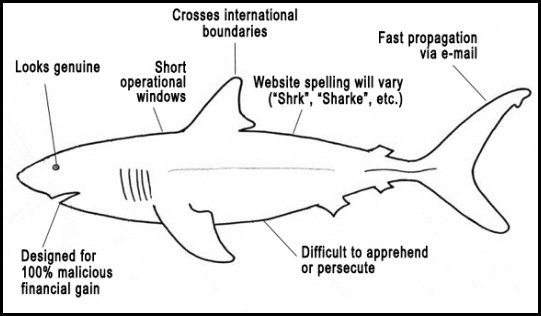
The Anti-Virus Virus
Another interesting observation—which is not without its irony—is that large vendors such as Microsoft are completely unaware of the malware distribution platforms and are aggressively purchasing advertising space on these sites.