Romantic scams a la Casanova style, have been around forever, but the Military Romantic scam variant has only taken off since the advent of social media and online dating. According to a 2018 BBB Online Romance Scams study, since 2015, this form of cybercrime has become a 1 billion dollar industry in the US alone. The lifecycle of this scam is well documented and understood, but the low-level details and logistics have never been made public. Little is known about their operations, networks, structure, finance, technology, and their relationship with law enforcement and politicians. The public’s perception of cyber scammers is that of modern-day pirates, an amorphous entity shrouded in mystery that operates overseas with what appears to be complete impunity from prosecution.

Two victims of military romance scams (L-R) Kate Roberts and Esther Ortiz-Rodeghero.
The impact of military romantic scams on the victims, who are typically older women living on a fixed income, is devastating. Some end up going into debt to pay the scammers; others lose their entire life savings. To add insult to injury, many of the victims continue to be blackmailed and forced into committing crimes like trafficking counterbid long after they discover that they have been defrauded. This can happen even if they try to terminate their communications with the scammer. Any compromising information such as sexually explicit material, family, legal, or medical information the victim shares about themselves will be used subsequently by the scammer to continue to exercise leverage on the victim through blackmail. Due to the international nature of these scams and the social stigma they carry, most victims have no legal recourse nor a chance of ever recovering their losses.
So in the spirit of Proverbs 31:8-9 “Speak up for those who cannot speak for themselves…” I’ll try to pull the curtain back on one military romantic scam and perform a deep dive into its inner workings and its perpetrators.
Military Romantic Scams 101
At its bare bones, the military romance scam has several variants, all of which revolve around repurposing images of some serviceman or woman and using them to create a fake profile on a social media or a dating site, then reaching out to a victim and defrauding them.
As can be seen from Image 1 and Table 1, a single set of stolen images can become a source of dozens of fake identities and over 900 concurrently running scams.
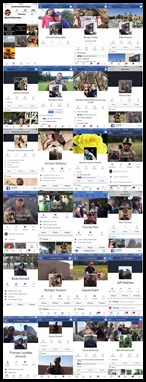

Image 1: (L-R) The 49 personalities of Richard Canon and 12 other stolen identities used in concurrent romantic scams.
|
# |
Fake Name |
Running Scam Count |
|
1 |
Richard Williams |
36 |
|
2 |
Burks Richard |
27 |
|
3 |
Richard Tonsom |
11 |
|
4 |
Canon Hendryx |
16 |
|
5 |
Jimmy Bernett |
24 |
|
6 |
Richard Canon Miller |
12 |
|
7 |
Johnson Smith |
15 |
|
8 |
Richard Canon |
25 |
|
9 |
Canon Richard |
28 |
|
10 |
Thomas Lavallee (Richard) |
18 |
|
11 |
Richard Thomas |
11 |
|
12 |
Thomas Rick |
23 |
|
13 |
Jeff Mathew |
15 |
|
14 |
Thomas Hunter Richard |
25 |
|
15 |
Charles Richard |
19 |
|
16 |
Seth Berman |
10 |
|
17 |
Romos Johnson |
17 |
|
18 |
Mark Brandon |
10 |
|
19 |
Richard Wilson |
19 |
|
20 |
Mata James |
26 |
|
21 |
Thierry Pienaar |
16 |
|
22 |
Sherman Massingale |
27 |
|
23 |
Brain Kobi |
15 |
|
24 |
Elijah Grayson |
19 |
|
25 |
Richard Canon Martin |
22 |
|
26 |
Richard Chocktoot Kenneth |
10 |
|
27 |
Mark Richard |
39 |
|
28 |
Richard Smiff |
16 |
|
29 |
Ballantyne Richard |
9 |
|
30 |
Burks Richard |
13 |
|
31 |
Richards Jack Hanan |
20 |
|
32 |
Richard Billy |
27 |
|
33 |
Randy Moore |
32 |
|
34 |
Richard Steven Nelly |
16 |
|
35 |
William David Mark |
25 |
|
36 |
Larry Brent Richards |
23 |
|
37 |
Cannon Richard |
33 |
|
38 |
Richie Arrow |
27 |
|
39 |
Sivewright Richard |
1 |
|
40 |
Richard Thorpe |
15 |
|
41 |
Richard E Garlock |
28 |
|
42 |
Richard Clark |
24 |
|
43 |
Froylan Richard |
17 |
|
44 |
Canon J Richard |
14 |
|
45 |
Richard C Brain |
30 |
|
47 |
Canon M Richard |
21 |
|
48 |
Ryann Camryn |
19 |
|
49 |
Cannoon Richard |
13 |
|
Total scams for image |
922 |
|
Table 1: One of the hundreds of concurrent scams using the same image with different name variations
Once the fake online profile is created, the scammer will then pursue certain victim demographics and concentrate their efforts on a previously proven cross-section of susceptible individuals—for example, a divorced or widowed woman over 50.
After the initial contact with a victim, the scammer will then engage in a trust-building campaign that can take weeks or months. As part of this process, the scammers will transmit to the victim a wide range of collateral that can include a fake military ID, service photographs, additional social network images, and even address and property information about their fake residence.
The emails, text messages, and step-by-step logic used in these exploits are all based on hundreds of previously tested and successful scams. This makes their decision trees robust and the playbooks plausible and effective. Also, because the operator doesn’t have to waste any time on trial and error approaches, improvisation, or real-time content creation, they can effectively run dozens of concurrent scams by just selecting some template-based material, such as handwritten love letters, and minimally customize them to the specific victim.

