian hacking into the 2014 elections in Ukraine contain EVERYTHING that was alleged to have happened in 2016’s US election. Stolen emails released to the public, alleged attempts to alter vote totals by hacking, you name it. This was used as the template for 2016 in the US, using copy-and-paste type fiction writing.
If you go to the Conservapedia site and check what happened during Obamagate in 2014 this stuff comes up. Just follow the links to the footnotes and click on them.
The only reason I started checking on 2014 is because Nunes said that is where they found out about Russian plans to interfere in elections. They just used the Ukrainian story and took from it the elements they used to create “election interference” in 2016.
Ukrainian story means IC has less excuse for not being more pro-active if 2016 Russian interference was real. They knew from Ukraine what Russians allegedly did–steal emails and publish them, try to hack voting records, etc. all the stuff IC accused them of doing in 2016. Were they ready?
“We had no playbook for this.”–John Brennan spysplaining why IC wasn’t ready.
They didn’t do anything because none of it was real.
What you’re saying about Ukraine does sound interesting. Don’t know a lot about it, tbh, but will have a look at some point. Thanks for tip.
I’m not a computer expert. Wouldn’t the file time stamps show the intermediate download times, not the initial download? It could still be a slow, over the net download. Just that the intermediate transfers will have changed the time stamps. This would not then conflict with the report that the exploit was over the net (for the initial download).
Hi Anonymous,
A file would retain its OS properties only if it was moved around the native file system environment like on a FAT, NTFS, etc. If you perform remote file copy operation using a streaming protocol like HTTP, the file will be stamped with a new ‘Created’, ‘Modified’, and ‘Accessed’ properties as soon as the local write is completed.
You can try this by clicking on this link to download a file. After you download it, look at its properties. Do it several times and you will notice that each download gets new date and time properties.
I admit to not being a computer expert (at all), but I still don’t see how your reply answers my question. Fine: the initial download gets a new timestamp. (Never contested that.) THEN when the file is put onto a thumbdrive it gets a new timestamp. No?
I mean if the argument is that (e.g.) Seth Rich downloading onto a thumbdrive happens faster and this is shown in timestamps, wouldn’t this still be the case, if Gucci (e.g.) made a thumbdrive off of the his intermediate machine?
Wouldn’t the timestamp only show the last download, not previous ones? Thus a slow download over the net would be irrelevant if later the files had been trasnferred to thumbdrive or disc or the like.
Yes, you are right, every time you download the file the metadata would be updated, This is one reason why I don’t put to much weight on the ‘Created’, ‘Modified’, and ‘Accessed’ properties. We just don’t know how many times the file was downloaded and copied and what generation of the file was eventually published. Another reason is that it’s really easy to ‘touch’ these properties with a utility like AtrributeMagic.
I don’t know who downloaded these file or if they were even initially download to a USB drive. Maybe they were just uploaded directly to a cloud storage. The question of who removed the data from system is important, but even more so is how?
The only way to answer this question is to analyze all of the event logs that CrowdStrike collected over the two week period. These log files will show where the connection came from, what type of a connection it was (upload-used to push the exploits or download-to pull data), what protocols were used, what files were accessed, what software was installed, what user(s) were involved, etc. The problem is that everyone is fixating on the file transfer trivia instead of looking into CrowdStrike’s SIEM dump of the DNC and HRC projects. This is cyber forensics habeas corpus 101
Binney(the ex NSA expert who also was part of they team who analyzed the files) explained the timestamp issue as being one embedded in the way FAT stores the file on the drive upon first seeing it (meaning how it keeps track of which data block in the file is “next” as it presents the entire file) And the “number” of each block is set by using the rightmost part of the system time variable, the part that counts the fractions. It’s by looking at the file’s blocks that you can tell the file was originally received fast or slow. The WikiLeaks docs showed it was not a file they got remotely. they were handed a locally copied USB. Which makes the idea of remote hackers untrue.
Binney did a great job with his analysis. But in the end, I don’t think that the USB drive is as critical to understanding this case. None of the actions in the DNC leak show the hostile intel foreign fingerprints. Forget the cyber forensics for a moment, just from the point of view of the document inventory that was leaked, one of the key documents was a derogatory opp research about Trump. If this HLO was indeed a Russian active measure designed to support Trump, why publish a hit piece against him?
Jacob, here’s a small error in this article you ought to fix. You say ‘flaunt’ when you mean ‘fluent’. Here’s the incorrect phrase: “without actually being able to read and write flaunt Romanian”
Thanks Bruce for pointing it out. I’ve corrected it.
How do we know that the Russians didn’t leave all of these clues around deliberately (i.e. using a Russian based VPN and AOL email)?
We don’t know for sure, but generally, that is not how cyber/intelligence operations are conducted. There would be little gain from the public exposure and a lot to lose from the fallout.
Is is sound logic to assume that hackers sophisticated enough to write a malicious exploit, smart enough to get it pushed out into the parts of the internet it would likely fool DNC users to infect their computers, smart enough to steal all this info and keep the opposition from finding out they did until they released it- yet they are so stupid to effectively “sign” the exploit? Seems that would be unreasonable.
Also consider: did the party that would benefit from such falsehood have the ability to fake those signatures?
