A number of internet researchers and reporters have asked me to evaluate some of the imagery and files that are being distributed by one George M. Nasif through his Twitter, Facebook, and website. Nasif claims to possess vast amounts of proprietary DOJ, diplomatic, intelligence community, and law enforcement records, in addition to donor credit card payments and a variety of classified emails. Nasif, who promotes himself as a network security specialist has significant presence and engagement on SM. His Twitter network alone has over 17K followers and its growing.
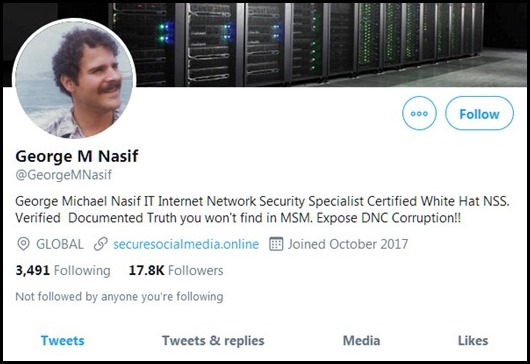
Image 1: George Nasif’s Twitter Profile
George Nasif, AKA George Michael Nasif, makes a lot of bold claims about the esoteric sources of his data and his deep knowledge and insight into current events. These claims seem to resonate well with his followers and influence network. A typical posting that promotes his content includes statements like:
“My Server files on the gangsters of the Obama admin. over 2 million documents. 3 Terabytes of information. Has now more than doubled to over 6 TB of files”
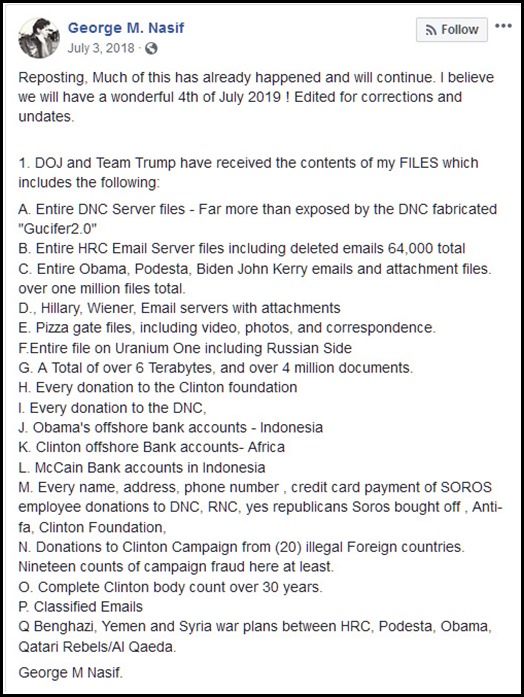
Image 2: George Nasif’s cave of data wanders
Running some analytics on Nasif’s depositories (some of which are housed in a public DropBox archive) reveals that almost all of his data and images were scraped from various forums, websites, and social media outlets. None of the examined data is proprietary in any way nor was it obtained recently. Also, contrary to his claims, his data set doesn’t even come close to 6 TB or millions of files.
The following image illustrates the data sources found on Nasif’s site. This screenshot is a Nasif snippet from a flight log on Jeffery Epstein’s Boing 727-31 TN N908JE showing Bill Clinton on the passenger list. This document was originally disclosed as part of the Epstein v. Edwards lawsuit in 2009, it was collected by Nick Bryant and published by John Cook via Gawker.com.
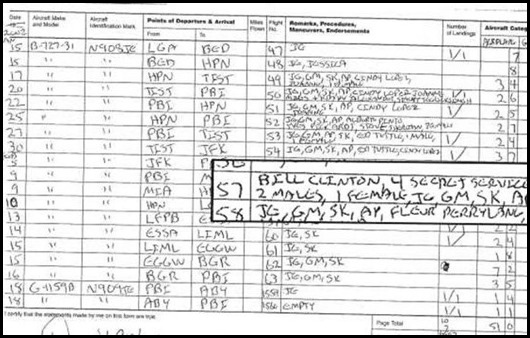
Image 3: Nasif’s snippet of the flight logs to Epstein’s private island
Nasif however, doesn’t provide a direct link to this source document nor does he credit John Cook and Nick Bryant. Instead, as can be gleaned from his tweet below, he implies that his depository may just be the only remaining source for this information, which is clearly not the case.