 Image 2: An example of template-based collateral ready for customization and a fake military ID with typical errors that include wrong service branch, rank mismatch, capitalization errors, mixed font use, inconsistent letter bolding, a mixture of imperial and metric units, and reuse of DOG TAG numbers from other fake IDs.
Image 2: An example of template-based collateral ready for customization and a fake military ID with typical errors that include wrong service branch, rank mismatch, capitalization errors, mixed font use, inconsistent letter bolding, a mixture of imperial and metric units, and reuse of DOG TAG numbers from other fake IDs.
The Psychology
Two major contributing factors that make romantic military scams so effective are the link between our perception of authority (e.g. people in uniform) and the sense of affinity and closeness we attribute to written communications. In a paper titled An Attributional Extension of the Hyperpersonal Model that analyzes the relationship between computer-based communications and the willingness to disclose intimate information, the authors conclude that:
“…In the experiment, participants were randomly assigned to a face‐to‐face or computer‐mediated interaction with a confederate who made either high‐ or low‐intimacy self‐disclosures. Results indicated that computer‐mediated interactions intensified the association between disclosure and intimacy relative to face‐to‐face interactions, and this intensification effect was fully mediated by increased interpersonal (relationship) attributions observed in the computer‐mediated condition.”
The reason why we trust people in uniform is obvious but paradoxically, it seems that we are willing to disclose more intimate details about ourselves via electronic communications than in person. The written nature of these exchanges also adds a level of conviction and earnestness that verbal communications lack. In the case of romantic scams, this results in the victim developing a higher degree of confidence in what the other party says because they view the ‘physical’ text messages, emails, and letters in their possession as proof of sincerity.
The Scam Lifecycle
Regardless of the specific instance, all scams are formulaic and follow a pre-defined lifecycle. Every successful romantic scam has these five sequential phases:
- Establish an online profile and make contact with a vulnerable victim
- Develop a trusting relationship with the victim by exploiting some of their weakness, isolating them, and grooming them
- Learn as much as possible about the victim’s family, background, desires, assets, and variabilities
- Gain access to the victim’s wealth
- Use the victim as a money mole or contraband mover to support other scams
The Law Enforcement Challenge
Traditional crime or terror linkage analysis is expensive, time-consuming, and resource-intensive. It requires dedicated task forces, access to fused HUMINT, GEOINT, MASINT, SIGINT, TECHINT, INT/DNINT, real-time surveillance data, and the support of many subject matter experts. Trying to reconstruct a modern criminal or terror network is not a straightforward matter because these networks don’t follow the classical organized crime models and rigid hierarchical structures.
Cybercrime networks and operators are loosely coupled and are assembled from among a tight-knit group of ethnically related individuals. They lack a central organization, command hierarchy, official communications channels, and consistent geographical location. They are shielded by local politicians and have the full support and cooperation of senior law enforcement officials. These organizations also utilize a brutal code of loyalty and enforcement that can result in violent punishment for any member who deviates from their assigned responsibilities.
To complicate things further, most of the individuals involved in cybercrime networks are non-US nationals who operate overseas in multiple international jurisdictions. They also effectively utilize countermeasures such as data anonymization techniques, burner phones, and non-traceable payment methods to evade detection and tracking.
So the upshot is that traditional law enforcement and prosecution techniques like the use of informants, bank accounts or assets seizure, and search warrants are mostly ineffective and practically useless.
The Analysis
The ultimate goal of this research wasn’t to locate specific individuals but rather to discover the patterns of life, flora, fauna and lay of the land in this mysterious Kingdom of Scam-Land. I personally have no interest in the individuals identified at all, but I do believe that the information and analytics framework used here would be useful in educating the general public and Western LEA in trying to develop automated and more effective real-time scam-fighting strategies and programs. You can find more details about some of the system components and solution architecture that I’ve used in Illustration 1 and a similar project in a post titled the Mechanics of Deception.
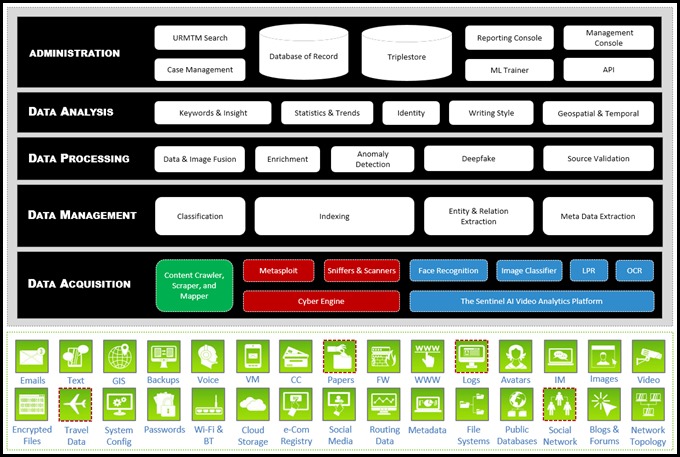
Illustration 1: The system components and solution architecture
The Analytics Framework
To generate the synthetic imagery, interactive dialogs, and wide-scale video and image searches, I’ve utilized the following software tools and machine learning frameworks:
- Facial Imager – AI style-based image generator architecture
- Rasa – Machine learning-based conversation engine
- IBM Watson – Text to Speech Generator
- Audacity 2.3.1 – Open-source digital audio editor and recorder
- XRVision Sentinel AI Platform – Face recognition, facial Indexing, image reconstruction, and object detection
In the machine learning and detection components I’ve utilized: Convolutional Neural, Support Vector Machine, Multi-Task Network Cascade, CAFFE Framework, Haar Cascades, Ensemble of Regression Trees and Learning, P-N and Supervised Learning.
The Process
For the video analytics, I’ve trained the ML engine to detect known scammer characteristics such as certain car makes, fashion brands, accessories, and hand signs. The training of the model included the extraction of known objects (Image 3) as well as seeding the engine with new insight matches that were confirmed to be related to some relevant search topics. So, for example, the results from a search of a person wearing a Gucci belt buckle yield new insight that these individuals also carried certain pattered style bags. So, moving forward, new searches incorporated the patterned bags into the query criteria, etc.

Image 3: A sample of graphic objects used to train the ML-based search engine used to identify fashion and other accessories with known scammer associations.
The object of interest database contained about 6K classified samples. When fully operational, the system delivered an object-matching true detection rate of about 86% accuracy. Over 17 K objects were found and confirmed as relevant (Image 4). The total runtime for all object detection and re-classification was about 9 hours.

Image 4: A sampling of a result set for video and image searches using a combination of “dark skin shade” + “golden watch” objects.
Another type of object classification was used in combination with the BigData engine to locate certain keywords like “prepaid” and identify fashion trends like clothing styles. This included a combinations of more than 23K stop words and graphic object like shoes, shirts, pants, bags, and various accessories. The stop words were scraped from both OCR images, text, and speech to text conversion.

Image 5: An example trend detection involving “distressed Jeans”.

Image 6: An example of a trend detection involving “visible toes” footwear.

Image 7: An example of a trend detection involving car keys suspended from the belt loops.

Image 8: An example of trend detection involves daily wardrobe arrangements, custom-made designer outfits, and shoes belonging to the scammer “Young Black American.”

Image 9: An example of video cataloging and identification of a fashion trend of T. Adugyamfi aka “Billion$King”.

Image 10: An example of a trend detection of a “modeling” pose that is characterized by the subject facing the ground.

Image 11: An example of a trend detection of over 40 types of “hand signal” gestures.
The system flagged the matches, anomalies, and trends and then converted them into insight that was used in more complex queries. This resulted in identifying several hundred trends, such as haircuts, hand signs, body poses, footwear, clothing styles, and color palettes. One interesting anomaly turned out to be a fashion ritual practiced by some of the scammers. They would once a week arrange their wardrobe in coordinated outfits (Image 8) for every day of the week and post them on internal chat boards.
A key component of the searching and linkage strategy was face recognition and face indexing. In total, I’ve indexed about 19K unique faces that constituted the POIs, their friends, families, and associates. The face recognition ran on multiple image sources, such as CCTV cameras, phone cameras, laptop cameras, offline video files, images stored in files, and social media albums and libraries.

