|
Victim |
Date |
# Accounts |
What was Breached |
|
MySpace |
2006 |
360 million |
User account records, email addresses, usernames, and passwords |
|
TJX Companies |
2007 |
90 million |
Driver’s license numbers, credit and debit card numbers, names, and addresses
One of the biggest thefts of consumer data in the United States, affecting the parent company of several major retail brands, including Marshalls, T.J. Max and Home Goods |
|
National Archive & Records Administration |
2008 |
76 million |
Names, contact information, and Social Security numbers of U.S. military veterans |
|
Heartland Payment Systems |
2009 |
130 million |
User account and credit and debit cards details |
|
Lincoln National Financial Securities |
2010 |
1.2 million |
User account database including user names and passwords |
|
Sony online entertainment services |
2011 |
102 million |
US user login credentials, names, addresses, phone numbers, and email addresses The credit-card data of approximately 23,400 SOE European users |
|
Epsilon Marketing |
2011 |
250 million |
Email addresses of customers ofmajor retailers, banks, hotels and other companies including Best Buy, JPMorgan Chase, Capital One Bank and Verizon |
|
|
2012 |
165 million |
Passwords, user names, account details |
|
Dropbox |
2012 |
68 million |
User IDs and passwords |
|
Yahoo |
2013 |
3.5 billion |
Names, dates of birth, email addresses, security questions, and answers and passwords. |
|
Target |
2013 |
110 million |
Contact information, full names, physical addresses, email addresses, telephone numbers, credit and debit card numbers |
|
Tumblr |
2013 |
65 million |
User ID, passwords, and email addresses |
|
Evernote |
2013 |
50 million |
Email addresses, usernames and passwords |
|
LivingSocial (an Amazon Company) |
2013 |
50 million |
Names, email addresses, birth dates, and passwords. |
|
Sony Pictures Entertainment |
2014 |
> 45K |
Social Security numbers and scanned passports belonging to actors and executives, internal passwords, unpublished scripts, marketing plans, financial and legal information and 4 unreleased Sony movies affecting the company’s 6,800 employees plus an estimated 40,000 other individuals the company had paid over previous years. Rival Hollywood studios got a detailed blueprint of Sony Pictures’ accounts, future plans and internal workings |
|
Home Depot |
2014 |
56 million |
Customer credit and debit cards |
|
Rambler |
2014 |
98 million |
Email addresses, user details, and passwords which had all been stored in plaintext |
|
Anthem (formerly WellPoint) |
2015 |
80 million |
Entire customer database including names, addresses, dates of birth, Social Security numbers, and employment histories |
|
FriendFinder The FriendFinder network, comprising Adult FriendFinder, Penthouse.com, Cams.com, iCams.com and Stripshow.com |
2016 |
412 million |
Entire user database, including names, addresses, email addresses, and phone numbers. This was a similar breach to that which affected the “Have an Affair” Ashley Madison dating service in 2015 |
|
|
2016 |
117 million |