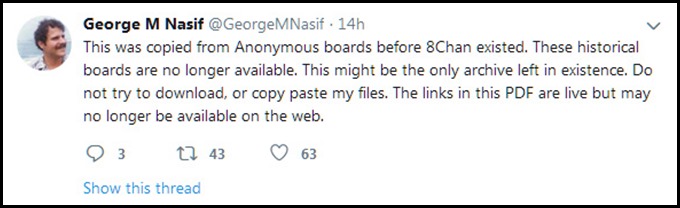
Image 4: “This might be the only archive left in existence.” Nasif, obfuscating the real sources of the data in his ‘proprietary’ archive or claiming that he (Team George) is the source.
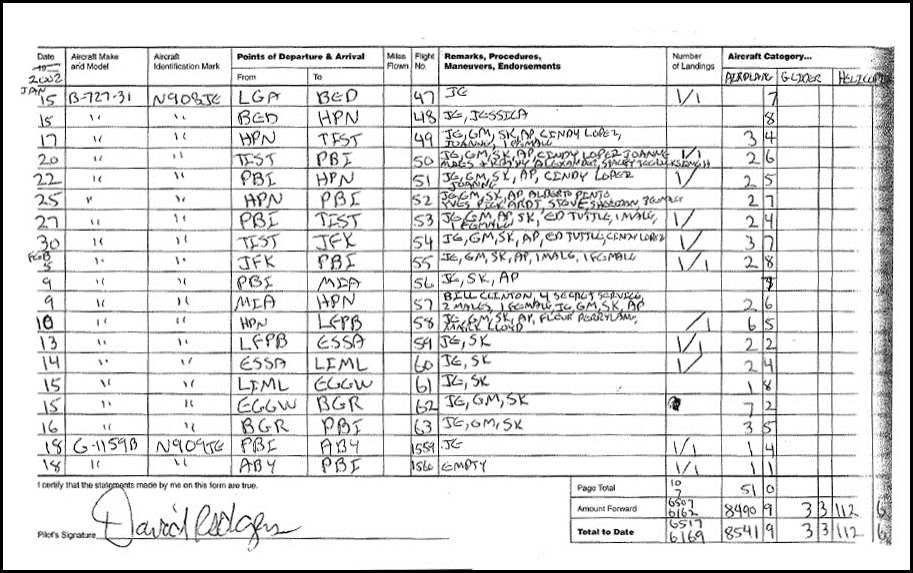 Image 5: One example of the source of George Nasif’s “proprietary” data depository (this is the source of of Nasif’s snippet seen in Image 2)
Image 5: One example of the source of George Nasif’s “proprietary” data depository (this is the source of of Nasif’s snippet seen in Image 2)
Beside the misattribution and hiding the real sources of his data, many of the images in his depository show evidence of touch-ups and post editing (it’s unclear by whom). The images have the wrong authorship attribution and their labels have misleading descriptions of the content. Many of the screenshots of the documents also exhibit font type and resolution mismatches, suggesting that the text on some of the images was retyped after they were produced.
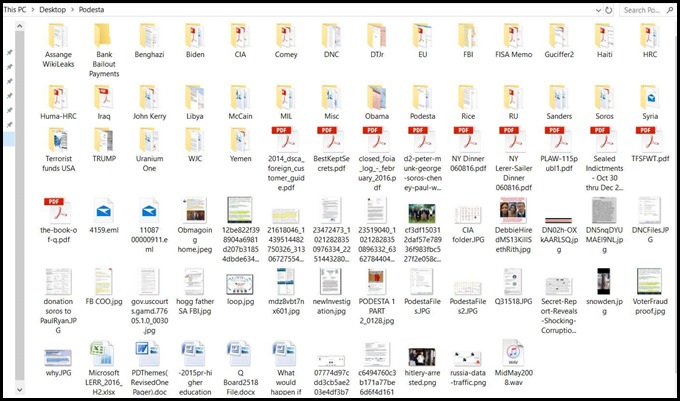
Image 6: Some of the ‘proprietary’ content advertised by George Nasif in his DropBox
The logistics behind Nasif’s > 6TB cloud based archive raise questions about his ability to float such an enterprise as a non-revenue service. IBM CDN cloud storage goes for $0.02-$0.085 per GB. Doing a quick math, shows that at these rates, Nasif could be spending an upwards of $100-$700 USD a month on storage alone and that doesn’t include the bandwidth cost for streaming all of the conspiratorial video files.