Image 12: Usage of Face Recognition to identify an individual in a large collection of images and reconstruct their social and professional network. Featured in the image are “Play Bowy” and his “KVNG DD” team.
All image captures in real-time from CCTV cameras, phones, and laptops were indexed and processed for object and face matches and linkage analysis. The indexed images were then used for geospatial analysis to identify the place and time of individuals and group linkage.
Objects Database
The following is a summary of the objects in the inventory database:
|
Object Type |
Quantity |
Comments |
|
Facial Images |
7,820 |
Used for Person of Interest (POI) searches |
|
IP Addresses |
6,881 |
Computer and other device IP addresses |
| Emails & Text Messages | 38,145 | Individual and group communications |
| Linkages |
19,537 |
Total number of individuals in the network |
|
Cars |
271 |
Make, model, and color |
| License Plates | 156 |
License plate numbers |
|
Image Patterns |
1,150 |
Used for entity searches |
|
Phone Numbers |
1,340 |
Mobile and computer phone numbers |
|
Financial Records |
182 |
Account numbers and details |
|
Voice Recordings |
261 |
Phone and conference calls |
|
Video Files |
89 |
Video sessions |
| General Objects | 17,209 | General graphic objects like logos and graphics |
Note on speech-to-text conversions.
Even though I captured several hours of conversation via open microphones and active chats sessions, I couldn’t accurately translate large parts of the content due to a limitation in Amazon’s, and Google’s transcribe and translation support for Nigerian and Gahanna dialects. In an operational deployment, this problem can be easily solved if a native language resource was available to review and translate the materials.
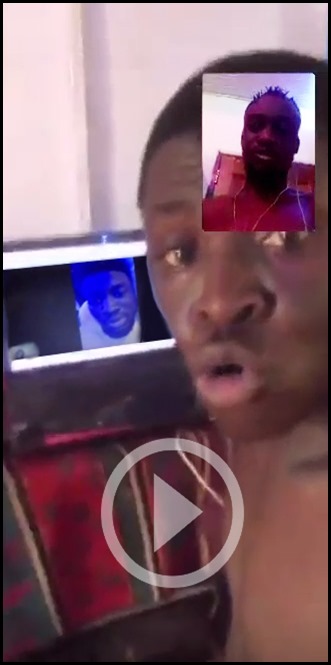
Image 13: Capturing a 3-way tech support Conference
Love is in the Air
It was time to get scammed. The first step was to create a fictitious person named Olga Schmatova and use her as bait. I didn’t want to use stock photographs because of their easy tractability or utilize a real person for obvious reasons, so I resorted to creating her images synthetically. I generated several photographs of Olga that accounted for age and weight variation. I then created the background information that supported her cover, such as a resume, biography, diplomas, online shopping profiles, employment history, and several other artifacts that would ensure that even an in-depth background search would yield valid results.


Image 14: AI-generated images of Olga Schmatova
Next, I created several social media, email, and dating site profiles and waited for the search engines to index her content. As soon as Olga started showing up in general internet searches, I was ready to go.
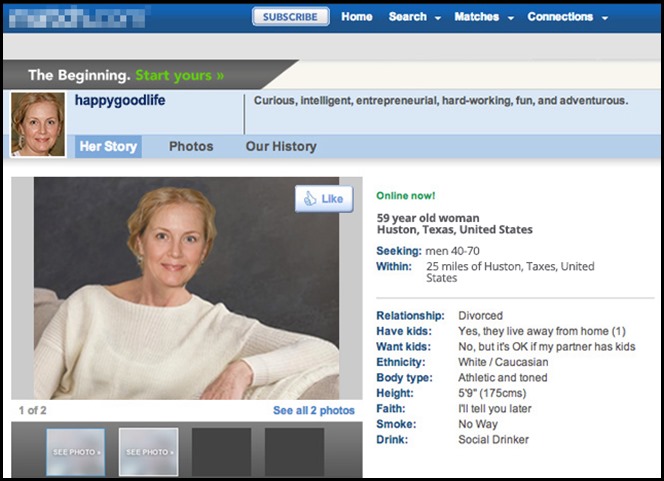
Image 15: One of Olga’s dating site profiles
Olga’s Dating Profile
My name is Olga. I am friendly, fun-loving, easy-going, and kind. My friends say that I bring a smile to the people around me. I consider myself balanced and calm, but I am also very energetic, active, and purposeful. I am full of positive energy, and I project it to others.
I work as an emergency room nurse. I am family-oriented and soft-spoken, but I am also a passionate and sensual woman with oceans of love in my heart, where we can swim together.
I like handmade art, visiting museums, cooking, and music, which is a significant relief.
Ideal Match Description
I want to find a man ready to accept my love and love me. I need stable and firm relations; I do not want to play with feelings or any drama. I would like to find a wealthy, mature, and wise man who is a doctor or a dentist who knows what he wants and can share some of his wisdom with me.
I didn’t have to wait long; within several days, I got the following hit:
Subject: Hello, My 110% Match
Message: Wow was the first thing I said when I went through your pictures/ profile and I wonder why a woman like you is still single. Perhaps, all the men around you are blind (lol)…
We can hook up and hopefully, be wonderful soul mates… A little about myself. Hmmm, I am easy going and kind. When people meet me, they sense it before long. I am a military doctor with the US Army, I love epic movies cos I love adventure, stories from ancient history and anything related to real life. I love the great outdoors, hiking, swimming, and travel.
I love family a lot! My favorite saying is “never look back”. Well, the only thing lagging in my life now is that lovely woman that will follow me to my dreamland. I believe ‘ONLY THOSE WHO SEEK, FIND’, and that is why I want to get to know you. I prefer direct email contact because of my deployment I don’t have access to this site at all times. Kindly email me on my gmail at the account at brandonrsmith2X@gmail.com or leave your email address. Sometimes, we are dumbfounded answering love related matters cos love is beyond human comprehension. I Hope to hear from u soon. Cheers!
Brandon
To make sure that this wasn’t a legitimate dating ping, I responded by asking Brandon for more personal details, to which, after several more emails and text exchanges, he eventually sent me an image of his fake military ID (image 16). From the recycled verbiage in his responses (matches for which the search spider found online), the poor grammar, typos, and the fake ID, I knew that I had found my scammer;
Subject: Dearest Olga,
Message: I’m just a normal guy who is searching for real love and wants to enjoy life to the fullest, I’m an american soldier.I come from a family of 4 which is me, dad, mum and my sister.I have my own house in Florida.We were living happily until my wife was diagnose of Cancer, it was a bad experience for me and my family it shattered us, my wife leaved with it for good 6 yrs before she gave up. It was a terrible experience but i just have to move on and hoping for the best. I have a daughter who I love dearly. My favorite color is blue (sky blue), Sunday is one of the day i don’t like , I lost my wife on Sunday so i don’t feel so much happiness on that day or maybe you can help me through that.
Been in the US Army for 5 years now as a surgeon. I enjoy my job but on deployment life is hard because you are restricted to do some things but I’m used to it. I love my job and I really need a family at the moment because I think we all deserve happiness in this life, My personality is outgoing and I have a good sense of humor. I am a kind and very tender hearted person. I am loving, in fact I sometimes think that I love too deeply when I love someone. I am a very honest person. I am too trusting at times and I am loyal to my companion and friends. i have a romantic heart and I like that. I want to be respected for being a man. I like to act, dress and look like a guy. i’m looking for a nice, honest,kind and caring woman, a woman that will love and be with me for the rest of my life. I’m not looking for someone to date but someone to spend the rest of my life with. All i need from her is just being sincere to me,make me feel secured,appreciate,love,care and being understanding. My recent life has been engulfed with misery and loneliness.
Everything in life happen for a reason, my being lonely for a very long time makes me want a companion and a woman to share my feelings with, I’m in search of a soul mate to spend the rest of our life together. No one is perfect and we could only give it a trial. Though it is right for us to learn from our mistakes. Which makes us resisting and having hard time trusting again in your life. A relationship is all about TRUST, SINCERITY and HONESTY, all this Paramount fact must exist in a relationship before anything can work out of it. Faith is the substance of things not seen, but the evidence of things being hoped for, lets strengthen our faith and see where this will lead us to. You are a beautiful woman and I want to get closer to you and see maybe this will work out for us.
Yours truly,
Brandon

