Several weeks ago, my wife was searching online for the words to one of Shel Silverstein’s poems. With the Internet within closer reach than the bookshelf in our den, she went to Google and typed in the key words “shel silverstein pancakes,” and within 0.32 seconds got several matching results (Image 1).
Image 1: Google Search Results
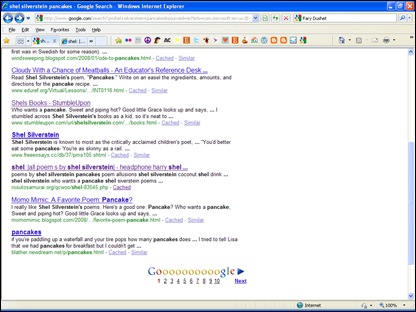
She clicked on one of the top results on the first search page and almost instantly got prompted by a message box (Image 2) indicating something to the effect that her computer contained various signs of viruses and immediately needed to be examined. It then offered an option to perform a security scan.
Image 2: Infection Warning
We keep our OS well patched and the anti malware software up to date, so she decided to decline the offer and clicked on the cancel button. The message box went away but then another screen popped up telling her that her system was being scanned for viruses. Thinking that she may have clicked the OK button instead by mistake, she waited for the scan results.
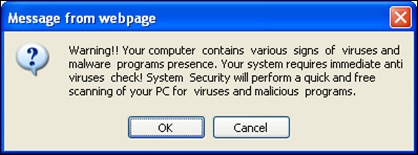
Image 3: Infection Warning
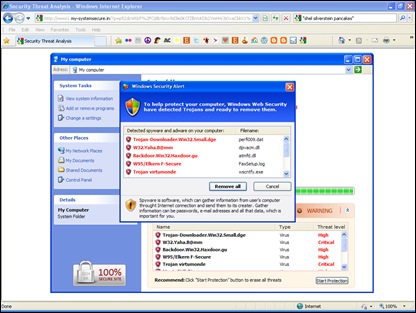
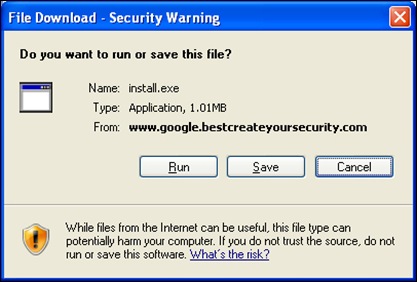
When the scan was complete (within 15 seconds or so), she was informed that her computer indeed had been infected with several nasty viruses (Image 3) and that she would need to download and install the offered security program in order to remove these viruses (Image 4).
Image 4: Malware Download Dialog Box
At that point, she realized that malware itself was communicating with her and trying to install itself on her machine. She clicked the Cancel button dialog box but instead of terminating the installation, she was taken back to the first message box which told her again that her computer contained various signs of viruses and needed to be examined. Essentially, she was trapped in a loop, unable to close the Browser. After another round of scans and cancelations, she decided to bring up the Task Manager and terminate the process from there.
Several days later during dinner, she happened to mention her run-in with the malware and I made a sly comment that these are the rewards we reap for hanging around dubious websites. She took offense. “Dubious web sites?” she said, mocking me, “this was the fourth entry on the first search results page of Google. How ‘dubious’ can that be?”
I found it hard to believe that the writers of the malware were clever enough to sneak by the Google filters and make it to the top of the first search results page. I executed the same search she did just day previous. My search results were almost identical, but ironically her malware link had by then moved a step upwards in relevance.
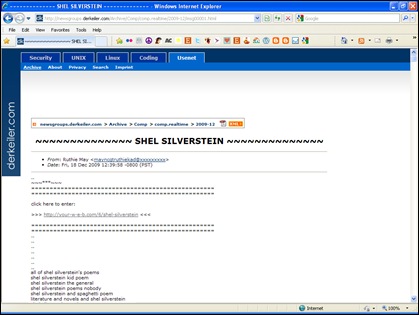
Instead of clicking on the link I copied its URL and went directly to the website (Image 5)
Image 5: Actual page with download link and keywords
The web site turned out the be a newsgroup called derkeiler.com, which is one of the most popular and most heavily advertised mailing list archives on the net. Looking closer at the page, I found the following:
- At the top was the bold title “SHEL SILVERSTEIN”
- Below the title was a bogus poster name in the format of name@xxxxxxxxx.com
- Next was a link which activated the malware download script.
- Finally at the bottom of the page was an extensive list of hundreds of keywords that were associated with the works of Shel Silverstein.
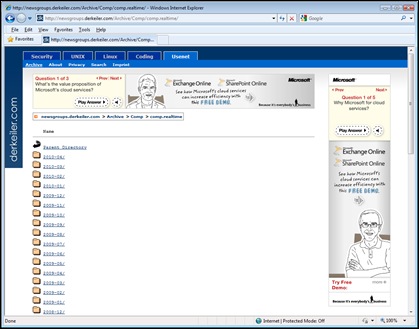
I looked at the parent directory page and found a long list of dated directories (Image 6).
Image 6: Parent Directory (note heavy commercial advertising)
Each one of these directories contained dozens of linked entries. After randomly clicking on about 30 links, I determined that most of them were identical to the Shel Silverstein page (Image 5) in terms of content, layout and malware activation functionality. I checked out several other public newsgroups and “personal” web sites to compare. It appeared as if indeed there was a method to this madness.
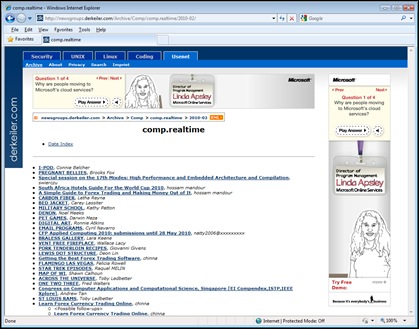
Image 6: Sample directory contents with links to malware download
So what does it all mean? Well, the modus operandi seems to be as follows:
- The creators of the malware install the program on a large number of personal websites (some have been breached and others are dedicated). One example is Rosuto Samurai which was allegedly created to support fantasy gaming but in reality never had any content beside the malware.
- They then proceed to automatically create hundreds of highly popular topic pages (i.e. Ipod, Shel Silverstein, movies, etc.) in newsgroups and mailing lists, each of which contains a link to the malware download website.
- Each of the pages also includes a large list of keywords (generated by some machine learning process) that are associated with the topic. The purpose of the keyword list is to increase the radar signature for the search engine spiders.
- The search engines find these individual topic pages, traverse the keyword list and algorithmically determine that all the words are related. They also see the hyperlinks and postings on each page (which makes them appear like miniature websites) and as a result assign them a top rating—which to the user, translates as top hits in topic search results.
The outcome of this strategy is cheap and effective SEO penetration and viral dissemination of viral contents (no pun intended) via top search results.
Another interesting observation—which is not without its irony—is that large vendors such as Microsoft are completely unaware of this practice and are aggressively purchasing advertising space on these sites, (including ads for their security products). Clearly, this is being done without the realization that they are actually sharing living space with some of the most aggressive malware distribution centers.
Stay tuned, in a future posting, we will dive deeper to see who is actually developing and marketing this malware.
Quis Custodiet Ipsos Custodes?
© Copyright 2010 Yaacov Apelbaum All Rights Reserved.

2 thoughts on “The Anti-Virus Virus”