Keep in mind the Vault7 set of “tools” that the CIA had stolen from them and exposed- they included tools to create such signatures to impersonate a variety of countries. Brennen has the means, the motive and surprisingly, he also had the position to police himself. It’s not often the bank robber gets to investigate his own crime and pronounce the guilty party.
All good points, but I don’t think that you have try to explain the DNC leaks as a function of Vault7. None of the parties (including LEA, DNC, Crowdstrike, and media) has released any evidence that ties the lead to the Russians. The smoking gun evidence of APT28-29 turned out to be a complete hoax. Even Shawn Henry testified (behind closed doors…) that CrowedStrike had no concrete evidence of Russian involvement.
I am very late to the table on this one, but if you see this perhaps you can answer a question. In your image 4, on the left it shows the Word doc properties of the document created at 1:38 PM on 15 Jun 2016.
The Company name is given as GSA. That sure looks to me like the General Services Administration (US gov agency), which shows as the Company for MS Office documents created via GSA-contracted copies of the software.
The DNC server wasn’t supposed to be using a GSA-contracted MS Office suite. A number of Democratic politicians and aides (e.g,, many members of the US House of Representatives) had DNC email accounts, but the DNC is a private entity and should not have hosted GSA-contracted software.
Are you aware of another “GSA” that could have been the Company in the properties block?
It’s possible the DNC was improperly using a GSA-contracted MS Office copy. That would be the simplest explanation.
But since the FBI never saw the original server, and we don’t have verification that the files were in fact created on it, it does make me wonder if the Word and PDF files were not created on the DNC server at all.
Thanks for your feedback theoptimisticconservative.
Regarding the GSA Company property (which is on Image 5). The supposed author of this document is Warren Flood. This could have been Vice President Joe Biden’s information technology director at the White House (which does use GSA registered software). But interestingly, if you cross-reference this document to the same document in the verified Wikileaks dump, the original author is Lauren Dillon. Lauren Dillon was the DNC Research Director in charge of GOP/Trump research.
The likely explanation for all of this fancy footwork in manipulating the document’s property fields is the following sequence of events:
1. A user on a computer registered to Warren Flood (GSA) opens the DNC document (authored by Lauren Dillon), copies it, and pastes it to a new document.
2. A user on a computer registered to Warren Flood (GSA) sets the theme language to Russian.
3. A user on a computer registered to Warren Flood (GSA) modifies the document’s Author field to Феликс Эдмундович.
4. A user uploades the modified document to the Guccifer 2.0 WordPress website and publishes it to various media outlets.
Based on the document’s metadata there is little doubt that either Warren Flood, or someone using his GSA licensed MS Word created the Russian fingerprint. Also, it’s important to note that several other document also show this type of manipulation, but they were created by users named “Blake” and “jbs836”.
In terms of the big picture, it is possible that whoever added the Russian fingerprint did this as part of laying the ground work for future unmaskings. We know that in June 2016 the Obama administration (via people like Susan Rich and Samantha Power) started unmasking Trump campaign officials on the pretext of a ‘Russian interference’. This June 2016 activity overlaps with dates of the Guccifer 2.0 saga. So, it is possible that Guccifer 2.0 and MSM outlets like NYT who promoted him ware part of a larger campaign to affirm Russian involvement with the DNC hacks. If this is indeed the case, than it means that the DNC email leak could implicate Obama administration officials who were manipulating these documents on a government clock and GSA registered computers.
Thank you, Mr. Apelbaum. Your proposition that Obama administration officials were perhaps manipulating these documents is by no means far-fetched. I have no idea if the actual person using the Warren Flood user account in this case was Warren Flood, but Flood himself would have been in the Executive Office of the Vice President and a member of the National Security Council staff, where a number of Sypgate-related persons worked at the time.
My hope was to exclude the possibility that “GSA” referred to another entity (i.e., might be a commercial company name), but I couldn’t find one that appeared remotely likely, and it appears you haven’t run into anything that would shed light on hat. Thanks, again. (J.E. Dyer, “Optimistic Conservative”)
Warren Flood didn’t create “1.doc”, but he/his wife Alice McAlexander knew and worked with several of the researchers that wrote the leaked documents. Both, were also close with the DNC leadership. One of several points of DNC integration (beside Warren consulting for them) was them running a progressive on-line newspaper called 63Mag-for progressive political organizers.”
Hello, Forensicator looked into the Warren Flood name appearing in the metadata of those documents and concluded that it was NOT because they were created on a computer Flood worked on. A document that was created in 2008 on such a computer was used as a template to create the documents whose metadata his name appears in. The process and the likely reasons are covered by Forensicator here: https://theforensicator.wordpress.com/did-guccifer-2-plant-his-russian-fingerprints/
If you think Forensicator made a mistake, obviously it should be corrected. But, if not, bringing Warren Flood’s name into it when there’s no evidence he had anything to do with it is obviously a bad idea. Just letting you know so you can figure out which is correct.
Michael Thau
aclearerpicture.net
Hi Michael,
Thank you for your comment. Warren name is relevant to this discussion in term of him consulting for the DNC and both, his and wife’s 2016 political work on projects such as 63Magazine. Both also show linkage to organizations like CIVIS who share the funding DNA with Crowdstrike.