Image 16: Brandon’s fake military ID with a scraped internet image of the Russian actor Oskar Ruchera.
Our romance lasted for about two weeks and included several exchanges of emails, voice, and text messages. I am not going to bother you with all of the details of the lengthy and steamy conversations that ensued. The skinny of it is that Brandon loved me and wanted to spend the rest of his life with me. We were going to get married in Indonesia and spend the honeymoon in Nusa Penida! All of this, of course, depended on him completing his “contract” combat deployment in Afghanistan in two years, where he served as a doctor.
Then came the con. Brandon said he could leave earlier and meet me in Indonesia, but he would have to pay the US Army an administration fee of about $20,000, which he didn’t have because all of his money was tied up in some high-tech investment in Google. He promised that if I helped him with this payment, he would repay me the money with interest in no time. I then received an email from williambdaniels1122@gmail.com, who claimed to be one Colonel William Daniels of the US Army HR team, requesting that I transfer these administrative fees to him via Western Union.
I didn’t have $20K on hand, so instead, I decided to give in to Brandon’s insistent requests for some intimate pictures of me. Following Ursula’s advice to the Little Mermaid that one should “…never underestimate the power of body language!” I sent Brandon several glamor shots of Olga. I also added some extra loving images to help take our relationship to the next level.



Image 17: Olga in a swimming suit and in and out of her little black dress.
Olga’s AI generated voice
After the first payload was deployed, the initial probe came back indicating that most machines on Brandon’s sizable local network were running Windows 7-8 and were unpatched. That was followed by several more payloads. I mapped his network and devices and started monitoring his internet traffic and messaging activity. Interestingly, Brandon and his team were somewhat security conscious as they were using dedicated machines for scamming and separate computers for banking and business operations and logistics. They were also careful to use burner phones for business communications and other phones for voice and internet browsing.
While taking inventory of the drives and storage media, I found a directory full of images that Brandon was using to assemble his social media profiles on what appeared to be a graphics editing machine. Surprisingly, it even had a licensed version of Adobe Creative Suite. As the VA spider was sifting through these images, it flagged two anomalies. The first was the OCR’d word “Verizon LTE” (Verizon doesn’t operate in Ghana), the second was a face match on two mobile phone screenshots of a FB page that contained the fake photos of Brandon and actual photos of two scammers (Image 18).
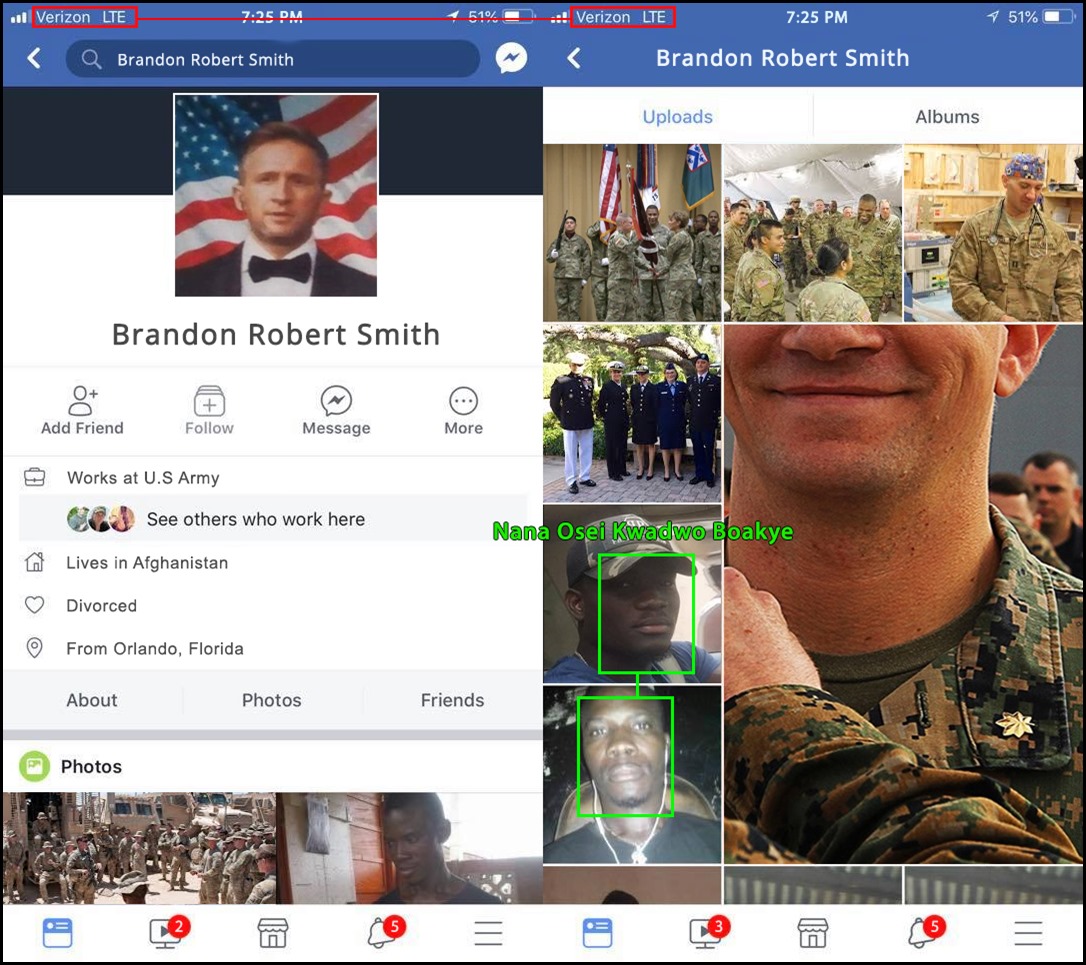
Image 18: Phone screenshots capture used for the network entry point.
Now that I had actual faces, the FR took over and traversed the photograph datasets on his storage devices and on his and his network’s on-line profiles and filled-in the matching names, addresses, phone numbers, car license plate, make, and car color (image 19). Altogether, the data collection took about 24 hours and involved some man-in-the-loop operations like the verification of anomalies and the termination of dead-end searches.
One interesting insight from the face recognition mapping is that Brandon and other individuals on his network use multiple ‘legal’ names and alternate spellings in official government documents such as drivers licenses and passports. Brandon, for example, was using the names “Nana Osei Kwadwo Boakye”, “Osei Kwadwo Boakye”, and “Osei Kwadwo”.

