I recently received an email claiming to be from Microsoft Live. The email stated that due to some processing issues, they could not authorize my credit card and so I would need to login to their website to update my credit card information by clicking on their link.
Over the years, I have seen a number of these types of messages, but this was the first one targeting me personally. After skimming through it, I realized that it was a blatant phishing attempt, nevertheless, I still marveled at the ingenuity of the scammers.
Billing and Account Management
Dear Windows Live Hotmail member,
During our regularly scheduled account maintenance and verification procedures, our billing department was unable to authorize your current payment method information.
This might be due to either of the following reasons:
A recent change in your personal information (i.e. change of address, credit card)
Submitting invalid information during the initial Sign Up or upgrade process.
An inability to accurately verify your selected payment method information due to an internal error within our processors.
Please use the following link to update your payment method information :
http://billing.microsoft.com/logon.srf?action=SignIn&reason=auth&type=auto&uid=187&acct=49472101102
The above link may have been blocked for your privacy. To activate the link please look for the Show content link that is usually located on top of this message.
NOTE! If your account information is not updated within 48 hours then your ability to use your Windows Live Hotmail account will become restricted.
Thank you for using Windows Live Hotmail!
Please do not reply to this e-mail, as this is an unmonitored alias.
© 2009 Microsoft Corporation. All rights reserved.
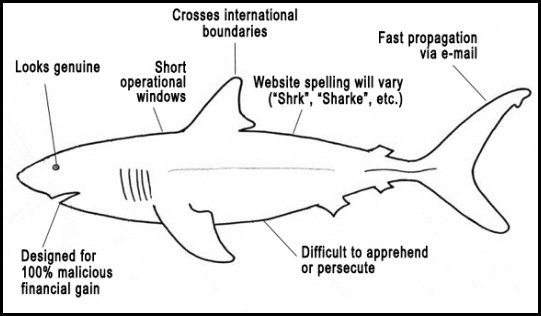
For the uninitiated, phishing (pronounced “fishing”) is a fraudulent attempt to acquire sensitive information from a user. Such information can be: credit cards, user IDs, passwords, and/or account information. It is often accomplished via email or phone.
Phishing falls into the category of exploits known as “social engineering”. Even though they are mostly low tech, (requiring neither sophisticated technology nor advanced programming), they can to be successful (especially the well executed and new exploits) because most people tend instinctively to do what they are told and will not challenge the authority and authenticity of what seems to be an official correspondence.
In a typical phishing scenario, the perpetrators (usually located offshore) send a simple email—claiming to be from the customer service department of a recognizable organization (like a bank, online service, etc.)—the email will inform you of some problem with your account. You are then instructed to provide details of your bank, email, or credit card account in order to correct this problem.
Even though phishing exploits can have many variations, they can be grouped into the following five usage scenarios:
- Forged identities — In this exploit, the attacker creates an email address that is related to a reputable organization like “Windows Live Customer Support”. Even though on the surface, their email address looks legitimate (as in: billing@windowslive.com), it is not. If you’re not paying attention, it can be easy to mistake a message like this for a genuine customer support request.
- Compromised accounts — In this exploit, the attacker uses a compromised user account to send an email to everyone in the address book for that account. An email you receive from a known account dramatically increases the credibility of that message and, therefore, the likelihood of a successful phishing attack.
- Direct phone calls — In this exploit, the scammer may contact you directly by phone, telling you that they work for some financial institution (may offer to lower your interest rates) or the fraud investigation departments. They will inform you that your account has been breached and will directly ask you for your account details in order to verify it.
- Bogus websites — In this exploit, the attacker will send you a link to what seems to be a functional website. The site will include official-looking logos, language, or other identifying information taken directly from a legitimate website. The site’s address will resemble the name of a reputable company but with some spelling variations. For example, the name”microsoft.live.com” could appear instead as: “micorsoft.live.com”
- Social Network Harvesting—In this exploit, a scammer will ask you for personal information in a communication. You may mistake it for an email from a friend wanting to reconnect. The email will include convincing details about your personal life recovered from social networks such as LinkedIn, Facebook, etc.
In general, the objective of phishing is to recover your webmail credentials since the resale value of a legitimate webmail account on the black market can be as high as $2-$3—twice the amount they could get for a stolen credit card number. So, for a phisher, breaching several dozen accounts a day can be a lucrative business, making $100K—$500K for the life of the scam.
In the case of my phishing email, when I followed the link in it, I was taken to a credit card entry form (Image 1). As I expected, the form looked genuine; it had all the right corporate trimmings: a Microsoft logo, copyright notice, and even a link to a help page (which ironically offered the following advice: “You should keep this number secret, protect it, and never write it on your card.”)
Image 1: Phishing Credit Card Entry Form
As with most phishing sites, I was expecting to find some bogus or misspelled Microsoft URL, but instead, I was surprised to see that the web address of the webpage belonged to a company called Human & Technology H&T (Image 2). Htech21.com doesn’t even sound like Microsoft. I’ve checked the parent URL, and it turns out that this company was, at one point, a legitimate Korean hardware manufacturer. Then, two years ago, their CEO was arrested, and the company became the target of one of the largesat class-action lawsuits in history.
It is also interesting to note, that the site’s help file focused on ATMs (Automated Teller Machines), strongly suggests that at least some of the phishing website contents have also been used in other scams.
Image 2: Phishing Host Website
It is hard to recognize legitimate customer service communications from phishing expeditions. This difficulty is further compounded by the fact that, for many, using services such as Amazon, eBay, and e-banking has now become a way of life. For most users, the potential inconvenience of being looked out of their favorite online services outweighs the risk of disclosing their account information. Unfortunately, online services are not helping in this situation either because most are impossible to reach by phone or because their offshore support centers are mainly useless.
So, how does one survive in the hostile jungle of email exploits? The following are my top 10 Do’s and Don’ts of email:
- Do Not open emails that have a wrong or incorrect spelling of your name. Phishers often harvest email addresses in balk and may not have your full name. Because of this, they will try to guess your name from your email address.
- Do Not open emails that are not addressed to you by name. Phishers will almost never personalize correspondences; they will refer to you as “Dear Customer” or “Dear Valued Customer” because they send balk solicitations to millions of email addresses.
- Do Not respond to any account management email requests that come from your bank. If your bank needs to reach you, they will send you an official letter or leave you a voicemail with a valid callback telephone number.
- Do Not open unsolicited emails. Nothing in life is free; this includes the invitation to view naked celebrities and the Prozac and Viagra offer in your inbox.
- Do Not use email links to go to any financial websites. Type in the URL yourself and save it as a bookmark.
- Do verify the website URL you are about to log into, check the spelling carefully before you provide your login details on any web page. Pay close attention to domain name following the “http://” section of the address. Many phishers will Intentionally create very long names to obfuscate the fake URL.
- Do log in to your on-line accounts regularly and look for unrecognized transactions. Do the same with your monthly credit card statements.
- Do Not send your account details via email to anyone. email traffic is unencrypted, so anyone on route can intercept the message.
- Do check that the Internet connection you are using is secure. Look for HTTPS in the address field of your browser. You may also want to click on the
- Do make sure that you have updated anti-virus software and that your firewall is turned on.
© Copyright 2009 Yaacov Apelbaum All Rights Reserved.