Thanks for the quick reply. I’m aware of all that. But if Forensicator is right and Flood’s name only appeared in the document because G2 grabbed a doc from Podesta’s emails from 2008 and used it as a template, than there’s no more reason to mention him than other person who worked for the DNC with (completely unsurprising) connections to other Democratic party outlets.
Unless there’s some problem with Forensicator’s work, then bringing up Warren Flood is both unfair to him and detrimental to making the case that G2 was connected with the Democrats in some way.
Bill Binney’s completely fallacious transfer speed argument that WL DNC emails weren’t hacked has already caused huge problems because it sounds neat and allows people to feel intelligent by quoting a technical result which they think they understand but don’t. Everywhere you look you’ll find Binney’s argument — Binney says it’s what he told Pompeo after Trump asked him to meet with Binney. So, assuming Pompeo was willing to be convinced, the one opportunity to get this in front of the President was ruined since Pompeo, after looking into it, would be sure to discover that the transfer speed argument is worthless. And if Pompeo wasn’t willing to be convinced, he was given ammunition.
Roger Stone’s lawyers also used the transfer speed argument in his one of their motions so its now enshrined in case law. The reason I bring it up is because this Warren Flood business has the potential to be the same kind of thing — an argument that, though fallacious, will appeal to ordinary people without the ability or will to look into things that discredits the real evidence G2 was a creation of CrowdStrike when someone with authority and an open-mind looks into it or is used to discredit it by people with closed minds.
Unless there’s something wrong with Forensicator’s work, apart from being unfair to Flood, nothing good is going to come of bringing Warren Flood into it.
In intelligence analysis there is a concept of sustained integrity. Truth is always rich in detail and organic. Regardless of what sequence you follow, the plot line will always perfectly converges for each individual/object/scene involved. Most truthful stories have complex charters, detailed timelines, rich interactions, and diverse network linkages.
Synthetically made plots tend to skimp on detail, be poorly linked, have abrupt timelines/dead ends, and be full of anomalies. Everything about the Crowdstrike DNC and Ukraine artillery hack claims as well as the Guccifer 2.0 plot is completely synthetic. It’s based on assertions and crypto facts that have not be confirmed by anyone beside CS. The whole G2 story exhibits such poor tradecraft that it can’t be possibly attributed to any intelligence organization. Whoever executed it spent very little time on research, testing, and the review of the end product prior to its release. None of the details we know about this operation follow any known cyber-attack CONOPS, which strongly suggests that this is the not so handiwork of a handful of law grade commercial US hacks. The MSM rapid mobilization and anomalies like getting preview materials prior to the June 14th release, or Lorenzo Franceschi-Bicchierai’s interview scoop also has coordination written all over it.
So, questions like the theoretical data transfer rates are interesting, but tangential to the question of the five W (who, what, when, where, how) and how did something as elementary as this almost got a sitting president impeached. In my post, tried to look at bigger picture (you may want to check out The Mechanics of Deception). So, in this context, Warren, the DNC, Crowdstrike, CIVIS, Biden, all exhibit certain linkages and relationships that appear to be relevant. As far as the tactical problem of trying to pin the tail on the CS donkey, I think that the problem is much simpler and that we are over intellectualizing it. But we can take this conversation offline.
I don’t disagree with any of that. Especially think you are 100% right that “theoretical stuff is tangential and problem is much simpler. I’ve been trying to “pin the tail on the donkey” without going into a lot of unnecessary technical stuff for a couple of years now in articles at “American Greatness.” (See, e.g.., https://amgreatness.com/2020/02/22/the-monstrous-lie-behind-crowdstrike/
My point about transfer speed stuff wasn’t meant to suggest it’s necessary. Just saying that, when normal people without any technical knowledge become attached to some belief, they like to be able to imagine they are privy to some very technical result that decisively proves it.
That’s why the fallacious transfer speed argument that WL’s DNC releases couldn’t have been hacked has proven so popular. Literally every time I write about fake DNC hack, I get at least a half dozen comments by people informing me of the transfer speed argument all of whom, to a greater or lesser degree, ignored the good evidence I gave them because they’ve put their confidence in the fallacious transfer speed argument. It gives people without any technical knowledge who want to believe Russian DNC hack was faked a simple sentence they can utter which allows them to imagine they are privy to some super-technical fact and to not bother thinking about the topic anymore. That’s why it’s dangerous.
Only brought it up because I think Warren Flood attribution has similar potential. In addition, it appeals to people’s desire to connect fake hack directly to Dem party, so in a way it’s got more potential.
Just don’t see how there’s a case for bringing Flood into it unless Forensicator is wrong about what RTF tags and RSIDs show. Since Adam Carter vouches for it, I’ve been assuming Forensicator’s conclusions are valid. But I’m not technically proficient enough to dispute either of them and it’s possible they’ve made a mistake. But, if not, seems unfair and unwise to bring Flood into it.
Anyway, as I say, couldn’t be more with you on thinking all this technical stuff is just a distraction to pinning the tail on the donkey. Unfortunately, it’s especially distracting to people without any technical knowledge who want to believe DNC hack is fake. My only concern is to telling a story that gives people an idea of what really happened that doesn’t misrepresent anything or leave any crucial facts out.