Image 19: Sample from over 150 license plates, car makes, and color details collected from the scammer network.
From the keystroke logs and login schedules, it was clear that multiple operators were involved as each exhibited distinctive ‘fist’ through Keystroke dynamics. Monitoring the login activity in real-time and screenshots confirmed that many of the operators shared the login details for their ‘bait’ profile.
The Scammer Enterprise and R&R
One surprising find was that the scammer operations used specialists. This makes sense because If one scammer had to carry out all of the work individually, it would take him years to develop the necessary cross-domain expertise. The substantial resource expenditure required to obtain the logistic and operational proficiency needed to support a massive scam campaign such as this would also be time-consuming and intellectually prohibitive. In the scammer community, members specialize according to their interests and talents; this allows them to more rapidly reach higher levels of productivity.
The person’s roles and responsibilities in the layered scammer enterprise depend on their ranking within the organizational structure. At the lowest level, there are the ‘factory workers’ who conduct their operations in teams of 5-15 individuals in internet cafes located in the suburbs and villages surrounding Lagos and Accra. Most don’t own their equipment and pay a fee for computing resources and internet access.
At the next level are the home-based operator ‘managers’ who own their equipment and manage several low-level teams. These managers are responsible for training, recruitment, mentoring, and operational support for the lower tiers.
The next level above them are the ‘supervisors’ who are responsible for maintaining proper ‘sales’ quotas, conversation rate, and logistics and the development of new scam products.
At the top of this pyramid are the kingpins who control several territories. They liaise with senior command of law enforcement, the military, media, and politicians and are considered to be the pillars of the community. They engage in wide-scale philanthropic activities such as sponsoring public works and charities.


Image 20: The opening of the new Wiamoase Police station in the Ashanti Region. Courtesy donation by Dr. Osei Kwame.
An interesting anomaly that was later confirmed to be a wide-scale trend was the frequent appearance of President Obama’s picture in many of the scammer workspace images (Image 21). Seventeen out of forty workspace images exhibited this trend. It turns out that BHO is considered to be the patron saint of the scammer industry in Nigeria and Ghana and is viewed as the ultimate scamming success story that everyone is trying to emulate.

Image 21: (L-R) Tier 3 scammers “KingKash” hard at work in the office and “Baron Osty” in a live session with a mark. Many scammers keep images of President Obama in their workspace and view him as the patron saint of the craft of the scam.
The Anatomy of a Scam
Based on the large volume of case data retrieved from the computers on Brandon’s network and the postmortem on these cases, it appears that many operators run hundreds of concurrent scams. In one example from January 2017- February 2018, a mid-level manager/supervisor named Asuaden Rich AKA “Goal Digger” (Image 22) operated over 105 simultaneous scams in the US alone with 40 of these scams paying over $630K USD. For these, “Goal Digger” assembled and used a library of over 300 stolen identities from Facebook and LinkedIn.
Between June 2018 and August 2018, Goal Digger spent on average 7 hours a day working 7 days a week, splitting his time between boarding new victims and maintaining active accounts.
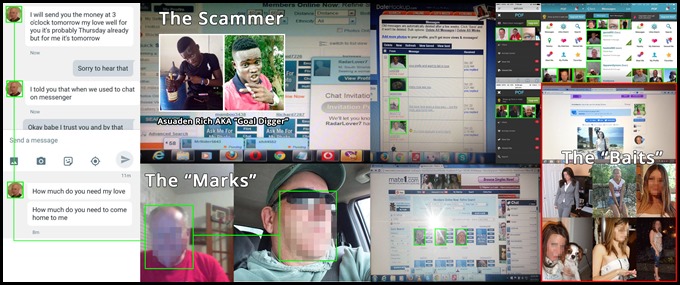
Image 22: An illustration of the scam details run by a the tier 2 scammer “Goal Digger”.
Money Makes the Scam Go Around
Since most victims are too embarrassed to report their ordeals, it is difficult to calculate the exact amount of money lost each year as a result of these scams. In 2013 the estimated figure was about $12.7 billion dollars. Adjusting for a modest 10% growth per year could bring it to 20 billion dollars. So, this industry makes more than the GDP of countries like Albania, Jamaica, and Afghanistan.
Just like in any other form of illegally generated revenue, the vast amounts of money that is collected from these scams must be laundered before the money can be used. In the case of the Nigerian and Ghanan networks, most of the placement, layering, and integration activity associated with money laundering took place locally via cash purchases of luxury goods, investment in large commercial and residential real estate developments, and the purchase of drugs, arms, and human trafficking. Additionally, in at least several instances, the scams were also financing Jihadi operations in Africa and overseas.

Image 23: An example of a UK-based courier service used by Brandon’s network for mailing goods and money laundering. The UK network is also affiliated with a local Stockton Jihadi mosque and recruitment center and a number of active Jihadists.
It is worth noting that local law enforcement and financial institutions are full participants in these ventures. The scammer networks also enjoy the full support of the local media. For example, the banks and money transfer/exchange organizations that service the scammers deliberately misplace the security cameras at the branches in order to avoid capturing the faces of the scammers. They also frequently purge their VMS systems and any internal records that contain the scammer’s national identification numbers, address, or other traceable PII data.

Image 24: Nana Kwadwo picking up the cash transferred via Western Union at the Ecobank branch near Medina Estate Gbagada Lagos. Camera field of view inside the teller does not capture the customer’s face. Cameras mounted on the branch ceiling only provide a rough view of customers.



Image 25: (L-R) Daily cash withdrawals, over $500K in freshly laundered money and weekly police and political payment bundles.