His claims about having pedophilia related images and records (the AI flagged several) are problematic to say the least. Beside the moral issues with possessing, posting, trading, and directing others to access this content, there is also the small problem of breaking federal and sate laws. His references to having personal and company financial data such as passport numbers, credit card numbers, bank accounts, and other PII data, could result in multiple felony charges for him and for anyone who has a copy of these records. Also, publishing this information (as he claims to have done) could be prosecuted under state doxing laws. If his public records do indeed contain names, addresses and phone numbers of federal employees, he and whomever downloads this data could also be potentially prosecuted under 18 USC § 119.
In terms of Nasif being a subject matter expert and uber-communicator, his writing style exhibits habitual poor grammar, punctuation errors, spelling, and capitalization issues—the hallmarks of an author not accustomed to technical writing. His claim of being an “IT Internet Network Security Specialist Certified White Hat NSS” is also dubious as his professional career mostly revolved around house painting. He has a zero industry security footprint, he has very limited technical vocabulary, and he exhibits a poor grasp of even basic computer security concepts. His professional network and background also fail to show any traces of Information security experience to back up many of the cybersecurity interpretive claims and ‘big’ statements.
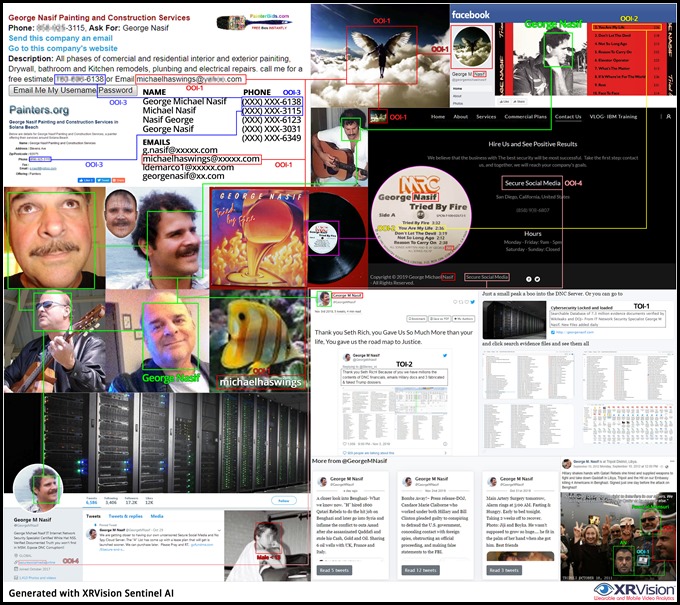
Image 7: George Nasif’s linkage
Based on Nasif’s lack of technical proficiency and a reasonable explanation of how he has gotten access to the ‘proprietary’ materials, it seems that he is just an opportunistic shadowy data broker who scrapes dubious content from 3rd parties, tags it with provocative titles, and makes sensational headline style claims about its meaning. It may also be relevant that him becoming a purveyor of ‘secret’ intelligence suspiciously coincides with the 2017-2018 GoFundMe launch of his web hosting service (re-selling IBM hosting) which, interestingly, also uses similar bombastic claims such as:
“The Most Secure Cloud Storage Server in the World. Secure Hosting- Secure High Speed 1Gig Internet- Secure Chat- Secure Photo and Video Storage”
If you need further evidence about the nature of this depository, read Nasif’s Read First NOTICE TO ALL VIEWERS:
“…Please do not publish any of my evidence documents in public or private forums without my written permission. Please do not try to “share” a link to my evidence file folders from this drop box folder to social media pages, groups, or news publications. If you publish anything labeled “Secret” in public, I cannot protect you from legal or criminal prosecution that may follow.
If you want to invite someone to view “George Global” please make that request by email to g.nasif@yahoo.com and make sure that person has followed protocol by first making a donation to the new server so I can give them access. Posting many of these documents is what got me banned 15 times from Social Media, Twitter and FB. Remember this when RT or sharing on FB. Think before you act. Be responsible. All Documents have been vetted as factual and true evidence from the source.”