The 2012 breach only discovered in 2016. Names, emails, passwords, complete user professional profiles |
|
Equifax |
2017 |
145 million |
Names, Social Security numbers, birth dates, street addresses and, in some instances, driver’s license numbers |
|
Marriott/Starwood Hotels |
2018 |
500 million |
Names, mailing addresses, email addresses, credit-card information, dates of birth, passport numbers, and Starwood Preferred Guest accounts |
| Capital One | 2019 |
106 million |
Credit card applications from consumers and small businesses, credit score, SS numbers, names, addresses, ZIP codes, phone numbers, email addresses, birthdates and self-reported income |
| Evite | 2019 |
100 million |
Names, email addresses, passwords, and IP addresses |
| American Medical Collection Agency | 2019 |
20 million |
Social Security numbers, dates of birth, payment card data, and credit card information |
Table 1: Sampling of successful cyber attacks and the resulting data breaches from 2006-2019
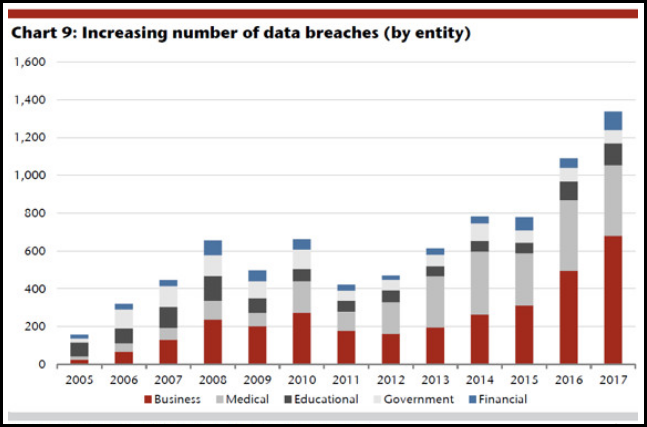
Chart 1: Data Breaches by verticals – Source Jefferies, Identity Theft Resources Centre
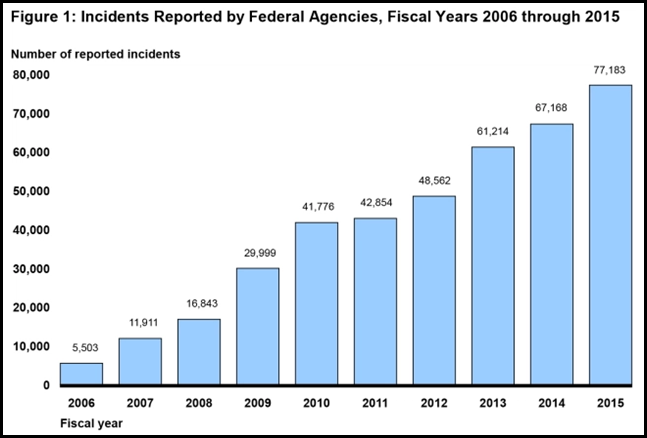
Chart 2: Incident of cyber attacks against the Federal government – Source: GAO Analysis of the US Computer Emergency Readiness Team and Office of Management and Budget
The paradoxical end result of these data breaches is that every year organizations increase their cyber security budget without any assurances that the expenditure will yield a return on the investment. To an outsider, this ritual must appear similar to the practice of throwing a virgin into a volcano in the hopes of quieting its rumbling. It seems that information security, as opposed to other types of technology spending, is just a budgetary black hole.
So why is it so difficult to prevent or even slow down cyber attacks? I think that it boils down to these two reasons:
- Lack of executive and BOD accountability and legal consequences for a data breach
- Use of outdated cyber defense models like concentric fortress security
Point 1 is a regulatory issue that should be addressed through legislative channels, so I’m not going to elaborate on it here. My take on this problem is that if legal enforcement worked properly, then it is likely that the first CISO that gets handed a hefty prison sentence for negligence, would also be the last CISO to allow his company to get hacked (the same also applies to the rest of the C officers and the BOD).
As far as point 2, the problem is a little more complex, but also easier to remedy. The issue with using an outdated static fortress models is that they overly abstract military practices that were developed/honed over thousands of years for a specific set of war scenarios and contort them to fit our virtual information security needs. This includes embracing defensive concept that utilizes multiple concentric-overlapping-sequential layers of protection akin to a moat, a drawbridge, a portcullis, a guardhouse, bastion walls, guard towers, ramparts, a keep, a treasury, and a well trained, armed, loyal garrison.