Image 26: Over a million dollars transported to Nigeria from Ghana via charted flight by a tier 1 scammer.
Scammers International
All of the Nigerian and Gahannan scammers networks examined show that they also maintain an international presence in many western countries like the US and Europe. These relationships are based on family members who either legally reside in the host country or arrive there on tourist visas. These relationships provide a home-based network with access to local organized crime for the purpose of local money laundering and goods transfer. For example, Brandon’s network included individuals in multiple cities in the US, England, Germany, Italy, Bulgaria, and France.
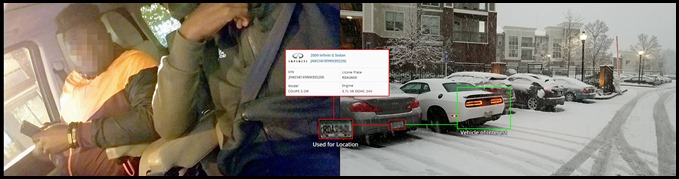
Image 27: One US node of the network.
Brandon’s network was also working closely with several local UN officials and aid organizations who either had their own or utilized UN and NGO trucks, planes, helicopters, and facilities to transport and store cash and drugs in and out of the country.
 Image 28: Osei Kwadwo Boakye, AKA Brandon Smith, and his domestic and international scammer network.
Image 28: Osei Kwadwo Boakye, AKA Brandon Smith, and his domestic and international scammer network.
The Derivative Economy
An interesting aspect of the scammer economy is its deep integration into the local marketplace. Many of the ‘manager’ and ‘supervisor’ level scammers eventually branch out and establish various legitimate businesses such as appliance and computer stores. The seed money and inventory for these ventures initially come from the scams. Still, eventually, as these ventures mature and develop a customer base and revenue traction, they switch and operate as legitimate businesses. In one illustrative example, a scammer named “Ruona Fundz” built a small retail empire of 6 electronic stores (Image 28), all managed and operated by his extended family.

Image 29: Reselling the loot, the electronics retail empire of “Ruona Fundz”.
Network Structure and Communications
All cybercrime networks depend on the contributions of a wide cast of professionals working in concert, including malware developers, scriptwriters, customer-facing operators, spammers, botnet masters, payment processors, IT, InfoSec, and finance. These communities require efficient and reliable methods to collaborate, communicate, and coordinate by sharing tips and tricks that help them defeat security measures and evade detection.
The stratified division of labor in the scammer networks allows actors to specialize in domains for which they have natural talent. This facilitates ‘personal growth’ and the achievement of the level of expertise in their particular area of specialization beyond what could be accomplished if they were responsible for all of the elements in the scam chain. Also, the acquisition of human talent is simplified because the professional barrier of entry is lower for newcomers. The recruits don’t have to spend significant time and money building the capacity themselves; they just have to purchase a starter kit and be productive immediately.
The traditional meeting place for cybercriminals used to be online messaging boards or web forums. There, scammers would get together, obtain support, buy technical tools like phishing kits and malware, and sell their illicit gains. Due to the effective shutdown of many of these sites by western law enforcement, this is no longer the case. This resulted in the wholesale migration of the scammer community to various peer-to-peer (P2P) messaging platforms.
The majority of the scammers on Brandon’s network utilized one or more of the following tools for their business communions:
- Skype
- Telegram
- Burner Phone Messaging
- Social Media Messaging
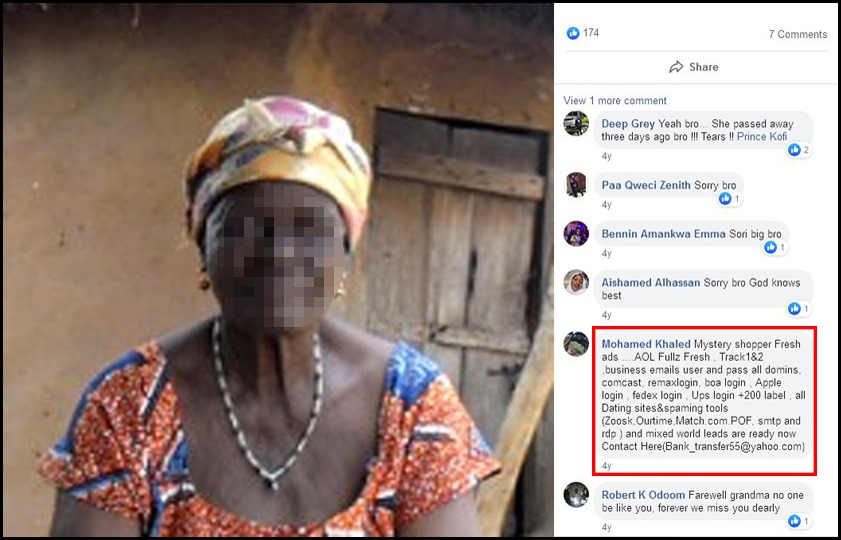
Image 30: Bogus postings of an obituary used for email, user ID, and password exchanges.
The Scammer InfoSec
Brandon’s network had a playbook for information security that included pointers on how to secure voice and data communicators (via encrypted channels like Skype and WhatsApp) and even advice on maintaining anonymity on social media. For example, some recommendations included best practices, such as:
- Using burner phones for all business exchanges. The burner phones are typically recycled every 3 months
- Obfuscating their car license plate numbers in images that they share on social media
- Always use aliases and never use their actual name in any online communication
- Obscuring the house number and street name in images uploaded to social media
- Recycle work computers once a year
- Not traveling internationally, especially in the US, with any ‘work’ equipment
- Disabling Geo-Tagging and GPS tracking on cell phones
Interestingly, most individuals in the network opted not to follow many of the InfoSec safeguards and precautions. In several cases, Ghana-based laptops showed up in Europe and the US. These exit nodes were not TOR-based, and they used local hotel and residential ISPs. In two examples, laptops that belonged to “Prince Pero” and “Halid The-General” were used for dating site scamming activity in Ghana, which beaconed an IP address in Marietta, GA, and Chicago, IL. From IP address history and use, it appears that their owners came to the US, traveled there for 2-4 weeks, and then headed back to Ghana, all the while continuing to scam their victims.

Image 31: Extensive use of burner phones for internal communications and coordination.