Also, happy to take conversation away from here. I’m assuming you have my email as a result of me commenting here.
It’s very interesting that Dmitri has left CS.
Yup, but he walked a way smiling and with a sizable chunk of equity.
What I find extraordinary about Crowdstrike is that their meteoric rise was almost entirely based on this DNC Russian hack fairytale. This by itself, deserves a new category of Oscar like awards. How many US publicly traded companies can claim that they started as a PR stunt?
Yaacov,
I have researched the DNC data loss (I refuse to call it anything else) for the past two years and just now got news that the Opposition Research document, that was identified by WaPo as the only two files stolen, came from the PODESTA EMAILS (?). I’m mystified about how that can be, or how, if it was, it escaped the early reporting that I relied upon to gauge what was claimed early on vs. what was claimed later, such as “only two files were stolen,” which Guccifer 2.0 (G2) ridiculed in his opening blog post.
I have vociferously objected to other reporting claiming the opposition research came from the Podesta emails. Could it not have come from a CC to Luis Miranda at the time the documents were sent to Podesta? If not, let me know what the evidence is that they come from the Podesta emails. Then I have to find out just why this has not been widely reported in the media. If I turn out to be wrong, and it was from the Podesta emails, then I have to track it all down.
I have found an interesting potential tie-in between the start of the notion of Russia interference in the 2016 election and the time John Brennan got nailed for hacking the Senate Select Committee on Intelligence in 2014. John Boy started his hacking operation during the CIA torture investigation, and got in trouble about April 2014. In May 2014, Obama got a report from US Intelligence Services that a “Russian source” told them of a Russian plan to interfere in elections all over the West, including the US. Just when Johnny gets cornered for HACKING, he gets to change the subject to Russians hacking to interfere in how our elected politicians hang on to their lucrative jobs. I had a hunch, and checked the dates. The incidents overlap. A Russian got spirited away to the US in 2017 and tucked away in Virginia. His name was Smolenkov. He was A source of CIA for Russian interference in the election. Could be the 2014 guy, or he is supposed to represent a source that never provided anything.
What do you think it was really all about? I think it was Assange. They wanted to frame him as a Russian asset. Getting the emails helped reinforce that idea. I’m not sure they gave a damn who got elected. What do you think?
Thanks a lot,
Guy Jordan
Thanks for your feedback Guy.
Please read the post carefully and follow the links for the two documents used to create “1.doc”. Both will take you to the Podesta Wikileaks dump. The primary source for the statement that only two documents were stolen from the DNC by the APT28 and APT29 is Ellen Nakashima, the WaPo reporter who broke the story on June 14, 2016 (you can read the details in the image below). Her sources were the prime movers in the DNC and Crowdstrike. The article below is the baseline for the Russian DNC hack narrative and most of the MSM derived their details from it.
Based on the Mueller report we know that the two file count is false, as the DNC lost many more files. So this is one of many problems with the whole Russian hacking narrative, the claims are simply unreconcilable.
https://apelbaum.files.wordpress.com/2020/03/the-washington-post-june-14-2016-and-nakashima-linkage-3.jpg
Thanks for the fast response. I always knew that the June 14, 2016 WAPO article about the data loss was false, but I enjoyed using it in discussions on-line with Russiagate believers to gauge their responses. Most don’t know much outside of what they see on TV.
The early coverage was lacking because of the way Crowdstrike and the DNC described the details of the incident, which made it look more like a fraternity prank than an “act of war,” and the ORLANDO PULSE ALLEGED SHOOTING took place that very weekend before the story broke on June 14. Since Omar Mateen’s daddy is acquainted with US intelligence, the FBI (informant) and State Department (he wants to be President of Afghanistan and in contact with State as a result) this co-incidence of events is curious.
How did Crowdstrike and the DNC get away with the original article and not get questioned for lying to WAPO? They would have HAD to have lied during that Nakashima interview, but had no prayer of getting away with it once the truth came out about the extent of the data loss. When I first started seriously researching it, I had to wonder “What happened between the interview and Crowdstrike’s altered description of the hack to a major data loss–after claiming only 2 files lost?” I could only come up with Guccifer 2.0 appearance. That was what had to change their story from 2 files to the devastating hack that Crowdstrike just sat there and watched happen because, as Donna Brazile claimed in HACKS, “the DNC” ordered Crowedstrike to stand down until after the primaries were over.
Going from 2 files stolen to massive data loss was a huge pivot. Who would deliberately put themselves in that position in full view of the public? It makes Crowdstrike look like either incompetents or frauds. The media had to have issued orders to all reporters to ignore Crowdstrike making that pivot. In military terms, they had their flanks hanging in the air. No one in the media exploited it, and it is still ignored even by some independent investigative reporters working Twitter.
So, whoever ran Guccifer already had the Podesta emails two months or so prior to the DNC data loss? I’ll take a look at Forensicator about that before I ask any further questions about it, or express any opinion about that.
What we know is there is no real OFFICIAL VERSION of this data loss that reconciles with anything that is in reality or approaches commonsense, but I’m used to that after watching everything from the JFK assassination to this thing.