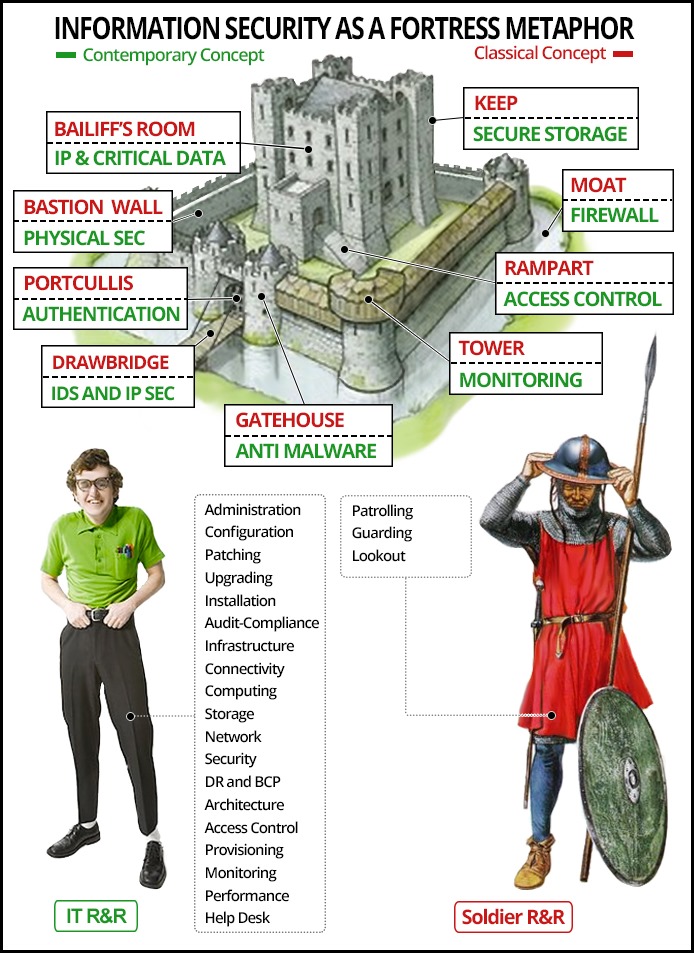
Image 1: Information security R&R and the traditional fortress and sentry analogy
A fortress is an intuitive analogy for the enterprise but it is an overly hyped and misleading one. Beyond a few shared objectives such as parameter security, surveillance, and physical access to a facility, cyber defense has little in common with traditional military fortifications. This is because information security deals with virtual threats and its attack vectors have a few equivalents in the physical world (see Table 2).
|
# |
Contemporary Assets & Threats |
Traditional Assets & Threats |
|
1 |
Contraband (weapons, alcohol, drugs, etc.) |
Contraband (mostly weapons) |
|
2 |
Unauthorized individuals |
Unauthorized individuals |
|
3 |
Infrastructure (power, water, Telco, etc.) |
Water and food storage |
|
4 |
Malware and Ransomware |
|
|
5 |
Financial data |
|
|
6 |
Intellectual property and trade secrets |
|
|
7 |
Computing, network, and storage resources |
|
|
8 |
Insider and trade information |
|
|
9 |
Strategic plans such as M&A |
|
|
10 |
Litigation information |
|
|
11 |
Customer and partner data |
|
|
12 |
PII (i.e. SS, BOD, driver license, address) |
|
|
13 |
R&D plans |
|
|
14 |
Medical and genetic data |
|
|
15 |
Biometric data |
|
|
16 |
Opposition and political research |
|
|
17 |
Business operations data |
|
|
18 |
Credentials and authentication data |
|
|
19 |
Credit card, PIN, and chip data |
|
|
20 |
Account details |
|
|
21 |
Patient information |
|
|
22 |
Banking and financial data |
|
|
23 |
Classified military, defense, and intelligence data |
|
|
24 |
Academic information |
|
|
25 |
Insurance and claims information |
|
|
26 |
HR, compensation, and, employee data |
|
|
27 |
Financial donor information |
|
|
28 |
public health and safety information |
Table 2: Threats and targets in the counterparty enterprise vs. the legacy fortress
Traditionally, fortresses were besieged and breached via one or a combination of these 7 methods:
- Scaling the walls (with assault ladder or a movable tower)
- Punching through the walls (with a battering ram, trebuchet, or cannon)
- Entering the surreptitiously or Trojan style
- Bringing the wall down by digging a tunnel underneath and setting the shoring timber on fire
- Inflicting damage on the fort structure and on the inhabitants via catapults or other projectiles
- Spreading disease by catapulting infected animals or bodies into the fortress
- Stopping the food and water supply (or poisoning it), and using psychological warfare against the inhabitants
This same doctrine that made massive layered fortifications synonymous with impregnability was used by France in the Maginot Line and proved to be a huge tactical and strategic disaster. Between 1929 and 1936 the French built a massive line of concrete and steel forts and tunnels along the German border with France between Switzerland and Luxembourg. It was constructed to defend France from any future WWI style attacks from Germany. So instead of attacking the heavy fortifications, the Germans simply went around them and invaded France through Belgium, exactly as they had done in 1914.