Image 32: An example of a car license plate obfuscation by scammers in order to prevent traceability on images posted to social media.
Summary of Findings
When I started the search, I only expected to identify a handful of enterprising individuals who ran these types of scams from an internet cafe or their basement. But I was wrong. I was taken aback by the sheer scale and sophistication of these operations and the amount of revenue they generate. It also became clear that these scams are not private operations that are run by enterprising individuals but rather a national industry that involves banking, law enforcement, the media, some UN bodies (mostly local), politicians, and local and international corporations across multiple jurisdictions.
Tracing the 1-degree operator network in the city of Madina in Ghana alone yielded over 10K individuals (total city population is about 132K) that were directly active in scamming. This represents about 7.5% of the total city population. A 2-degree linkage would triple this figure. If we account for a similar distribution across the whole of Ghana, we could potentially be looking at 15%-30% of the entire population working in or supporting scamming as a national industry. And these numbers don’t account for the impact that hundreds of millions of dollars have on Ghana’s overall economy and political structure. It is revealing that the official 2016 -Statistical-Report-Ministry-Of-Employment-and-Labor Ghana report completely ignores this phenomenon and fails to account for this market segment/industry as a major source of national revenue.
Most of the scammers identified in the analysis fit into a specific age and socio-economic cross sections. They are between 14-30 years old, and the majority have some high school education. Many had IT training through a local network of centers called IPMC. Only a handful have college degrees, and these are mostly supervisors. The majority of the member of the network come from the surrounding villages and towns around Accra, Abuja, and Lagos.
Scamming is a family business and is based on personal relationships; this is especially the case for the low-level operators. Many of them arrive to the city in search of fame and fortune from smaller villages and live in crowded rentals with as many as 5-10 per room.

Image 33: “Baron Norway” and his Tier-3 “Rich Boys” team chillin’ out.
The operations have a quasi-hierarchical and fluid structure that is based on tiers. These tiers are roughly divided to the low-level teams (tier-4-5) that work in the internet cafés (which are owned by the tier-1-2 operators). They are responsible for creating online profiles, generating leads, and maintaining constant cash flow. The tier-2-3 have management responsibilities and run multiple production facilities that can range from 10-50 tier 4-5 operators. They are responsible for recruitment, training, and meeting sales quotas. The tier-1 group sits at the top of the pyramid and manages multiple tier-2-3 managers. They finance the overall operations, provide political and security coverage, and collect the bulk of the revenue from their territories.

Image 34: The scammer tier hierarchy.
This tiered structure is, to a large degree, merit based and provides for constant upward mobility. In many ways it resembles a classic sales organization: the more you sell, the higher your commission is and the faster you move up to a more lucrative tier. It is not unusual to see a tier-5 operator move to tier-2 level in just a few years.

Image 35: From rags to riches in 4 easy steps. The Cinderella Success Story of “Goal Digger.”
The tier-1 operators only function in specific territories that are controlled by the police and politicians. They have strict “payment” responsibilities for their territory.

Image 36: Examples of some of the sweet rides owned by the tier-1 and 2 scammers. The cars are exclusively Mercedes, Lexus, Land Rover, or Porsche.
The revenue collection is controlled by a strict commission structure with every individual who is involved in the supply chain taking his cut based on the following rates per transaction.
|
Party |
Commission Per Transaction in Percent |
|
Bank |
~ 5 |
|
Military (if involved) |
~ 7 |
|
Police |
~ 10 |
|
Political Patronage |
~ 10 |
|
Tier 5 |
3 |
|
Tier 4 |
5 |
|
Tier 3 |
10 |
|
Tier 2 |
20 |
|
Tier 1 |
30 |
The police provide security services to protect the carriers and money as it’s transferred to various locations in the city. The police will also provide the scammers with additional for fee ‘anti-robbery’ protection to ensure that nonaffiliated gangs won’t whack them en route from and to the bank.
One illustrative case for this protective service (Image 37) is the altercation between police officer Frederick Amanor Godzi and Ms. Patience Osafo at the Midland bank branch in Ghana. The popular explanation for the beating she received was that she was at the bank trying to withdraw about $50 USD to buy some food for her baby grandchild and that the bank refused to give her the money. This led to an argument with the bank manager, who called the police. The policeman then proceeded to beat her up and kicked her out of the bank. However, the internal communications suggest that she was working as a lookout for an armed gang that was waiting nearby for scammers to come into the bank to withdraw large amounts of cash.


Image 37: Police beating at the Midland bank and “Crym Payys” and “Da General’s” doing the weekly cash runs.
After the initial public outcry that followed the posting of the violent video on social media, the court and the police ended up dismissing all charges against the policeman and the bank employees. The victim failed to appear in court to testify and cooperate with the police investigation. Ms. Osafo ended up getting a new luxury house as compensation, and the bank officials even released the following statement:
“We just closed a generous offer that removes her from the ‘kiosk’ to owning a brand new house and from the streets hawking toffees to now owning multiple bank accounts. “
Ironically, Ms. Osafo’s house, as well as several other developments in the Fettah Kakabra Top King estate, were funded by scammer investment money.
This form of collusion between politicians, justice officials, law enforcement, and the financial institutions where they ‘work things out privately’ seems to be the norm in scammer land and at least partially explains why these environments are so fertile in supporting the massive growth of the scamming industry.

Image 38: The main characters of the Midland Bank police beating saga.
Law Enforcement and Scamming
The police strictly enforce ‘permits’ to operate and the payment of commissions from the scammers by partnering with the money exchanges and financial institutions. For example, the security guards employed by the electronic payment vendors are also responsible for collecting a copy of each money transfer invoice that is cashed to ensure proper accounting of all payments. As can be seen from Image 39, the failure to pay or any attempts of cheating is dealt with promptly and severely.

Image 39: Money collection and the payment of ‘protection money’.
The payment to the scammers varies based on KPI such as closing rate, month to month performance, and seniority. The banks, police, and other facilitators such as the UN/NGOs, and politicians typically deduct their commissions at the teller. What is left is then distributed among the hierarchy on a weekly basis. The final form of payment can take different forms including cash (in local or foreign currency), drugs, or even gold bars.
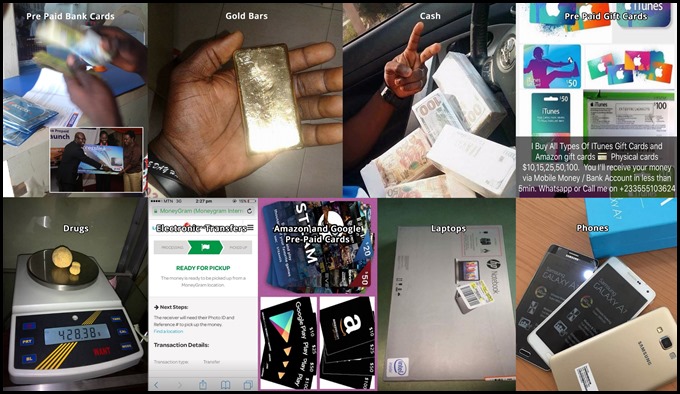
Image 40: Forms of payment include pre-paid bank cards (Access Bank), gold bars, cash, pre-paid cards, drugs, electronic funds transfer, pre-paid e-commerce cards, laptops, and phones.

Image 41: Example of large scale money laundering operations through investment in residential development projects in Ghana. The Qyarifa development, one of dozen such projects cleared over $12 million USD through the sale of units each going for $65K-$100K USD.