So, there you have it. You shouldn’t publish any of Nasif’s documents without his permission because he scraped them from 8chan/8kun/4chan and other conspiracy watering holes and now claims them as his IP. But if you do re-publish anything labeled “Secret” from his publicly accessible DropBox archive, he won’t be able to protect you from “legal or criminal prosecution”. Also, don’t forget to ‘donate’ to his business venture in order to get access to the ‘full’ content in this magical archive (which previously was in the public domain). And finally, Nasif himself assures you that he “vetted as factual and true evidence” over 6 TB of data and millions of records.
If you are still struggling with the classification of the content in Nasif’s depository/postings as real or fake, the highly technical illustration below may be of some help.
Image 8: How Nature Says “Don’t Touch”
Credit: Gary Larson’s Far Side Cartoons
References and Sourcing
XRVision Sentinel AI Platform – Face recognition, image reconstruction, and object classification
Copyright 2020 Yaacov Apelbaum, All Rights Reserved.


Did some people actually pay this shyster? They best be cautious when they get a phone call from someone informing them that the caller is their credit card company ready to offer them a lower interest rate or some other dubious scam claim.
Good point, it does read like a scam… You can’t get the ‘full access’ to the 6TB of secret government data and millions of records until you make a ‘contribution’. But that is only until he gets the world most secure social media hosting server up and running on the the IBM cloud. After that, he will take out Facebook. The shady business model aside, the bigger issue here is that he is brokering massive amounts of fake mislabeled content on a wholesale scale.
Where can one get the “XRVision Sentinel AI Platform” that you use to make these illustrative connections? Fascinating!
Hi realgaryseven,
Currently the Sentinel AI is not available to the general public. We do a projects from time-to-time as a public service in order to promote transparency and provide insight into people/events that otherwise would get ignored/suppressed/manipulated by MSM.
I gathered as much from the lack of web info. In any event, your infographics are the best I’ve seen anywhere. I appreciate what you do release. Absolutely first rate.
Thanks for the kind words realgaryseven,
“The simple inherit folly, but the prudent are crowned with knowledge.” – Proverbs 14:18
What do you think about George Webb. He’s got a series of youtube videos that, if ture, ared downright frightening. They seem to paint a picture of the wholse set of troubles directed at Trump seem to be interconnected in a ridiculous degree. Here’s a link exposing Alex Vindman’s twin brother who’s fund got fine 1.3Billion for arms trafficking.
https://www.youtube.com/watch?v=3kiwTP-PP10&t=614s
Hi Peter,
Thanks for your comment. I know little about the topics that Mr. Webb discusses in his videos, so, I can’t offer any valuable opinion about the validity of these theory/connections/persons/organization. The golden rule in intelligence analysis is that no matter how convincing the information is, you have to confirm it through multiple independent sources. Unfortunately, validating these statements would require a signification investment in time and resources, which is something that I can’t afford to do.
Bummer. He spins a very complex yarn, and that alone makes it hard to believe, but he tends to have some pieces get confirmed by later coverage, so it keeps me guessing.
I love what you do in your blog and am always impatiently waiting on the next story.
Staying informed used to mean watching the news every day, maybe also reading the paper.
4th estate, journalism ethics and all that jazz
I never had reason to doubt this until the Trump election.
When is saw accusation of racism, or white supremacy, it seemed unfair, so i decided to dig for a bit more detail. This was like stepping in Alice in Wonderland – The more i looked the more i saw, with most of the pieces being reported so slanted they often painted the reverse of reality and most concerning, being repeated almost identically across most news stations.
That is a clear betrayal by the mainstream news. I get that the internet is forcing them toward clickbait and short cycles, but that’s largely irrelevant if the result is mis-information.
Staying informed today takes more time than most citizens have, and that is being used to herd our culture down paths we have no desire to go.
Worse yet, the ideas being foisted onto the public are nothing short of destructive.
This is why sources of information like you are so important.
Thank you for doing this.
Thank you for the kind words Peter.
When evaluating any report/reporter, I try to ask the following questions:
1. What is the source of the report (using statements like “speaking on condition of anonymity…” can be categorically classified as manipulative)?