All the motorized artillery turrets, tank traps, bunkers, periscopes, and other gimmicks designed to impede the advance of the German army turned out to be useless when a million soldiers and 1,500 tanks led by Guderin and Rommel flanked this supposed impenetrable chain of forts and blitzkrieged their way to some renowned Parisian fine dinning and cabaret entertainment.
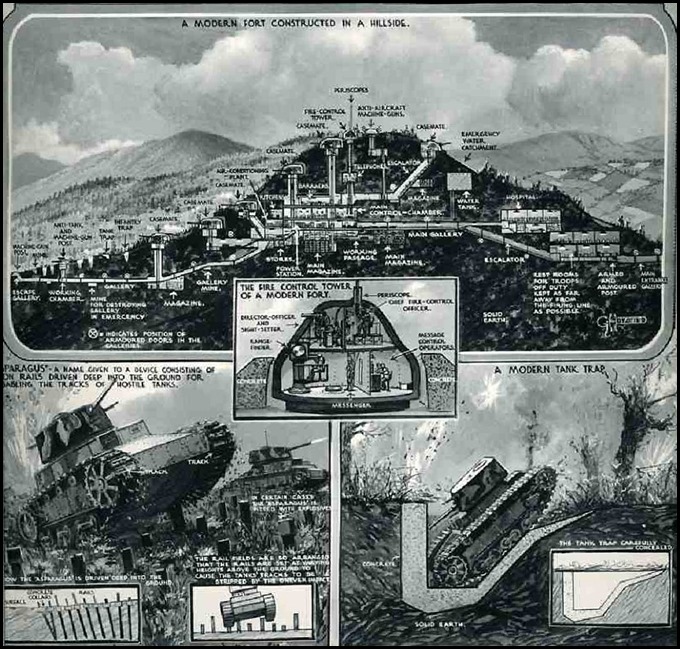
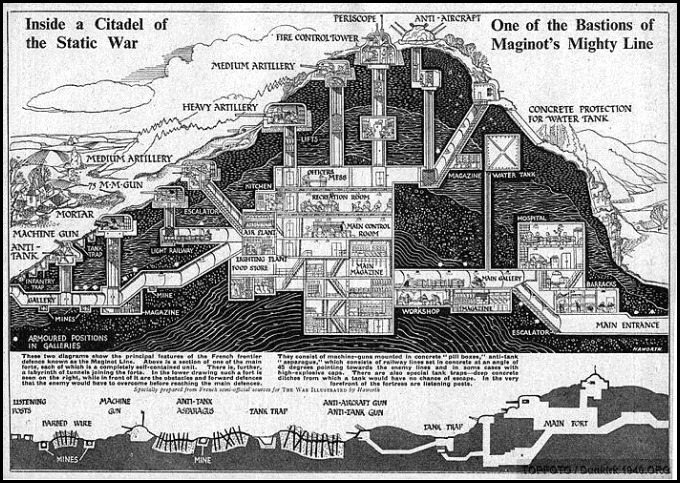

Image 2: The Maginot Line fortresses system and some Parisian cabaret entertainment
Today, many of the leading cyber security vendors continue to sell the same fortification concept using flowery language such as “impregnable defense” or “defense in-depth” or “multitier lines of defense”. The promise of all of these protective marvels is that increasing the number of your defensive lines is guaranteed to shield your enterprise from threats and the latest cyber attack.