Image 42: International travel and coordination with local scammer teams. Global scammer networks are located in many major cities in the US, Europe, and Asia.

Image 43: “Crym Payys” at home piling up the cash and bling.
What can we do?
There is no silver bullet solution for keeping vulnerable individuals safe online. Still, there is a lot that we can do to strengthen our ability to disrupt and destroy the scammer networks. International cooperation is important in tackling this ever-growing form of cybercrime, but ultimately, it is important to remember that some UN personnel, diplomats, government policymakers, NGOs, politicians, media, and local law enforcement officials in the host countries are the largest financial beneficiaries of this industry and are themselves part of the problem.
As the data suggest, the solution to the scammer challenge is not to use more law enforcement to post-fact persecute the perpetrators but rather to preemptively disrupt and destroy these networks before they become operational or drain them financially once they are active. This is a classic feedback loop problem that every Western intelligence organization deals with daily. Even the scope of gathering, processing, and analyzing national security information from around the world fits in squarely with the capabilities and charter of agencies like the CIA and NSA, which already collect this type of intelligence and operate on it in similar environments internationally.
The public attitudes toward cyber scammers influences the way that government, law enforcement and commercial companies regard cybersecurity in general. If they think that the public does not perceive cyber scamming to be a serious threat to their personal wellbeing, then they won’t place a high priority on regulation, enforcement, and platform security.
Although history doesn’t repeat the same exact tune, it does tend to play the same scales over and over again. In 75 BCE, the 25-year-old Julius Caesar was sailing the Aegean Sea when he was kidnapped by Cilician pirates. According to Plutarch, the pirates asked for a hefty ransom for his release, and Caesar sent several of his friends to Rome to gather the silver, a task that took 38 days. Caesar told the pirates that after he was set free, he would hunt them down and hang them. Once he was freed, he made good on that promise: he quickly raised a fleet in Miletus and went right back to Pergamon, where he had been held captive. He captured the pirates and, as he promised, ordered that they be crucified.
The moral of the story is that cybercrime is the modern version of piracy, and the only effective way to deal with it is with diligence and force. The pirate infestation of the cost of Somalia shows what happens when these types of problems are not dealt with promptly. The current approach of trying to combat international online fraud by relying on international treaties, the Interpol, and UN resolutions amounts to little more than standing in a malaria-infested swamp and swatting at individual mosquitos.
We can all rest assured that there is no need for Caesar’s brutal form of punishment to solve this problem. Following these six easy steps is guaranteed to quickly drain the international scammer swamp:
- Place OFAC/Treasury sanctions against key cybercrime, political, UN, NGO, and law enforcement personnel involved in the scamming activity.
- Shut down the access of the cybercrime facilitating states to internet services like SWIFT, Airline Reservations System, etc., for several days/weeks as a warning.
- Start an international media campaign to inform the scammer sponsoring governments that their continues support for this industry would have severe consequences to their economy.
- Create and maintain a real-time database (using a framework such as demonstrated here) of all known scammers and arrest them when they attempt to travel internationally. The required bond for their release should be the total amount they scammed plus interest. That money should then be electronically transferred back to the victim’s accounts.
- Create a provision to allow victims to bring civil actions against dating sites and social media platforms that fail to vet users who turn out to be scammers.
- Bring RICO, mail and wire fraud, and money laundering charges against the C-level executives/board members of the US-based money transfer companies that are the lifeblood of these scams.
Finally, If you are reading this Captain Brandon, it was fun while it lasted, but I don’t think that this relationship is going to work out, it just wasn’t meant to be chéri.
Olga
References
The Disclosure–Intimacy Link in Computer Communication: Human Communication Research
Understanding Romance Fraud: Insights From Domestic Violence Research
Generating and Tuning Realistic Artificial Faces: ML-based face generation by Rani Horev
A Style-Based Generator Architecture for Generative Adversarial Networks: T. Karras NVIDIA
A Style-Based Generator Architecture for Generative Adversarial Networks: Cornell University
Generative Adversarial Networks: Cornell University
Sources for Online Romance Scams
Better Call Harry: Stolen Heart, Stolen Identity
This Army Veteran Became The Face Of Military Romance Scams. Now He’s Fighting Back
Brown County Browser: Don’t fall for veterans romance scams
Fake US Soldiers Robbing Women Online
How a billion-dollar Internet scam is breaking hearts and bank accounts
“Prince Charming” Behind Bars: Nigerian Romance Scammer Nets 27-Year Prison
Love a man in uniform? Online dating scammers hope so
Love me don’t: the West African online scam using U.S. Soldiers
Australian grandmother on drug ice charges in Malaysia: Maria Elvira Pinto Exposto may be a victim of a military romance scam
Copyright 2019 Yaacov Apelbaum, All Rights Reserved.


Brilliant as usual.
I think other web-site proprietors should take this web site as an model, very clean and great user friendly style and design, let alone the content. You are an expert in this topic!
All of this hard work, did you at least get their bank accounts?
Noblesse oblige
How can you find out your being scammed is there a web site you can cheak names
Sorry, I don’t know of a central scammer database.
Hello, i think im scam with a false soldier name cpt Davis from Florida, now in Yemen could you check for me if its real please, from a dating site , thank you
If you think it’s scam it’s likely a scam :-(
I won’t keep mute and will share my story to save a soul- my story started in 2016 where I met Sgt. Lee on a dating site and I was found in love until one day he said he has come across a box of gold and want to secretly sent to me for upkeep until he returns home I paid all cost but he was always given excuse for a request for money therefore my friend-Dave contacted the Embassy and it was confirmed scam and my case was reported to the Ghana Crime Unit(info.ghanapolice at consultant dot com) as his was traced to Ghana and luckily the perpetrators was brought to justice! Beware of scam and if any office asks for money then it’s a scam.
I am in the process of this now the person is portraying one of the Soldiers in the box at the top of the page James is on his pocket, they say he is Sergent Major James Douglas. He has told me he loves me and of course I gave him my info of my life and family but no names there thank God. I have not exchanged any money but they sure are wanting it.
Glad you found the post useful Karen :-)
I have a picture of a young man from Ghana who scammed me. It appears you have an immense data file. Can you do reverse imaging to find this scammer?
Also, why hasn’t the FTC hired you to run an agency to investigate romance scams. Romance scams are the leading type of fraud in the USA surpassing bank and health care fraud.
Hi Sheryl,
The “Military Romantic Scams – The Theory and Practice” is an old project (published 3 years ago). Sorry, I didn’t keep any of the data-files and I dismantled the solutions after the project was complete. You can try and reverse lookup the image via Google image search yourself. If you were scammed for a large amount of money, I suggest that you also file a police report.
It’s very kind of you to suggest that the FTC should hire me to run an anti-scam agency, but, the good people at the FTC, just like their sister federal agencies in the DOJ, SS, Intel, treasury, etc., are too busy planning their career in the private sector.