2. Why is the reporter sharing this information and not another story (is this part of a broader narrative)?
3. Are there any flaws in the information (even a small flaw can disqualify the whole story)?
4. How did the reporter learn this information and why were they chosen by the source?
5. Does the reporter have documented history of dishonesty?
6. How is the reporter benefiting from transmitting this information?
7. What is the age and gender of the reporter (attractive younger female reporters are more likely to exchange sexual favors for high value information)?
8. Is the reporter transmitting secret or classified information (typically obtained via some illegal collection and makes them accessories to a crime)?
9. Does the reporter have an emotional attachment to the story?
10. Does the reporter have a pattern of reporting and promoting certain topics?
11. Does the reporter understand the low level details of his reports and can they explain them?
12. Is the reporter promoting an ideology?
13. Is the news organization promoting a narrative that is tied to its corporate interests
14. What did the reporter do before working for the current news outlet?
15. Is the reporter or his family benefiting financially or professionally from the report or source?
16. Who is in the reporter’s social network?
17. Is the reporter using third party experts to prop the story and who are these experts?
18. Is there a revolving door in the news organization where sources become contributors?
19. Is the reporter working for a ‘state’ news agency? (Al Jazeera, RT, the BBC, etc. reflect government propaganda and foreign policy objectives)?
20. Does the reporter have any known character flaws (i.e. committing sexual harassment or shielding another sexual harasser)?
21. Does the reporter have an unusual number of scoops and/or industry awards (could be an indication of some sort of a Mephistophelian contract)?
Once you take these and other questions into account, it’s easy to evaluate information processors like CNN, NYT, or Google and classify them as propaganda mills. You can also apply these same evaluation methods to independent sources like blogs.
In regards to specifically what Mr. Webb is reporting, I don’t know what are the sources for his claims or the type of rigor he applies to the analysis. It’s possible the he/other analyst collect primary materials and validates them thoroughly. But doing this type of work on regular basis would require either high level of software automation or a sizable intelligence team. Again, this can go either way, I just don’t know.
In general, (1) truth tends to be rich in detail, have a organic look and feel to it, and be supported by a variety of people and events, (2) made-up events on the other hand, tend to be more linear, syntactic, and feature a skeletal set of characters. The reason for this is that in case 1, the plot-line is generated by the universe, in case 2, the plot-line is generated by someone with a constrained imagination and resources.
I’m not sure what the long term solution to the news reliability problem is. I think that when it comes to the social media/internet platforms, we should either force them out of the news collation and classification business or regulate them as news outlets. They should be forced to choose one or the other. If they chose to become news outlets, and the likes of Google/FB continue to sensor search results, then they should be open to civil claims like civil rights violations, hate crimes, and discrimination. There is also no reason why entities like Google—which are a classic monopoly—shouldn’t be broken up to multiple business units.
As far as MSN, its little more complicated because of historical precedent, but considering the fact that they no longer report the news but manufacture it, opening them up to a corporate and personal liability claims could put them back on track. Either way, I think that we need to re evaluate the definition of freedom of the press and enact new laws regarding the use of protected sources and the ability to publish classified/illegally obtained information. If a news outlet can’t clear most of the questions in the list above, cite their source for the story, or use only legally obtained information, they shouldn’t publish the piece.
Dear Yaacov, The ghastly situation with the Trump Impeachment “hearings” is making me wonder what is so damned important about getting rid of President Trump. I mean, they hated GW Bush, too, calling him Hitler. Why are the anti-Trumps so desperate that they will literally hold up the business of Congress (in some ways not a bad situation) to throw crap at the wall day after day, hoping at least a little sticks. Of course the malignant press is colluding in this mess too. But WHY?
I am thinking this all dates back to the 2008 Presidential campaign, where the Republicans put John McCain up against the inexperienced, but lusciously-colored Barack Obama, about whom very little was known. Didn’t John Brennan conduct some sort of operation to hide/destroy the details on Obama’s passports and other records, like his supposed foreign birth which would have him ineligible to run for the Presidency? (I myself think photographic evidence shows Frank Marshall Davis to be the Dad, which would make Barry/Barack a thoroughly Natural-Born Citizen, embarrassing if true, but not a real crisis if revealed IMO) Is there a way to unearth his college records, supposedly accepted as a foreign student at Occidental and then transferring to Columbia; getting into Harvard LS with special action of Arab potentate etc. Even bossy Hillary Clinton stood aside as BHO hove into view. All these mysterious cover-ups of important details allowed Obama to be elected easily. Lots of shadowy money helped him, and is available to assist in electing Congress critters, too. Ukraine? John McCain had his fingers in there, too.