Thanks for your help, and I’ll be in touch.
I’m commenting on this separately since it involves different research I’m working on now, but I think is related. It has to do with the proximity of two events in 2014:
1. John Brennan getting caught hacking the SENATE SELECT COMMITTEE ON INTELLIGENCE and also getting caught lying about it.
2. John Brennan, contemporaneous to the scandal of hacking the SSCI, made his first report to Obama about a Russian informing CIA that the Kremlin has plans to interfere with elections in Western Europe an the US. I think I found the Russian, too, some guy named Smolenkov, whom Brennan had taken to US in 2017, supposedly for protection.
https://www.realclearinvestigations.com/articles/2019/11/15/the_brennan_dossier_all_about_a_prime_mover_of_russiagate_121098.html
My present position is that Number 2 was a made-up story–in its entirety–to change the subject from Number 1 to Number 2, and maybe that was all it was until the maniacs in the CIA decided to resurrect the story to:
1. Cover what they were doing in 2016 so the Russians could be scapegoated.
2. Pass the emails to Wikileaks so that Assange could be framed as a Russian asset and eventually removed from the Ecuadorean embassy and arrested, followed by extradition to US. Until Assange could be labeled as an espionage agent, he would be a journalist and protected by past Supreme Court rulings from prosecution for publishing stolen documents.
Smolenkov is just being used as the faux source of the “Russian interference” story. The CIA can wheel him out in a pinch if they need an instant Russian source for the story. Russian interference in elections is comparable to the WMD hoax in the Iraq War. I look for a reasonable example of COVERT Russian interference in the election and can’t find any, like looking for WMD in Iraq.
I think the true target of all this was Assange, not Trump. I think the Establishment could care less that Trump is in the White House. They only act like they care about it. If they wanted Hillary as President, the old bat would be in the WH now. It wasn’t about the election. It was about Julian Assange.
Good points. Both Mateens (Seddique and Omar) were intelligence and LEA assets. That is how Omar managed to get off the US Terror Watch list at least twice. The bigger problem with the whole Mateen story is that it exposes a pattern of poor CI agency practices. It also shows that very senior individuals like Bryan Paarmann (the Mateen handler) and James Comey were dishonest when discussing the Pulse night club shooting.
You can find little more details about the CI issues I’m referring to and the Comey problem in Toxic Masculinity My Foot!
https://apelbaum.files.wordpress.com/2020/01/the-fort-pierce-mosque-cair-connection-2.jpg
https://apelbaum.files.wordpress.com/2019/09/omar-mateen-and-orlando.jpg
Here’s a link to a Podesta email publshed by WikiLeaks. Haven’t looked at it in ages but pretty sure the Trump oppostition research file attached to it is the one G2 rleased. Also pretty sure that the file isn’t in any of the DNC emails.
Also, it’s not just the Trump op file. The irst five files Guccier 2.0 released all later turned up in Podesta’s emails. https://wikileaks.org/podesta-emails/emailid/26562. I think it’s all explained here https://archive.fo/2dMfC#selection-597.55-597.60
Finally, it’s not even just the first five files. Forensicator did a graph showing where most of G2’s stuff later turned up. IIRC, he did a few more rleleases that contained stuff that would later turn up in Podesta’s emails up until around July 1. I can’t remember the exact date, but sometime around July 1 he stopped releasing stuff from Podesta’s emails and started releasing stuff that would turn up in WikiLeaks’ DNC releases. Will try to track down the graph at some point but it was in an article at Disobedient Media and the site went down for some reason so everything there is gone. So might need to make inquiries to get a copy.
I found an archived version of the article with Forensicator’s graph of where G2’s releases came from: https://web.archive.org/web/20180925054636/https://disobedientmedia.com/2018/09/forensicators-analysis-supports-assanges-statements-on-the-dnc-podesta-emails/
Don’t seem to be able to attach images, but if you go to the link and scroll down you will find it.
According to Forensicator’s graph, apart from the five files that would turn up in WL’s Podesta emails that G2 released when he debuted on June 15, he also released what looks like around 10 files from Podesta’s emails on on June 18.
Then on June 30, G2 released what looks like a single file from Podesta’s emails though the bar on the graph might represent two files. However, he also released what looks like around 10 files that would turn up in WL’s DNC emails on June 30.
Then, on July 6, he released what looks like around nine files that would later turn up in WL’s DNC emails. After that, none of G2’s releases on the graph contained any files from WL’s Podesta or DNC releases. However, the graph doesn’t include G2’s September 13 release, (which, I’m pretty sure is the one on which Forensicator did his famous transfer speed analysis.) So it might be missing other stuff as well.
In any event, G2 somehow got ahold of a lot of files from WL’s Podesta’s emails and from WL DNC emails as well. For some reason, in early July he decided to start tainting the DNC emails instead of Podesta’s. My hypothesis is that CS discovered the DNC leaker at that point and had accidentally chosen the DNC for their fake hack in the June 24 Wapo story because they couldn’t say Podesta’s emails were phished and wanted to keep target of fake hack as far away from HRC as possible given that here unsecured server was still a very serious issue. That’s why G2 starts releasing stuff from Podesta’s emails, which the Clinton campaign new were stolen.