Image 3: The Multi-Layered Security Fortress – Source Digital banking software Q2
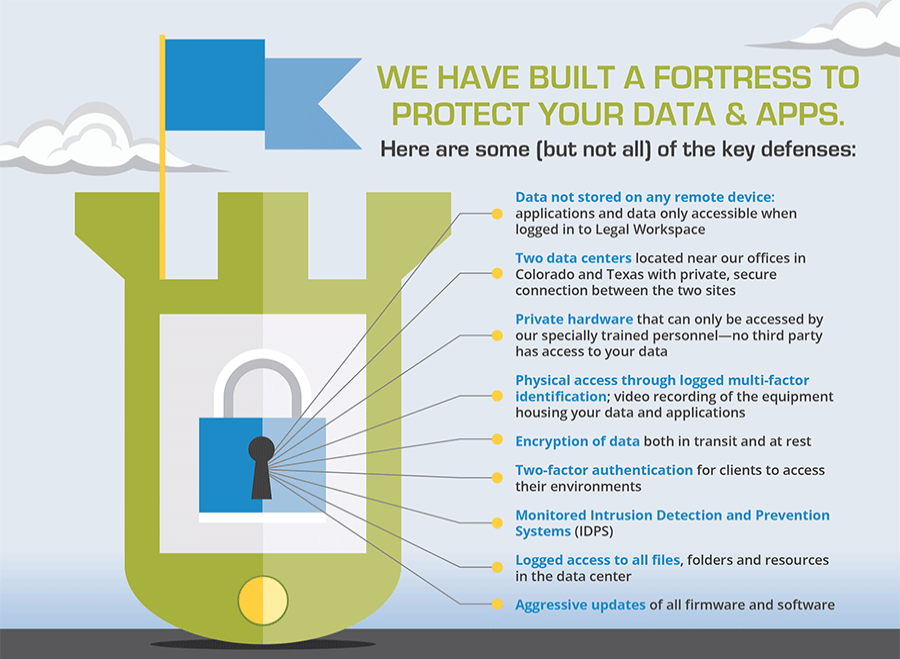
Image 4: The Data Fortress – Source Legal Workspace
A Dynamic Threat Theater
The cyber threat landscape evolves daily, but the enterprise defensive architecture continues to rely on countering ancient seige techniques. The hacker skill set and the resources needed to penetrate a high valued target no longer require highly specialized expertise, lengthy planning, or expensive zero day exploits. A simple phishing technique can now do the job just as effectively.
The prevalence of social media platforms in our daily lives and their use as line-of-business applications (i.e. LinkedIn for HR and recruiting), enables attackers to quickly conduct reconnaissance and exploit their targets directly and in real-time. The use of personal devices in the workplace provides payload delivery vectors and allows the attacker to use them to bypass external facing security measures like firewalls and pivot to the internal network. The use of Bluetooth to connect mobile devices allows an attacker to collect the contents of address books and capture phone conversations. Free Public Wi-Fi offers ample opportunities for attackers to collect credentials from corporate users while they are commuting to work or are off-site, and a glut of mobile apps provides an endless source for spyware and malware distribution channels.
Yes, democratization has finally reached Hackerdom. These days, you don’t even need to write your own malware; you can just download a free fully functional phishing kit from various depositories, customize it, and launch your campaign in minutes. All this gives an attacker the ability to cruise into the enterprise with relative ease, completely bypassing all of the layered security controls en route.
Behold! The Adaptive Secure Architecture For the Enterprise (SAFE)
The majority of the current cybersecurity models are still based on the erroneous game-theory arms race assumption that continuously bulking up your defensive elements (like upgrading to an ASA device or endpoint security client) will stop an intruder. The concept is not dissimilar to using the club to secure a Lamborghini. However, these models incorrectly rely on idealized assumptions about the decision making process of the attacker and their ability to find and exploit the endless number of vulnerabilities in your enterprise.
The traditional approach of adding additional security strata to the already tangled web of unmanageable layers is unruly and unsustainable. If you are still not convinced, the root cause analysis of the breaches in table 2 shows that all of the platforms breached had up-to-date antimalware, segmented networks, rule bases access control, multi-factor authentication, firewall, IDPS, etc. The hacking statistics clearly demonstrate just how ineffective these defensive strategies are against an Advanced Persistent Threats.