This is why when Trump started questioning Obama’s origins back years before he began his run in 2015, the swamp denizens came out swinging. They had to, because if Barack Obama is someone different from what he says he was, his whole Presidency is a LIE. Every single entity is implicated — Democrats, Republicans, SCOTUS, the media. Hillary’s email scandal or inaction at Benghazi when the Ambassador was murdered will be as nothing compared to this potentially nation-ending crisis.
Hi Lady Sid,
There are probably many contribution factors as to why our political discourse has become so toxic. I’m not intimately familiar with some of the point that you bring up so I can’t comment intelligently about them. I personally think that the main reason for this is that President Trump’s election spelled the collapse of the Clinton dynasty.
Over the years the Clintons have formed one of the most powerful political dynasties in US history (even more powerful than the Kennedys). Using official office and foundation, they created a vast network of media, business, politics, and foreign actors that spanned the globe. With this powerful network of clients the Clintons became a one stop shop for ‘getting stuff’ done. If you were a foreign leader and needed some sort of a favor, there was a proven method to achieve your goals. You didn’t have to guess, pray, or peruse complex lobbying efforts with congress. All you had to do was reach out to someone in the Clinton inner circle, donate xx millions to the foundation, get your 5 minutes with HRC or BJK, who in turn, would take care of your problem. The various methods of pay-to-play were discrete, effective, and profited both parties (and everyone who brokered this transaction).
Organization like Google liked this models because it essentially gave them direct access to the throne and the ability to operate as a monopoly/sovereign nation without any oversight and scrutiny. Organization like NYT and Saros counted on the fact that they would continue to harvest the sweet fruits of this relationship through direct access to policy, sourcing, commercial benefits, etc.
And then HRC lost. “Now there arose a new king over Egypt, who knew not Joseph.”, and with one swoop the old tried-and-true network of mega-doners, fixers, lubricators, lobbyist, contractors, and beneficiaries lost their influence. History teaches us that dynasties never go down without a bloody fight to the death, this is the reason why the impeachment push has been so relentless over the past 3 years and will most likely continue in 2020 as well.
Thank you for your fine work!!! You inspired me to do a brief post & quote your wisdom from the comments section liberally there…God Bless you & your ongoing relentless pursuit of the Truth!
https://specialconnections.wordpress.com/2020/01/13/wise-evaluation-of-news-reports-reporters/
Thank you Valerie for your kind words.
This guy George M nasif is a scam. I have informations that can prove it. He’s also psychotic and involved in many fraudulent acts. His work is illegal and unethical.
Hello! Can you use the same AI software to prove that George Nasif is dropping his fraudulent information on a telegram channel called The Great Awakening? He’s collecting bitcoin. I know it’s him but I would love a way to prove it to stop the spread once and for all.
You can safely disregard the content on the Great Awaking. It’s laced with disinformation. One of the pictures seen there shows a two part image of Hunter with what appears to be an under age Asian girl next to a stripper pole. Only one of the images is of him and the girl facing him is not under age (see a few of the images from the original sequence below). The second image has been scrapped from an Asian site and is not of Hunter.
https://apelbaum.files.wordpress.com/2021/01/stripper-session.jpg
Yacoov, thanks for taking the time to reply! I’m seeing a lot of people share it who I consider intelligent people and it pains me that they aren’t vetting the information. Based on the files that have been shared on that telegram channel, do you think Nasif is behind it?
Yes, that is the problem with well produced disinformation, is that It’s plausible and believable. Regarding Nasif, it’s possible that he did scarp it, he is a known fabricator and has been promoting fake content for years.
https://apelbaum.wordpress.com/2019/11/06/the-raise-of-the-real-fake-data-brokers
FYI, the image of the man who is supposed to be Hunter and the child in the bathing suit came from a site called Viper. The original post was titled: “【閲覧注意】ハンター・バイデンのPCから流出した画像、ヤバ過ぎる “[Reading notice] Image leaked from Hunter Biden’s PC, too dangerous”. The Viper post was also mirrored on a site called Antenna about same time on 12/30/2020. The Asian sourcing and publication timeline also suggests that this could be related to the G-TV activity.