But sometime in late June they discover the DNC really was hacked and then start releasing DNC emails. Interestingly, they release their final bunch of DNC emails just four days before July 10. Could be a coincidence though. I’m agnostic about all of that.
…should say June 14 Washington Post story, not June 24.
Hi michaelthau,
All of your comments are plausible, but it’s difficult to reconstruct the publication logic. The strategy could have been ‘do the best with the bad hand dealt to you and inflict the maximum damage you can on Trump’, or ‘let’s throw the Podesta virgin into the volcano and hope that its stops rumbling’, or some other unknown angle, unfortunately, it’s all speculative.
The bottom line is that whoever released these early documents didn’t get them from the Wikileaks batch that only came out in October. And if we assume that Guccifer 2.0 is fictitious figure, then this whole operation had to be an internal DNC/HRC damage control move.
In Intelligence analysis these types of problems are considered trivial. That’s because you have all of the suspects under your jurisdiction, detailed timelines, written statements, motives, surveillance, and plenty of evidence. This is not a difficult problem to solve, but just like with a horse, you can bring it to the trough, but can’t force him to drink.
Agree. There’s an overall picture that makes very good sense to me and seems organic. But agree it’s totally speculative and I wouldn’t be shocked at all if it was wrong in crucial respects. You’re right that important concrete issue is where the hell did G2 get files from Podesta’s emails and speculation probably detracts from that.
Also think second somewhat concrete issues is: What could have motivatied Alperovitch and Henry on June 14, 2016 to loudly release the information that Russian intelligence agents had penetrated the DNC servers and, in particular, had stolen a file of Trump opposition research? Still speculative to some extent. But think it’s not speculative to assume that doing so had to be advantageous to the DNC in some way. And once that’s assumed, the number of ways it could have helped the DNC seems very limited.
This is the $$$ question. You answer that and why he promoted the Ukrainian Artillery Hack and everything else will fall into place.
Please oh please oh please do a follow-up here now that we have way more evidence made public and you were proven right https://www.thegatewaypundit.com/2020/05/exclusive-absolutely-correct-released-transcripts-show-crowdstrike-no-evidence-russia-hacked-emails-dnc-sent-wikileaks/ Seth Rich is the only attribution I can make at this point, no other person or intel service could make any sense to me.
Could it be Flynn?
A FISA judge denied a FISA warrant in June 2016.
Same FISA judge approved a warrant in Oct. 2016.
That FISA warrant used on Mike Flynn-why there’s no FBI unmask between Dec 29th (date of the call) and Jan. 4th. 2017.
The FBI had drafted a memorandum on Jan. 4, 2017 to close the investigation — but Strzok texted a colleague to keep it open.
Theory is contractors (fusion gps/crowdstrike) were abusing 702 about queries to spy on Flynn/others until Mike Rogers becomes aware and shuts it down.
Adm. Mike Rogers becomes aware of 702 abuse in early 2016 and in mid 2016 Rogers ordered the NSA compliance officer to run a full audit on 702 NSA compliance.
Several violations found, and Rogers is briefed on Oct. 20 2016.
On October 26th, 2016, full FISA Court assembly, NSA Director Rogers personally informed the court of the FISA 702(17) violations. Additionally, Rogers also stopped “About Query” permanently.
The Halper/Flynn/Lokhova 2014 shows Flynn was targeted before the Trump Campaign began. Once they saw Trump could win, insert Steele. So the Russiagate Narrative fit all of their problems at the time and the Ukranian Artillery Hack backed it up, they could blame the hack on Russia while creating a hoax involving Russian Collusion.
LG Flynn was under surveillance long before December 28, 2016. Monitoring his communications started shortly after he voiced his objection to the Iran agreement and became a political threat to Obama’s pro-Iran policy. The original WH hit job was going to claim that he was an Israeli asset. But, after treaty was ratified in 2015 he was no longer a threat, so, they dropped the contract on him. Then, in 2016, he became a target again, so the collusion story was just changed from Israel to Russia. That is how Obama personally knew in advance (and Sally Yates didn’t) who Flynn was talking to and that is why the DOJ didn’t have anything or record.
My theory all along has been that Flynn was targeted because he was adamant that the Russian DNC hack was a ruse (see Rick Gates’ testimony). Both Manafort (see RG testimony) and Stone were also aggressively pushing it was fake; Stone made doing so part of his brand until Mueller indicted him and that judge put a gag order on him.
Another of Mueller’s targets, Konstantin Kilimnik was also adamant that the Russian DNC hack was fake (see RG testimony). And Michael Cohen’s prosecution helped cement the Russian hack narrative because of the story he met with Russians in Prague to arrange payment for the hackers. The story was eventually revealed to be BS. But the mass of people who believe all this garbage either don’t know or don’t care as they’re prepared to accept anything that helps justify they’re hatred of Trump.
Also, in his recently released testimony, CrowdStrike President Shawn Henry admitted they had no “conclusive evidence” that anyone had stolen anything from the DNC system. But he alleged that the supposed APT 28 malware CrowdStrike claimed they found had been used to “prepare” files for exfiltration on 4/22/16. One obvious problem here is that the earliest compile date on any of the APT 28 malware CrowdStrike said the detected was 4/25. But, it’s also interesting that the very next day, 4/26, happens to be when Misfud told George Papadopoulos that the Russians had Clinton emails.