Thunderbolt and Lightning Very, Very Frightening
So, instead of succumbing to more security by fear and continuing to throw more good money after bad into the security furnace, I propose an alternative to the static fortress defense doctrine. This concept is based on adaptive security. It relies on continuous monitoring, active threat quantification and assessment, traffic anomaly detection, response prioritization, and real-time remediation. I call this design reference the Secure Architecture For the Enterprise (SAFE) framework.
At the heart of the SAFE framework is the assumption that the security of the enterprise can never be up to par and that most organizations can’t afford the latest and greatest in cyber security services. The model also accounts for all of the typical IT and InfoSec vices, sins, and transgressions found in your day to day workplace such as weak and reused passwords, usage of personal devices at work, unpatched systems, buggy software, etc.
The SAFE framework doesn’t focus on traditional defensive elements like malware protection, but rather, it leverages real-time AI based monitoring, a decision support system, and autonomous identification o risky areas requiring immediate attention. At a high level the SAFE framework is comprised of a real-time BI dashboard that analyzes and reports patterns of inbound and outbound traffic in your systems and users. This dashboard, in turn, is powered by real-time RBE, CEP, and a BigData engine that detects and flags anomalies on your network (such as uncharacteristic use of encrypted traffic). The decision support system (DSS) integrates feeds from various internal IT system such as patching, upgrades, VPN logs, firewall logs, event logs, etc to give you a current situational awareness of your security posture. The DSS then uses an expert system to flag and prioritize remediation actions as they apply to the various vulnerabilities or exploits in progress.
When building a security solution using the SAFE framework, you don’t have to fix/upgrade/sunset all of your systems at once. You can instead rationalize your security priorities and concentrate on the areas with the highest risk of attack. The good news about using the SAFE framework is that you don’t have to spend a fortune on over-hyped preparatory protection services and commit to one vendor or another. You can easily build your security architecture with a relatively small in-house team using mostly COTS and open source components.
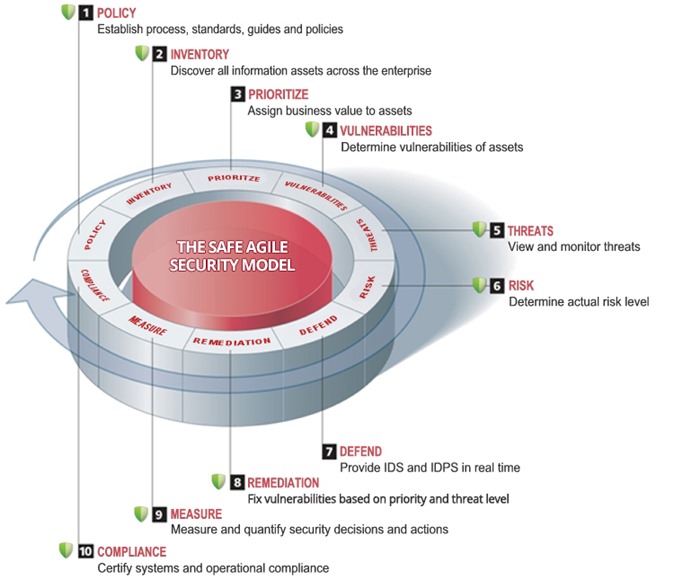
Due to the modular and loosely coupled nature of the SAFE framework, you don’t even have to own all of the inventory of the building blocks. You can start small and expand over time. This approach also allows you to customize your solution to your industry vertical and business needs. Finally, because the SAFE model uses concepts from the software development life cycle (SDLC) such as iterative development, feature prioritization, bug tracking, etc., it allows you to prioritize and gradually adapt and move iteratively between the 10 elements that comprise the framework.
Image 5: The SAFE life cycle security model focuses on the evolving threat matrix
Cyber attacks don’t just mysteriously materialize out of thin air; they follow a specific life cycle of reconnaissance, planning, vulnerability assessment, exploit, and post exploit steps. Far from being helpless, we can intercept and circumvent most of these attacks during any of those steps. Integrating the concept of a cybersecurity kill chain into the SAFE model could even further enhance your ability to prevent, disrupt, or stop any attack on your enterprise in near real-time.
© Copyright 2019 Yaacov Apelbaum, All Rights Reserved.