My view has always been that the only way to make sense of Spygate is that it’s purpose was to cement and tie Trump to the Russian DNC hack narrative. CrowdStrike Faking Russian cyber espionage and key Obama administration officials aiding and abetting them is one of the greatest political crimes in our history. And it had huge ramifications, as it resulted in sanctions on Russia and substantially worsened relations. All the effort they went through in the various parts of Spygate doesn’t make sense if all they were doing was spying on Trump. They didn’t believe Trump had a chance and what information could they have possibly hoped to gain that would have been worth the effort and risk?
But the Clinton campaign knew Podesta’s emails were stolen and knew that there was a ton of damaging stuff in there that they needed to distract ordinary voters and Sanders’ disgruntled base from. Within a week of the Podesta phish in late March, CrowdStrike started a job at the DNC allegedelyt dealing with the NGP-VAN incident that happened way back in December. The supposedly coincidentally finished that job just a few days before being called in to deal with the Russian intrusion. Seems likely that when CS was called in allegedly to deal with NGP-VAN breach three months after the fact, they were really dealing with Podesta phish which had happened less than a week before.
It’s definitely clear that Mueller’s main purpose wasn’t to get Trump but, instead, to cement bogus Russian hack narrative. Apart from the 5 indictments mentioned above, his 7/13/16 of those 12 Russian nationals for hacking the DNC served no other purpose than cementing the narrative since he (or Weissman if he was really running the show) knew there was no chance of getting them into court. And the February indictment of Concord management and the others help to establish a background of widespread Russian election interference for the vast majority of the population not paying enough attention to realize it was obviously all bushit. In short, virtually everything Mueller did either served to reinforce the Russian DNC hack narrative or shut down prominent people who were opposed to it.
The, to my mind, false idea that Mueller was primarily out to get Trump helped too in that Trump’s supporters were so busy gloating about Mueller not finding any evidence that the Trump campaign was involved that they didn’t notice Mueller was confirming that Assange got the DNC emails by way of Russian cyber-espionage (and that the Russians had also phished Podesta’s emails) and, hence, that Trump owed his win, at least in part to Russian cyber-espionage.
Thanks for your comment Michael.
There is a lot of confusion regarding Flynn’s surveillance timeline. The fact is that he was under surveillance long before December 28, 2016. The WH started monitoring his communications (via a 3rd party) shortly after he voiced his objection to the Iran agreement and became a political threat to Obama’s pro-Iran policy. The original hit job against him was going to claim that he was an Israeli asset and did not involve any FISA activity. But, after treaty was ratified in 2015 he was no longer a threat. Then, in 2016, he became a target again, so the collusion story was just changed from Israel to Russia.
Thanks for additional useful info Yaacov. If I’m following you, there was an interim period after Iran deal was passed but before 2016 targeting of Flynn in which Obama’s people weren’t actively going after him. Do you know whether the spying continued during that period?
Yes, Flynn was under NSA and 3rd party surveillance from April 2014 through 2016.
A motivating discussion is definitely worth comment. I do believe that you need to write more about this subject, it may not be a taboo subject but typically folks don’t discuss such subjects. To the next! Many thanks!!|
Thanks for your kind words Arianna. Everything should be open to debate, taboos should only apply to certain actions not speech.
Off subject, but I can’t seem to locate your original article that was the main source for this short piece here
https://www.thegatewaypundit.com/2020/02/ilhan-omars-second-highest-donor-basim-omar-sabri-is-a-convicted-felon-who-regularly-raises-funds-for-hamas/
Would appreciate any help.
Thanks and kudos for all of your incredible work!
Hi Jim,
I don’t think I wrote a dedicated post about Basim Sabri. You can use the following composite for details. I hope it helps.
https://apelbaum.files.wordpress.com/2020/06/basim-omar-sabri-the-profile-of-ilhan-omar-top-donor.jpg
Thanks for the clarification. Any insight you can share into Sabir relationship with the El Nuevo Rodeo?
Yes, a family relative by the name of Mona Sabri AKA, Allan Botchman, Marianne Aboutanos, Richard Williams owned that property via a her company Omer investments, Inc.
Thanks for the useful information :)
Is the NSA able to capture metadata from government issued blackberries?
Anyone with access to the notwork on which these devices operate on can capture metadata, this includes the carriers.
So, even though Hillary smashed her blackberries with a hammer, the NSA still has her info?
I don’t know what’s the source for the claim that HRC’s phones were smashed with a hammer. Records of text messages, phone calls, and other activity are kept by the carrier and network provider. Also, HRC used multiple phones, so even if some of them were ‘destroyed’, one could still examine her other devices.
https://apelbaum.files.wordpress.com/2020/08/hrc-cell-phones.jpg
Correction: it was her aides who smashed them. But, thank you as always for clarification about government Issued phones. Here is one link about it… https://www.wired.com/2016/09/actually-clinton-destroyed-phones-better/
A few observations about your link:
1. Only 2 of the 13 blackberries were allegedly smashed. We don’t know which two devices and why these two were selected.
2. We don’t have actual evidence that these two devices were actually destroyed
3. HRC used other non-government issued phones. We don’t know what happened to these devices
The inference in some of these articles about smashed phones is that all her metadata was lost and not retrievable. Bloggers are saying that blackberries are not traceable by NSA. I wanted clarification because it never made sense to me.
It’s not that the NSA can’t technically collect data from blackberries, the issue is that they are restricted from doing so on domestic/US citizen devices. The actual agency that would be doing this type of investigation on HRC would be the FBI. Note that they successfully recovered the emails and text messages from Peter Strzok’s and Lisa Page’s devices :-)
Curious. Rosenstein released the texts. He also testified recently the dossier was not in the FISA against Carter Page. The IG said it was. DOJ vs FBI… the saga continues. https://www.youtube.com/watch?time_continue=133&v=cKh8JjfXAS4&feature=emb_logo
You have to pay close attention to what Rosenstein is saying. When he stated that “the Steele Dossier, is not in FISA, it was not submitted to the court”, he was right, the actual document was not submitted to the court. Nevertheless , it was still used as one of the main sources for the allegations against Carter Page, and without they would have had not case.
You can find more about the dossier’s who/what/where details here: The Mechanics of Deception
I don’t believe Hillary Clinton was Considered a “Domestic US Citizen” while working at the State Dept.
She is Considered as a Member of the Dept of State and any Device she uses falls under the Security Protocol of the Bureau of Network Services and is a Replicated Device for Matters of Record…
No Matter what is Transmitted on that Device it is on Govt Equipment and is Archived and a Property of the People, whether the People are able to access all of the Data is another issue based on Sensitivity…
And while on the Subject of Network and Internet Protocol, the EMail Server Domain Name was ClintonMail.com and the EMail Addresses were just as Simple…
For that Server to Communicate with Servers that Reside within the .GOV Domain at Levels that she Communicated the server would have to be Granted Access or Authorization to Reach Specific Destinations Depending on the Level of Security of the Destination Domain…
With that said, an EMail or a Stream of Packets with The Destination of a Domain within the Dot Gov Infrastructure would be Flagged if it didn’t carry the Proper Credentials for Access…
Imagine the Look on the Network Admins face when he is Sifting Through Flagged Domains that Attempted to Communicate with for Example The State Dept.gov Domain, He or She is Looking at ClintonEMail Dot Com thinking ok someone is Spoofing the Domain or it is another Clinton…
Proceeding to the Data that was Trapped and Flagged and what do You know, “Barak This is My Email Address on My Email Server We Talked about – “hrod17 at clintonemail dot com” Pleas reply to establish that we are live…
Needless to say the Dept that Received this “Test Email” was the NSA and the Decision was made to “see where this Goes” and ‘Archive Every Transmission to and from Every Device that the Server Communicates with being that it is a “Suspicious” Server and it is COmmunication with Govt Equipment Under the Jurisdiction of the NSA or Governing Body Respectively falling under the NSA…
So if ever the Question Surfaces as to whether the Data CAn Be Recovered from Govt Issued Equipment the Answer 99.9% of the time YES..!
HRC had multiple cell phones while at State, many of these were her private US based non-government issued devices.
As far as the HRC email server mystery, I think that it’s much simpler than its made up to be. While in State, HRC (via several non-government organizations like Platt River and individuals Paul Combetta) stood up a private server and then forwarded > 30K of sensitive emails from her .gov account to that server. To add insult to injury, her admin(s) also made on-line backups of these emails by forwarding them to several other accounts like carterheayindustries@Gmail.com. They also made a backup copies on portable USB/HD storage. Some of these devices were then kept by the admins.
Long story short, there is no need for sophisticated SIGINT intercepts in order to find these emails… All someone in the DOJ/FBI has to do is just ‘nicely’ ask people like Paul Combetta to spit them out. It is likely that even now, HRC’s emails are still sitting on someone’s USB/drive at home or in the cloud. One thing is certain, HRC’s emails were not ‘all deleted’ through BleachBit and the use of 5lbs hammers.
https://apelbaum.files.wordpress.com/2020/08/aaron-zebley-2.jpg
HRC’s Emails were Copied to a Gmail Account by Platte River Employee Paul Combetta
I’ve never closely read the Guccifer 2.0 chat transcript until now. I’m baffled at how obviously fake parts of it are, like the translations of Guccifer’s Romanian into broken English. The phrase “Asta e din partea următoare” being translated as, “That’s the next” is hilariously inept. LFB’s claim that he’s using Google Translate isn’t remotely believable. Today it translates the phrase as, “That’s from the next part.” Even assuming Google Translate was not as good then, it wouldn’t have magically omitted “partea” (part) from the translation.
Also funny is G2.0’s careful stylization of “CrowdStrike” and “Google” while incessantly saying “u”.
Hi Yaccov, I don’t know if you’d be interested, but I’ve written a book on my search for G2. I’d be delighted to have your thoughts on it, and can send you a pdf of it if I had an email I could send it to.
Sure, you can email it to: Y[@]YaacovApelbaum.com. Does it have a lot of pictures?